★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW SY0-701 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/SY0-701-dumps.html
we provide Refined CompTIA SY0-701 exam guide which are the best for clearing SY0-701 test, and to get certified by CompTIA CompTIA Security+ Exam. The SY0-701 Questions & Answers covers all the knowledge points of the real SY0-701 exam. Crack your CompTIA SY0-701 Exam with latest dumps, guaranteed!
Online CompTIA SY0-701 free dumps demo Below:
NEW QUESTION 1
A security operations center wants to implement a solution that can execute files to test for malicious activity. The solution should provide a report of the files' activity against known threats.
Which of the following should the security operations center implement?
- A. theHarvester
- B. Nessus
- C. Cuckoo
- D. Sn1per
Answer: C
Explanation:
Cuckoo is a sandbox that is specifically written to run programs inside and identify any malware. A sandbox is a virtualized environment that isolates the program from the rest of the system and monitors its behavior. Cuckoo can analyze files of various types, such as executables, documents, URLs, and more. Cuckoo can provide a report of the files’ activity against known threats, such as network traffic, file operations, registry changes, API calls, and so on.
A security operations center can implement Cuckoo to execute files to test for malicious activity and generate a report of the analysis. Cuckoo can help the security operations center to detect and prevent malware infections, investigate incidents, and perform threat intelligence.
NEW QUESTION 2
A security analyst reviews a company’s authentication logs and notices multiple authentication failures. The authentication failures are from different usernames that share the same source IP address. Which of the password attacks is MOST likely happening?
- A. Dictionary
- B. Rainbow table
- C. Spraying
- D. Brute-force
Answer: C
Explanation:
Detailed
Password spraying is an attack where an attacker tries a small number of commonly used passwords against a large number of usernames. The goal of password spraying is to avoid detection by avoiding too many failed login attempts for any one user account. The fact that different usernames are being attacked from the same IP address is a strong indication that a password spraying attack is underway.
NEW QUESTION 3
A security incident has been resolved Which of the following BEST describes the importance of the final phase of the incident response plan?
- A. It examines and documents how well the team responded discovers what caused the incident, and determines how the incident can be avoided in the future
- B. It returns the affected systems back into production once systems have been fully patched, data restored and vulnerabilities addressed
- C. It identifies the incident and the scope of the breach how it affects the production environment, and the ingress point
- D. It contains the affected systems and disconnects them from the network, preventing further spread of the attack or breach
Answer: A
Explanation:
The final phase of an incident response plan is the post-incident activity, which involves examining and documenting how well the team responded, discovering what caused the incident, and determining how the incident can be avoided in the future. References: CompTIA Security+ Certification Exam Objectives - 2.5 Given a scenario, analyze potential indicators to determine the type of attack. Study Guide: Chapter 5, page 225.
NEW QUESTION 4
A security analyst notices several attacks are being blocked by the NIPS but does not see anything on the boundary firewall logs. The attack seems to have been thwarted Which of the following resiliency techniques was applied to the network to prevent this attack?
- A. NIC Teaming
- B. Port mirroring
- C. Defense in depth
- D. High availability
- E. Geographic dispersal
Answer: C
Explanation:
Defense in depth is a resiliency technique that involves implementing multiple layers of security controls to protect against different types of threats. In this scenario, the NIPS likely provided protection at a different layer than the boundary firewall, demonstrating the effectiveness of defense in depth. References: CompTIA Security+ Certification Exam Objectives (SY0-601)
NEW QUESTION 5
An organization is repairing the damage after an incident. Which of the following controls is being implemented?
- A. Detective
- B. Preventive
- C. Corrective
- D. Compensating
Answer: C
Explanation:
A corrective control is a type of security control that is designed to mitigate the damage caused by a security incident or to restore the normal operations after an incident. A corrective control can include actions such as restoring from backups, applying patches, isolating infected systems, or implementing new policies and procedures. A corrective control is different from a preventive control, which aims to stop an incident from happening, or a detective control, which aims to identify and record an incident. References: https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/security-controls-3/
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/security-controls-3/  https://www.oreilly.com/library/view/comptia-security-all-in-one/9781260464016/ch31.xhtml
https://www.oreilly.com/library/view/comptia-security-all-in-one/9781260464016/ch31.xhtml  https://www.professormesser.com/security-plus/sy0-501/security-controls-2/
https://www.professormesser.com/security-plus/sy0-501/security-controls-2/
NEW QUESTION 6
An attacker replaces a digitally signed document with another version that goes unnoticed Upon reviewing the document's contents the author notices some additional verbiage that was not originally in the document but cannot validate an integrity issue. Which of the following attacks was used?
