★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW SY0-701 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/SY0-701-dumps.html
Cause all that matters here is passing the CompTIA SY0-701 exam. Cause all that you need is a high score of SY0-701 CompTIA Security+ Exam exam. The only one thing you need to do is downloading Exambible SY0-701 exam study guides now. We will not let you down with our money-back guarantee.
Free SY0-701 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
A security assessment found that several embedded systems are running unsecure protocols. These Systems were purchased two years ago and the company that developed them is no longer in business Which of the following constraints BEST describes the reason the findings cannot be remediated?
- A. inability to authenticate
- B. Implied trust
- C. Lack of computing power
- D. Unavailable patch
Answer: D
Explanation:
If the systems are running unsecure protocols and the company that developed them is no longer in business, it is likely that there are no patches available to remediate the issue. References: CompTIA Security+ Study Guide, Sixth Edition, pages 35-36
CompTIA Security+ Study Guide, Sixth Edition, pages 35-36
NEW QUESTION 2
A cybersecurity administrator needs to allow mobile BYOD devices to access network resources. As the devices are not enrolled to the domain and do not have policies applied to them, which of the following are best practices for authentication and infrastructure security? (Select TWO).
- A. Create a new network for the mobile devices and block the communication to the internal network and servers
- B. Use a captive portal for user authentication.
- C. Authenticate users using OAuth for more resiliency
- D. Implement SSO and allow communication to the internal network
- E. Use the existing network and allow communication to the internal network and servers.
- F. Use a new and updated RADIUS server to maintain the best solution
Answer: BC
Explanation:
When allowing mobile BYOD devices to access network resources, using a captive portal for user authentication and authenticating users using OAuth are both best practices for authentication and infrastructure security. A captive portal requires users to authenticate before accessing the network and can be used to enforce policies and restrictions. OAuth allows users to authenticate using third-party providers, reducing the risk of password reuse and credential theft. References: CompTIA Security+ Study Guide, pages 217-218, 225-226
NEW QUESTION 3
Which of the following in a forensic investigation should be priorities based on the order of volatility? (Select TWO).
- A. Page files
- B. Event logs
- C. RAM
- D. Cache
- E. Stored files
- F. HDD
Answer: CD
Explanation:
In a forensic investigation, volatile data should be collected first, based on the order of volatility. RAM and Cache are examples of volatile data. References: CompTIA Security+ Study Guide 601, Chapter 11
NEW QUESTION 4
Ann, a customer, received a notification from her mortgage company stating her PII may be shared with partners, affiliates, and associates to maintain day-to-day business operations.
Which of the following documents did Ann receive?
- A. An annual privacy notice
- B. A non-disclosure agreement
- C. A privileged-user agreement
- D. A memorandum of understanding
Answer: A
Explanation:
Ann received an annual privacy notice from her mortgage company. An annual privacy notice is a statement from a financial institution or creditor that outlines the institution's privacy policy and explains how the institution collects, uses, and shares customers' personal information. It informs the customer about their rights under the Gramm-Leach-Bliley Act (GLBA) and the institution's practices for protecting their personal information. References: CompTIA Security+ Certification Exam Objectives - Exam SY0-601
CompTIA Security+ Certification Exam Objectives - Exam SY0-601
NEW QUESTION 5
Server administrators want to configure a cloud solution so that computing memory and processor usage are maximized most efficiently across a number of virtual servers. They also need to avoid potential
denial-of-service situations caused by availability. Which of the following should administrators configure to maximize system availability while efficiently utilizing available computing power?
- A. Dynamic resource allocation
- B. High availability
- C. Segmentation
- D. Container security
Answer: A
Explanation:
Dynamic resource allocation is a technique that allows cloud providers to adjust the amount and distribution of computing resources according to the changing demand and capacity of the cloud environment1. Dynamic resource allocation can improve the efficiency and utilization of available computing power, as well as reduce the cost and energy consumption of the cloud infrastructure1. Dynamic resource allocation can also enhance the system availability and reliability by avoiding potential denial-of-service situations caused by overloading or under-provisioning of resources1.
