★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW SY0-701 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/SY0-701-dumps.html
Your success in CompTIA SY0-701 is our sole target and we develop all our SY0-701 braindumps in a way that facilitates the attainment of this target. Not only is our SY0-701 study material the best you can find, it is also the most detailed and the most updated. SY0-701 Practice Exams for CompTIA SY0-701 are written to the highest standards of technical accuracy.
CompTIA SY0-701 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly Which of the following technologies should the IT manager use when implementing MFA?
- A. One-time passwords
- B. Email tokens
- C. Push notifications
- D. Hardware authentication
Answer: C
Explanation:
Push notifications are a type of technology that allows an application or a service to send messages or alerts to a user’s device without requiring the user to open the application or the service. They can be used for multi-factor authentication (MFA) by sending a prompt or a code to the user’s device that the user has to approve or enter to verify their identity. They can be non-disruptive and user friendly because they do not require the user to remember or type anything, and they can be delivered instantly and securely.
NEW QUESTION 2
A new plug-and-play storage device was installed on a PC in the corporate environment. Which of the following safeguards will BEST help to protect the PC from malicious files on the storage device?
- A. Change the default settings on the PC.
- B. Define the PC firewall rules to limit access.
- C. Encrypt the disk on the storage device.
- D. Plug the storage device in to the UPS
Answer: A
Explanation:
The best option that will help to protect the PC from malicious files on the storage device would be A. Change the default settings on the PC. Changing the default settings on the PC can include disabling the autorun or autoplay feature, which can prevent malicious files from executing automatically when the storage device is plugged in. Changing the default settings can also include enabling antivirus software, updating the operating system and applications, and configuring user account control and permissions.
NEW QUESTION 3
A Chief Information Officer is concerned about employees using company-issued laptops lo steal data when accessing network shares. Which of the following should the company Implement?
- A. DLP
- B. CASB
- C. HIDS
- D. EDR
- E. UEFI
Answer: A
Explanation:
The company should implement Data Loss Prevention (DLP) to prevent employees from stealing data when accessing network shares. References: CompTIA Security+ Study Guide Exam SY0-601, Chapter 8
CompTIA Security+ Study Guide Exam SY0-601, Chapter 8
NEW QUESTION 4
A Security engineer needs to implement an MDM solution that complies with the corporate mobile device policy. The policy states that in order for mobile users to access corporate resources on their devices, the following requirements must be met: Mobile device OSs must be patched up to the latest release.
Mobile device OSs must be patched up to the latest release.  A screen lock must be enabled (passcode or biometric).
A screen lock must be enabled (passcode or biometric). Corporate data must be removed if the device is reported lost or stolen.
Corporate data must be removed if the device is reported lost or stolen.
Which of the following controls should the security engineer configure? (Select two).
- A. Disable firmware over-the-air
- B. Storage segmentation
- C. Posture checking
- D. Remote wipe
- E. Full device encryption
- F. Geofencing
Answer: CD
Explanation:
Posture checking and remote wipe are two controls that the security engineer should configure to comply with the corporate mobile device policy. Posture checking is a process that verifies if a mobile device meets certain security requirements before allowing it to access corporate resources. For example, posture checking can check if the device OS is patched up to the latest release and if a screen lock is enabled. Remote wipe is a feature that allows the administrator to erase all data from a mobile device remotely, in case it is lost or stolen. This can prevent unauthorized access to corporate data on the device.
NEW QUESTION 5
A company's public-facing website, https://www.organization.com, has an IP address of 166.18.75.6. However, over the past hour the SOC has received reports of the site's homepage displaying incorrect information. A quick nslookup search shows hitps://;www.organization.com is pointing to 151.191.122.115. Which of the following is occurring?