- A. Cryptomalware
- B. Hash substitution
- C. Collision
- D. Phishing
Answer: B
Explanation:
This type of attack occurs when an attacker replaces a digitally signed document with another version that has a different hash value. The author would be able to notice the additional verbiage, however, since the hash value would have changed, they would not be able to validate an integrity issue.
NEW QUESTION 7
An information security manager for an organization is completing a PCI DSS self-assessment for the first time. which of the is following MOST likely reason for this type of assessment?
- A. An international expansion project is currently underway.
- B. Outside consultants utilize this tool to measure security maturity.
- C. The organization is expecting to process credit card information.
- D. A government regulator has requested this audit to be completed
Answer: C
Explanation:
PCI DSS (Payment Card Industry Data Security Standard) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Any organization that accepts credit card payments is required to comply with PCI DSS.
NEW QUESTION 8
An organization is concerned about hackers potentially entering a facility and plugging in a remotely accessible Kali Linux box. Which of the following should be the first lines of defense against such an attack? (Select TWO).
- A. MAC filtering
- B. Zero trust segmentation
- C. Network access control
- D. Access control vestibules
- E. Guards
- F. Bollards.
Answer: AC
Explanation:
MAC filtering is a method of allowing or denying access to a network based on the MAC address of the device attempting to connect. By creating a list of approved MAC addresses, the organization can prevent unauthorized devices from connecting to the network.
Network Access Control (NAC) is a security solution that allows organizations to restrict access to their networks based on the device's identity, configuration, and security posture. This can be used to ensure that only legitimate devices are allowed to connect to the network, and any unauthorized devices are blocked.
NEW QUESTION 9
A security administrator needs to add fault tolerance and load balancing to the connection from the file server to the backup storage. Which of the following is the best choice to achieve this objective?
- A. Multipathing
- B. RAID
- C. Segmentation
- D. 8021.1
Answer: A
Explanation:
to achieve the objective of adding fault tolerance and load balancing to the connection from the file server to the backup storage is multipathin1g. Multipathing is a technique that allows a system to use more than one path to access a storage device1. This can improve performance by distributing the workload across multiple paths, and also provide fault tolerance by switching to an alternative path if one path fails1. Multipathing can be implemented using software or hardware solutions1.
NEW QUESTION 10
A security analyst is investigating multiple hosts that are communicating to external IP addresses during the hours of 2:00 a.m - 4:00 am. The malware has evaded detection by traditional antivirus software. Which of the following types of malware is MOST likely infecting the hosts?
- A. A RAT
- B. Ransomware
- C. Polymophic
- D. A worm
Answer: A
Explanation:
Based on the given information, the most likely type of malware infecting the hosts is a RAT (Remote Access Trojan). RATs are often used for stealthy unauthorized access to a victim's computer, and they can evade traditional antivirus software through various sophisticated techniques. In particular, the fact that the malware is communicating with external IP addresses during specific hours suggests that it may be under the control of an attacker who is issuing commands from a remote location. Ransomware, polymorphic malware, and worms are also possible culprits, but the context of the question suggests that a RAT is the most likely answer.
NEW QUESTION 11
A financial institution would like to store its customer data in the cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution Is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would best meet the requirement?
- A. Asymmetric
- B. Symmetric
- C. Homomorphic
- D. Ephemeral
Answer: C
Explanation:
Homomorphic encryption is a cryptographic technique that allows data to be stored, accessed and manipulated while encrypted. Homomorphic encryption enables computations to be performed on ciphertexts, generating an encrypted result that, when decrypted, matches the result of the operations as if they had been performed on the plaintext. Homomorphic encryption can prevent the cloud service provider from being able to decipher the data due to its sensitivity, as the data remains encrypted at all times. Homomorphic encryption is not concerned about computational overheads and slow speeds, as it trades off performance for security and privacy. References: https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/cryptography-concepts-2/
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/cryptography-concepts-2/ https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/symmetric-and-asymmetric-crypt
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/symmetric-and-asymmetric-crypt
NEW QUESTION 12
A company is implementing a new SIEM to log and send alerts whenever malicious activity is blocked by its antivirus and web content filters. Which of the following is the primary use case for this scenario?