NEW QUESTION 6
The Chief Information Security Officer (CISO) has decided to reorganize security staff to concentrate on incident response and to outsource outbound Internet URL categorization and filtering to an outside company. Additionally, the CISO would like this solution to provide the same protections even when a company laptop or mobile device is away from a home office. Which of the following should the CISO choose?
- A. CASB
- B. Next-generation SWG
- C. NGFW
- D. Web-application firewall
Answer: B
Explanation:
The solution that the CISO should choose is Next-generation Secure Web Gateway (SWG), which provides URL filtering and categorization to prevent users from accessing malicious sites, even when they are away from the office. NGFWs are typically cloud-based and offer multiple security layers, including malware detection, intrusion prevention, and data loss prevention. References: CompTIA Security+ Study Guide Exam SY0-601, Chapter 4
CompTIA Security+ Study Guide Exam SY0-601, Chapter 4
NEW QUESTION 7
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following steps:
* 1. Configure the RADIUS server.
* 2. Configure the WiFi controller.
* 3. Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01 Password: guestpass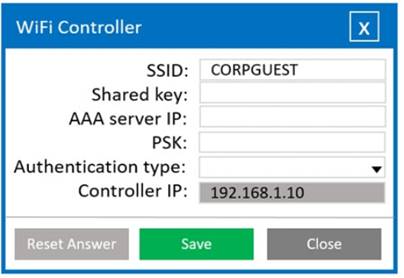
Solution:
Wifi Controller SSID: CORPGUEST
SHARED KEY: Secret
AAA server IP: 192.168.1.20
PSK: Blank
Authentication type: WPA2-EAP-PEAP-MSCHAPv2 Controller IP: 192.168.1.10
Radius Server Shared Key: Secret
Client IP: 192.168.1.10
Authentication Type: Active Directory Server IP: 192.168.1.20
Wireless Client SSID: CORPGUEST
Username: guest01 Userpassword: guestpass PSK: Blank
Authentication type: WPA2-Enterprise
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
A company has installed badge readers for building access but is finding unau-thorized individuals roaming the hallways Of the following is the most likely cause?
- A. Shoulder surfing
- B. Phishing
- C. Tailgating
- D. Identity fraud
Answer: C
Explanation:
Tailgating is a physical security threat that occurs when an unauthorized person follows an authorized person into a restricted area without proper identification or authorization. It can cause unauthorized individuals to roam the hallways after gaining access through badge readers installed for building access.
NEW QUESTION 9
Hackers recently attacked a company's network and obtained several unfavorable pictures from the Chief Executive Officer's workstation. The hackers are threatening to send the images to the press if a ransom is not paid. Which of the following is impacted the MOST?
- A. Identify theft
- B. Data loss
- C. Data exfiltration
- D. Reputation
Answer: D
Explanation:
The best option that describes what is impacted the most by the hackers’ attack and threat would be D. Reputation. Reputation is the perception or opinion that others have about a person or an organization. Reputation can affect the trust, credibility, and success of a person or an organization. In this scenario, if the hackers send the unfavorable pictures to the press, it can damage the reputation of the Chief Executive Officer and the company, and cause negative consequences such as loss of customers, partners, investors, or employees.
NEW QUESTION 10
An organization wants to enable built-in FDE on all laptops Which of the following should the organization ensure is Installed on all laptops?
- A. TPM
- B. CA
- C. SAML
- D. CRL
Answer: A
Explanation:
The organization should ensure that a Trusted Platform Module (TPM) is installed on all laptops in order to enable built-in Full Disk Encryption (FDE). TPM is a hardware-based security chip that stores encryption keys and helps to protect data from malicious attacks. It is important to ensure that the TPM is properly configured and enabled in order to get the most out of FDE.
NEW QUESTION 11
A security analyst is reviewing SIEM logs during an ongoing attack and notices the following:
http://company.com/get
php? f=/etc/passwd
http://company.com/..%2F.
