★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GCIH Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GCIH-dumps.html
Actualtests offers free demo for GCIH exam. "GIAC Certified Incident Handler", also known as GCIH exam, is a GIAC Certification. This set of posts, Passing the GIAC GCIH exam, will help you answer those questions. The GCIH Questions & Answers covers all the knowledge points of the real exam. 100% real GIAC GCIH exams and revised by experts!
Also have GCIH free dumps questions for you:
NEW QUESTION 1
You want to connect to your friend's computer and run a Trojan on it. Which of the following tools will you use to accomplish the task?
- A. PSExec
- B. Remoxec
- C. Hk.exe
- D. GetAdmin.exe
Answer: A
NEW QUESTION 2
Which of the following is the best method of accurately identifying the services running on a victim host?
- A. Use of the manual method of telnet to each of the open ports.
- B. Use of a port scanner to scan each port to confirm the services running.
- C. Use of hit and trial method to guess the services and ports of the victim host.
- D. Use of a vulnerability scanner to try to probe each port to verify which service is running.
Answer: A
NEW QUESTION 3
Which of the following controls is described in the statement given below?
"It ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. It secures information by assigning sensitivity labels on information and comparing this to the level of security a user is operating at."
- A. Role-based Access Control
- B. Attribute-based Access Control
- C. Discretionary Access Control
- D. Mandatory Access Control
Answer: D
NEW QUESTION 4
Which of the following attacks allows an attacker to sniff data frames on a local area network (LAN) or stop the traffic altogether?
- A. Port scanning
- B. ARP spoofing
- C. Man-in-the-middle
- D. Session hijacking
Answer: B
NEW QUESTION 5
Which of the following types of malware can an antivirus application disable and destroy?
Each correct answer represents a complete solution. Choose all that apply.
- A. Rootkit
- B. Trojan
- C. Crimeware
- D. Worm
- E. Adware
- F. Virus
Answer: ABDF
NEW QUESTION 6
Which of the following statements are true about netcat?
Each correct answer represents a complete solution. Choose all that apply.
- A. It provides special tunneling, such as UDP to TCP, with the possibility of specifying all network parameters.
- B. It can be used as a file transfer solution.
- C. It provides outbound and inbound connections for TCP and UDP ports.
- D. The nc -z command can be used to redirect stdin/stdout from a program.
Answer: ABC
NEW QUESTION 7
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He establishes a connection to a target host running a Web service with netcat and sends a bad html request in order to retrieve information about the service on the host.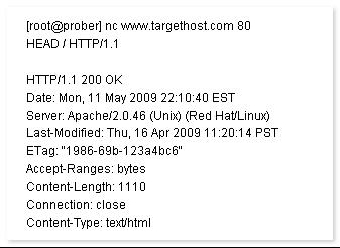
Which of the following attacks is John using?
- A. Sniffing
- B. Eavesdropping
- C. War driving
- D. Banner grabbing
Answer: D
NEW QUESTION 8
Which of the following is a technique for creating Internet maps?
Each correct answer represents a complete solution. Choose two.
- A. Active Probing
- B. AS PATH Inference
- C. Object Relational Mapping
- D. Network Quota
Answer: AB
NEW QUESTION 9
Which of the following tools is used for port scanning?
- A. NSLOOKUP
- B. NETSH
- C. Nmap
- D. L0phtcrack
Answer: C
NEW QUESTION 10
Victor wants to send an encrypted message to his friend. He is using certain steganography technique to accomplish this task. He takes a cover object and changes it accordingly to hide information. This secret information is recovered only when the algorithm compares the changed cover with the original cover.
Which of the following Steganography methods is Victor using to accomplish the task?
- A. The distortion technique
- B. The spread spectrum technique
- C. The substitution technique
- D. The cover generation technique
Answer: A
NEW QUESTION 11
Which of the following tasks can be performed by using netcat utility?
Each correct answer represents a complete solution. Choose all that apply.
- A. Checking file integrity
- B. Creating a Backdoor
- C. Firewall testing
- D. Port scanning and service identification
Answer: BCD
NEW QUESTION 12
Which of the following types of skills are required in the members of an incident handling team?
Each correct answer represents a complete solution. Choose all that apply.
- A. Organizational skills
- B. Diplomatic skills
- C. Methodical skills
- D. Technical skills
Answer: ABD
NEW QUESTION 13
When you conduct the XMAS scanning using Nmap, you find that most of the ports scanned do not give a response. What can be the state of these ports?
- A. Filtered
- B. Open
- C. Closed
Answer: B
NEW QUESTION 14
In which of the following steps of the incident handling processes does the Incident Handler make sure that all business processes and functions are back to normal and then also wants to monitor the system or processes to ensure that the system is not compromised again?
- A. Eradication
- B. Lesson Learned
- C. Recovery
- D. Containment
Answer: C
NEW QUESTION 15
Alice wants to prove her identity to Bob. Bob requests her password as proof of identity, which Alice dutifully provides (possibly after some transformation like a hash function); meanwhile, Eve is eavesdropping the conversation and keeps the password. After the interchange is over, Eve connects to Bob posing as Alice; when asked for a proof of identity, Eve sends Alice's password read from the last session, which Bob accepts. Which of the following attacks is being used by Eve?
- A. Replay
- B. Firewalking
- C. Session fixation
- D. Cross site scripting
Answer: A
NEW QUESTION 16
John is a malicious attacker. He illegally accesses the server of We-are-secure Inc. He then places a backdoor in the We-are-secure server and alters its log files. Which of the following steps of malicious hacking includes altering the server log files?
- A. Maintaining access
- B. Covering tracks
- C. Gaining access
- D. Reconnaissance
Answer: B
NEW QUESTION 17
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the company for personal reasons. He wants to send out some secret information of the company. To do so, he takes an image file and simply uses a tool image hide and embeds the secret file within an image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using the image file to send the data, the mail server of his company is unable to filter this mail. Which of the following techniques is he performing to accomplish his task?
- A. Email spoofing
- B. Steganography
- C. Web ripping
- D. Social engineering
Answer: B
NEW QUESTION 18
Which of the following types of attacks is only intended to make a computer resource unavailable to its users?
- A. Denial of Service attack
- B. Replay attack
- C. Teardrop attack
- D. Land attack
Answer: A
NEW QUESTION 19
......
P.S. Allfreedumps.com now are offering 100% pass ensure GCIH dumps! All GCIH exam questions have been updated with correct answers: https://www.allfreedumps.com/GCIH-dumps.html (328 New Questions)