- A. Implementation of preventive controls
- B. Implementation of detective controls
- C. Implementation of deterrent controls
- D. Implementation of corrective controls
Answer: B
Explanation:
A Security Information and Event Management (SIEM) system is a tool that collects and analyzes
security-related data from various sources to detect and respond to security incidents. References: CompTIA Security+ Study Guide 601, Chapter 5
NEW QUESTION 13
A security administrator is managing administrative access to sensitive systems with the following requirements:
• Common login accounts must not be used for administrative duties.
• Administrative accounts must be temporal in nature.
• Each administrative account must be assigned to one specific user.
• Accounts must have complex passwords.
" Audit trails and logging must be enabled on all systems.
Which of the following solutions should the administrator deploy to meet these requirements? (Give explanation and References from CompTIA Security+ SY0-601 Official Text Book and Resources)
- A. ABAC
- B. SAML
- C. PAM
- D. CASB
Answer: C
Explanation:
PAM is a solution that enables organizations to securely manage users' accounts and access to sensitive systems. It allows administrators to create unique and complex passwords for each user, as well as assign each account to a single user for administrative duties. PAM also provides audit trails and logging capabilities, allowing administrators to monitor user activity and ensure that all systems are secure. According to the CompTIA Security+ SY0-601 Course Book, “PAM is the most comprehensive way to control and monitor privileged accounts”.
NEW QUESTION 14
Which of the following describes business units that purchase and implement scripting software without approval from an organization's technology Support staff?
- A. Shadow IT
- B. Hacktivist
- C. Insider threat
- D. script kiddie
Answer: A
Explanation:
shadow IT is the use of IT-related hardware or software by a department or individual without the knowledge or approval of the IT or security group within the organization12. Shadow IT can encompass cloud services, software, and hardware. The main area of concern today is the rapid adoption of cloud-based service1s.
According to one source3, shadow IT helps you know and identify which apps are being used and what your risk level is. 80% of employees use non-sanctioned apps that no one has reviewed, and may not be compliant with your security and compliance policies.
NEW QUESTION 15
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
• Hostname: ws01
• Domain: comptia.org
• IPv4: 10.1.9.50
• IPV4: 10.2.10.50
• Root: home.aspx
• DNS CNAME:homesite. Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.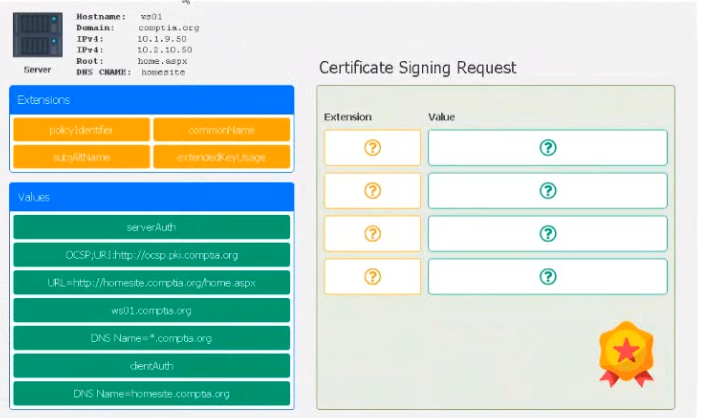
Solution:
Graphical user interface, application Description automatically generated
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
An organization wants to integrate its incident response processes into a workflow with automated decision points and actions based on predefined playbooks. Which of the following should the organization implement?
- A. SIEM
- B. SOAR
- C. EDR
- D. CASB
Answer: B
Explanation:
Security Orchestration, Automation, and Response (SOAR) should be implemented to integrate incident response processes into a workflow with automated decision points and actions based on predefined playbooks. References: CompTIA Security+ Study Guide, Exam SY0-601, Chapter 9
NEW QUESTION 17
......
Recommend!! Get the Full SY0-701 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/SY0-701-dumps.html (New 0 Q&As Version)