.42 F..42F.. $2Fetct2Fshadow
http: //company.com/../../../ ../etc/passwd
Which of the following best describes the type of attack?
- A. SQLi
- B. CSRF
- C. API attacks
- D. Directory traversal
Answer: D
Explanation:
Directory traversal (also known as file path traversal) is a web security vulnerability that allows an attacker to read arbitrary files on the server that is running an application. This might include application code and data, credentials for back-end systems, and sensitive operating system files1. In some cases, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behavior, and ultimately take full control of the server1.
Directory traversal in its simplest form uses the …/ pattern, which means to step up one level in the directory structure. By repeating this pattern, an attacker can traverse to the root directory and then access any file or folder on the server. For example, the following request attempts to read the Unix password file /etc/passwd from the server:
http://company.com/get.php?f=/etc/passwd
Some web applications may implement some defenses against directory traversal attacks, such as filtering out
…/ patterns or percent-decoding the user input before validating it. However, these defenses can often be bypassed by using variations or encoding techniques. For example, the following requests use different ways to represent …/ or / characters:
http://company.com/…%2F…%2F…%2Fetc%2Fpasswd
http://company.com/…/…/…/%2Fetc%2Fpasswd http://company.com/%2E%2E/%2E%2E/%2E%2E/etc/passwd
These requests may still result in directory traversal attacks if the web application does not properly handle them12.
* A. SQLi. This is not the correct answer, because SQLi stands for SQL Injection, which is an attack that exploits a vulnerability in a web application’s database layer, where malicious SQL statements are inserted into an entry field for execution3. The requests in the question do not contain any SQL statements or commands.
* B. CSRF. This is not the correct answer, because CSRF stands for Cross-Site Request Forgery, which is an attack that exploits the trust a web server has in a user’s browser, where malicious requests are sent to the web server using the user’s credentials4. The requests in the question do not indicate that they are forged or sent by another website.
* C. API attacks. This is not the correct answer, because API stands for Application Programming Interface, which is a set of rules and specifications that allow software components to communicate and exchange data. API attacks are attacks that target the vulnerabilities or weaknesses of APIs, such as authentication, authorization, encryption, rate limiting, or input validation5. The requests in the question do not target any specific API functionality or feature.
* D. Directory traversal. This is the correct answer, because directory traversal is an attack that exploits insufficient security validation or sanitization of user-supplied file names, such that characters representing “traverse to parent directory” are passed through to the operating system’s file system API12. The requests in the question contain various patterns of …/ or / characters that attempt to access restricted files and directories on the server.
Reference: What is directory traversal, and how to prevent it? - PortSwigger, Directory traversal attack - Wikipedia, What Is SQL Injection (SQLi) and How To Prevent It, What Is Cross-Site Request Forgery (CSRF)? | Acunetix, API Security Testing – How to Hack an API and Get Away with It (Part 1 of 3).
NEW QUESTION 12
A web server has been compromised due to a ransomware attack. Further Investigation reveals the ransomware has been in the server for the past 72 hours. The systems administrator needs to get the services back up as soon as possible. Which of the following should the administrator use to restore services to a secure state?
- A. The last incremental backup that was conducted 72 hours ago
- B. The last known-good configuration stored by the operating system
- C. The last full backup that was conducted seven days ago
- D. The baseline OS configuration
Answer: A
Explanation:
The last incremental backup that was conducted 72 hours ago would be the best option to restore the services to a secure state, as it would contain the most recent data before the ransomware infection. Incremental backups only store the changes made since the last backup, so they are faster and use less storage space than full backups. Restoring from an incremental backup would also minimize the data loss and downtime caused by the ransomware attack. References: https://www.comptia.org/blog/mature-cybersecurity-response-to-ransomware
https://www.comptia.org/blog/mature-cybersecurity-response-to-ransomware  https://www.youtube.com/watch?v=HszU4nEAlFc
https://www.youtube.com/watch?v=HszU4nEAlFc
NEW QUESTION 13
The compliance team requires an annual recertification of privileged and non-privileged user access. However, multiple users who left the company six months ago still have access. Which of the following would have prevented this compliance violation?