- A. DoS attack
- B. ARP poisoning
- C. DNS spoofing
- D. NXDOMAIN attack
Answer: C
Explanation:
The issue is DNS spoofing, where the DNS resolution has been compromised and is pointing to a malicious IP address. References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 7
NEW QUESTION 6
A security administrator is integrating several segments onto a single network. One of the segments, which includes legacy devices, presents a significant amount of risk to the network.
Which of the following would allow users to access to the legacy devices without compromising the security of the entire network?
- A. NIDS
- B. MAC filtering
- C. Jump server
- D. IPSec
- E. NAT gateway
Answer: C
Explanation:
A jump server is a device that acts as an intermediary between users and other devices on a network. A jump server can provide a secure and controlled access point to the legacy devices without exposing them directly to the network. A jump server can also enforce authentication, authorization, logging, and auditing policies.
NEW QUESTION 7
A security architect is required to deploy to conference rooms some workstations that will allow sensitive data to be displayed on large screens. Due to the nature of the data, it cannot be stored in the conference rooms. The file share is located in a local data center. Which of the following should the security architect recommend to best meet the requirement?
- A. Fog computing and KVMs
- B. VDI and thin clients
- C. Private cloud and DLP
- D. Full drive encryption and thick clients
Answer: B
Explanation:
VDI and thin clients are the best solution to deploy to conference rooms for displaying sensitive data on large screens. VDI stands for virtual desktop infrastructure, which is a technology that hosts the desktop operating systems and applications on a central server or cloud and allows users to access them remotely. Thin clients are devices that have minimal hardware and software components and rely on a network connection to the VDI system. By using VDI and thin clients, the security architect can ensure that the sensitive data is not stored in the conference rooms, but rather in a secure data center or cloud. The thin clients can also be easily managed and updated centrally, reducing the maintenance costs and risks. References: https://www.acecloudhosting.com/blog/what-is-vdi-thin-client/
https://www.acecloudhosting.com/blog/what-is-vdi-thin-client/  https://www.parallels.com/blogs/ras/vdi-thin-client/
https://www.parallels.com/blogs/ras/vdi-thin-client/
NEW QUESTION 8
A security analyst needs to implement an MDM solution for BYOD users that will allow the company to retain control over company emails residing on the devices and limit data exfiltration that might occur if the devices are lost or stolen.Which of the following would BEST meet these requirements? (Select TWO).
- A. Full-device encryption
- B. Network usage rules
- C. Geofencing
- D. Containerization
- E. Application whitelisting
- F. Remote control
Answer: DE
Explanation:
MDM solutions emerged to solve problems created by BYOD. With MDM, IT teams can remotely wipe devices clean if they are lost or stolen. MDM also makes the life of an IT administrator a lot easier as it allows them to enforce corporate policies, apply software updates, and even ensure that password protection is used on each device. Containerization and application whitelisting are two features of MDM that can help retain control over company emails residing on the devices and limit data exfiltration that might occur if the devices are lost or stolen.
Containerization is a technique that creates a separate and secure space on the device for work-related data and applications. This way, personal and corporate data are isolated from each other, and IT admins can manage only the work container without affecting the user’s privacy. Containerization also allows IT admins to remotely wipe only the work container if needed, leaving the personal data intact.
Application whitelisting is a technique that allows only authorized applications to run on the device. This way, IT admins can prevent users from installing or using malicious or unapproved applications that might compromise the security of corporate data. Application whitelisting also allows IT admins to control which applications can access corporate resources, such as email servers or cloud storage.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.office1.com/blog/byod-vs-mdm
NEW QUESTION 9
Two organizations are discussing a possible merger Both Organizations Chief Fi-nancial Officers would like to safely share payroll data with each Other to de-termine if the pay scales for different roles are similar at both organizations Which Of the following techniques would be best to protect employee data while allowing the companies to successfully share this information?
