★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GCIH Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GCIH-dumps.html
we provide Practical GIAC GCIH free question which are the best for clearing GCIH test, and to get certified by GIAC GIAC Certified Incident Handler. The GCIH Questions & Answers covers all the knowledge points of the real GCIH exam. Crack your GIAC GCIH Exam with latest dumps, guaranteed!
Free demo questions for GIAC GCIH Exam Dumps Below:
NEW QUESTION 1
Smoothening and decreasing contrast by averaging the pixels of the area where significant color transitions occurs.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 2
Which of the following tools is an automated tool that is used to implement SQL injections and to retrieve data from Web server databases?
- A. Fragroute
- B. Absinthe
- C. Stick
- D. ADMutate
Answer: B
NEW QUESTION 3
Adam works as a Security Administrator for Umbrella Technology Inc. He reported a breach in security to his senior members, stating that "security defenses has been breached and exploited for 2 weeks by hackers." The hackers had accessed and downloaded 50,000 addresses containing customer credit cards and passwords. Umbrella Technology was looking to law enforcement officials to protect their intellectual property.
The intruder entered through an employee's home machine, which was connected to Umbrella Technology's corporate VPN network. The application called BEAST Trojan was used in the attack to open a "back door" allowing the hackers undetected access. The security breach was discovered when customers complained about the usage of their credit cards without their knowledge.
The hackers were traced back to Shanghai, China through e-mail address evidence. The credit card information was sent to that same e-mail address. The passwords allowed the hackers to access Umbrella Technology's network from a remote location, posing as employees.
Which of the following actions can Adam perform to prevent such attacks from occurring in future?
- A. Allow VPN access but replace the standard authentication with biometric authentication
- B. Replace the VPN access with dial-up modem access to the company's network
- C. Disable VPN access to all employees of the company from home machines
- D. Apply different security policy to make passwords of employees more complex
Answer: C
NEW QUESTION 4
Which of the following tools are used as a network traffic monitoring tool in the Linux operating system?
Each correct answer represents a complete solution. Choose all that apply.
- A. Netbus
- B. IPTraf
- C. MRTG
- D. Ntop
Answer: BCD
NEW QUESTION 5
Which of the following is used by attackers to obtain an authenticated connection on a network?
- A. Denial-of-Service (DoS) attack
- B. Replay attack
- C. Man-in-the-middle attack
- D. Back door
Answer: B
NEW QUESTION 6
Which of the following tools can be used for steganography?
Each correct answer represents a complete solution. Choose all that apply.
- A. Image hide
- B. Stegbreak
- C. Snow.exe
- D. Anti-x
Answer: AC
NEW QUESTION 7
Choose the items from the given list that are required to be in the response kit of an Incident Handler.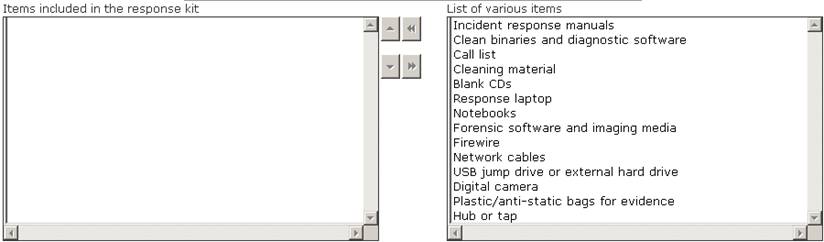
Solution:
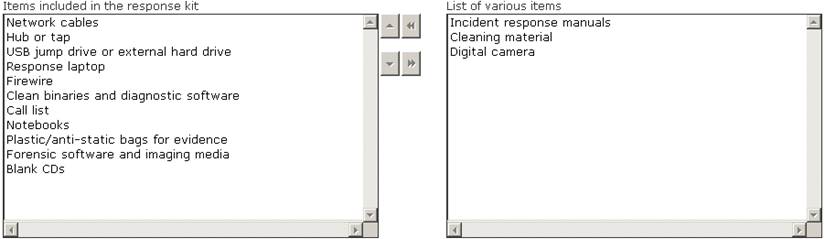
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
Which of the following attacks involves multiple compromised systems to attack a single target?
- A. Brute force attack
- B. Replay attack
- C. Dictionary attack
- D. DDoS attack
Answer: D
NEW QUESTION 9
Which of the following statements about threats are true?
Each correct answer represents a complete solution. Choose all that apply.
- A. A threat is a weakness or lack of safeguard that can be exploited by vulnerability, thus causing harm to the information systems or networks.
- B. A threat is a potential for violation of security which exists when there is a circumstance, capability, action, or event that could breach security and cause harm.
- C. A threat is a sequence of circumstances and events that allows a human or other agent to cause an information-related misfortune by exploiting vulnerability in an IT product.
- D. A threat is any circumstance or event with the potential of causing harm to a system in the form of destruction, disclosure, modification of data, or denial of service.
Answer: BCD
NEW QUESTION 10
Which of the following is the method of hiding data within another media type such as graphic or document?
- A. Spoofing
- B. Steganography
- C. Packet sniffing
- D. Cryptanalysis
Answer: B
NEW QUESTION 11
Which of the following steps of incident response is steady in nature?
- A. Containment
- B. Eradication
- C. Preparation
- D. Recovery
Answer: C
NEW QUESTION 12
You run the following PHP script:
<?php $name = mysql_real_escape_string($_POST["name"]);
$password = mysql_real_escape_string($_POST["password"]); ?>
What is the use of the mysql_real_escape_string() function in the above script.
Each correct answer represents a complete solution. Choose all that apply.
- A. It can be used to mitigate a cross site scripting attack.
- B. It can be used as a countermeasure against a SQL injection attack.
- C. It escapes all special characters from strings $_POST["name"] and $_POST["password"] except ' and ".
- D. It escapes all special characters from strings $_POST["name"] and $_POST["password"].
Answer: BD
NEW QUESTION 13
Which of the following are open-source vulnerability scanners?
- A. Nessus
- B. Hackbot
- C. NetRecon
- D. Nikto
Answer: ABD
NEW QUESTION 14
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Each correct answer represents a complete solution. Choose all that apply.
- A. Host
- B. Dig
- C. DSniff
- D. NSLookup
Answer: ABD
NEW QUESTION 15
John works as a C programmer. He develops the following C program:
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
int buffer(char *str) {
char buffer1[10];
strcpy(buffer1, str);
return 1;
}
int main(int argc, char *argv[]) {
buffer (argv[1]);
printf("Executed\n");
return 1;
}
His program is vulnerable to a __________ attack.
- A. SQL injection
- B. Denial-of-Service
- C. Buffer overflow
- D. Cross site scripting
Answer: C
NEW QUESTION 16
Which of the following DoS attacks affects mostly Windows computers by sending corrupt UDP packets?
- A. Fraggle
- B. Ping flood
- C. Bonk
- D. Smurf
Answer: C
NEW QUESTION 17
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
- A. Post-attack phase
- B. On-attack phase
- C. Attack phase
- D. Pre-attack phase
Answer: D
NEW QUESTION 18
You are the Administrator for a corporate network. You are concerned about denial of service attacks.
Which of the following would be the most help against Denial of Service (DOS) attacks?
- A. Packet filtering firewall
- B. Network surveys.
- C. Honey pot
- D. Stateful Packet Inspection (SPI) firewall
Answer: D
NEW QUESTION 19
......
P.S. Dumps-files.com now are offering 100% pass ensure GCIH dumps! All GCIH exam questions have been updated with correct answers: https://www.dumps-files.com/files/GCIH/ (328 New Questions)