- A. Account audits
- B. AUP
- C. Password reuse
- D. SSO
Answer: A
Explanation:
Account audits are periodic reviews of user accounts to ensure that they are being used appropriately and that access is being granted and revoked in accordance with the organization's policies and procedures. If the compliance team had been conducting regular account audits, they would have identified the users who left the company six months ago and ensured that their access was revoked in a timely manner. This would have prevented the compliance violation caused by these users still having access to the company's systems.
To prevent this compliance violation, the company should implement account audits. An account audit is a regular review of all user accounts to ensure that they are being used properly and that they are in compliance with the company's security policies. By conducting regular account audits, the company can identify inactive or unused accounts and remove access for those users. This will help to prevent compliance violations and ensure that only authorized users have access to the company's systems and data.
NEW QUESTION 14
After a hardware incident, an unplanned emergency maintenance activity was conducted to rectify the issue. Multiple alerts were generated on the SIEM during this period of time. Which of the following BEST explains what happened?
- A. The unexpected traffic correlated against multiple rules, generating multiple alerts.
- B. Multiple alerts were generated due to an attack occurring at the same time.
- C. An error in the correlation rules triggered multiple alerts.
- D. The SIEM was unable to correlate the rules, triggering the alert
Answer: A
Explanation:
Multiple alerts were generated on the SIEM during the emergency maintenance activity due to unexpected traffic correlated against multiple rules. The SIEM generates alerts when it detects an event that matches a rule in its rulebase. If the event matches multiple rules, the SIEM will generate multiple alerts.
Reference: CompTIA Security+ Study Guide, Exam SY0-601, Chapter 3: Architecture and Design
NEW QUESTION 15
During an incident a company CIRT determine it is necessary to observe the continued network-based transaction between a callback domain and the malware running on an enterprise PC. Which of the following techniques would be BEST to enable this activity while reducing the risk of lateral spread and the risk that the adversary would notice any changes?
- A. Physical move the PC to a separate internet pint of presence
- B. Create and apply micro segmentation rules.
- C. Emulate the malware in a heavily monitored DM Z segment.
- D. Apply network blacklisting rules for the adversary domain
Answer: C
Explanation:
To observe the continued network-based transaction between a callback domain and the malware running on an enterprise PC while reducing the risk of lateral spread and the risk that the adversary would notice any changes, the best technique to use is to emulate the malware in a heavily monitored DMZ segment. This is a secure environment that is isolated from the rest of the network and can be heavily monitored to detect any suspicious activity. By emulating the malware in this environment, the activity can be observed without the risk of lateral spread or detection by the adversary. References:
https://www.sans.org/blog/incident-response-fundamentals-why-is-the-dmz-so-important/
NEW QUESTION 16
A security administrator Is evaluating remote access solutions for employees who are geographically dispersed. Which of the following would provide the MOST secure remote access? (Select TWO).
- A. IPSec
- B. SFTP
- C. SRTP
- D. LDAPS
- E. S/MIME
- F. SSL VPN
Answer: AF
Explanation:
IPSec (Internet Protocol Security) is a technology that provides secure communication over the internet by encrypting traffic and authenticating it at both the sender and receiver. It can be used to create secure tunnels between two or more devices, allowing users to access resources securely and privately.
SSL VPN (Secure Sockets Layer Virtual Private Network) is a type of VPN that uses an SSL/TLS connection to encrypt traffic between two or more devices. It is a secure and reliable solution for providing remote access, as all traffic is encrypted and authenticated. Additionally, SSL VPNs can also be used to restrict access to certain websites and services, making them a secure and robust solution for remote access.
NEW QUESTION 17
......
P.S. Surepassexam now are offering 100% pass ensure SY0-701 dumps! All SY0-701 exam questions have been updated with correct answers: https://www.surepassexam.com/SY0-701-exam-dumps.html (0 New Questions)