- A. Pseudo-anonymization
- B. Tokenization
- C. Data masking
- D. Encryption
Answer: A
Explanation:
Pseudo-anonymization is a technique of replacing sensitive data with artificial identifiers or pseudonyms that preserve some characteristics or attributes of the original data. It can protect employee data while allowing the companies to successfully share this information by removing direct identifiers such as names, addresses, etc., but retaining indirect identifiers such as job roles, pay scales, etc., that are relevant for the comparison.
NEW QUESTION 10
Which of the following describes the exploitation of an interactive process to gain access to restricted areas?
- A. Persistence
- B. Port scanning
- C. Privilege escalation
- D. Pharming
Answer: C
Explanation:
Privilege escalation describes the exploitation of an interactive process to gain access to restricted areas. It is a type of attack that allows a normal user to obtain higher privileges or access rights on a system or network, such as administrative or root access. Privilege escalation can be achieved by exploiting a vulnerability, design flaw, or misconfiguration in the system or application. Privilege escalation can allow an attacker to perform unauthorized actions, such as accessing sensitive data, installing malware, or compromising other systems. References: https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/privilege-escalation-3/
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/privilege-escalation-3/ https://www.linkedin.com/learning/comptia-security-plus-sy0-601-cert-prep-2-secure-code-design-and-im
https://www.linkedin.com/learning/comptia-security-plus-sy0-601-cert-prep-2-secure-code-design-and-im
NEW QUESTION 11
An organization is concerned about hackers potentially entering a facility and plugging in a remotely accessible Kali Linux box. Which of the following should be the first lines of defense against such an attack? (Select TWO)
- A. MAC filtering
- B. Zero trust segmentation
- C. Network access control
- D. Access control vestibules
- E. Guards
- F. Bollards
Answer: CE
Explanation:
Network access control (NAC) is a technique that restricts access to a network based on the identity, role, device, location, or other criteria of the users or devices. NAC can prevent unauthorized or malicious devices from connecting to a network and accessing sensitive data or resources.
Guards are physical security personnel who monitor and control access to a facility. Guards can prevent unauthorized or malicious individuals from entering a facility and plugging in a remotely accessible device.
NEW QUESTION 12
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
- A. Accept
- B. Transfer
- C. Mitigate
- D. Avoid
Answer: B
Explanation:
A company purchased cyber insurance to address items listed on the risk register. This represents a transfer strategy. A transfer strategy involves transferring or sharing some or all of the responsibility or impact of a risk to another party, such as an insurer, a supplier, or a partner. A transfer strategy can help to reduce the financial liability or exposure of the company in case of a security incident or breach. References: https://www.comptia.org/blog/what-is-cyber-insurance
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 13
A financial institution would like to store its customer data in a cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would BEST meet the requirement?
- A. Asymmetric
- B. Symmetric
- C. Homomorphic
- D. Ephemeral
Answer: B
Explanation:
Symmetric encryption allows data to be encrypted and decrypted using the same key. This is useful when the data needs to be accessed and manipulated while still encrypted. References: CompTIA Security+ Study Guide, Exam SY0-601, Chapter 6
NEW QUESTION 14
Which of the following secure application development concepts aims to block verbose error messages from being shown in a user’s interface?
- A. OWASP
- B. Obfuscation/camouflage
- C. Test environment
- D. Prevent of information exposure
Answer: D
Explanation:
Preventing information exposure is a secure application development concept that aims to block verbose error messages from being shown in a user’s interface. Verbose error messages are detailed messages that provide information about errors or exceptions that occur in an application. Verbose error messages may reveal sensitive information about the application’s structure, configuration, logic, or data that could be exploited by attackers. Therefore, preventing information exposure involves implementing proper error handling mechanisms that display generic or user-friendly messages instead of verbose error messages.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://owasp.org/www-project-top-ten/2017/A6_2017-Security_Misconfiguration
NEW QUESTION 15
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible. INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:  WAP
WAP DHCP Server
DHCP Server  AAA Server
AAA Server Wireless Controller
Wireless Controller  LDAP Server
LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.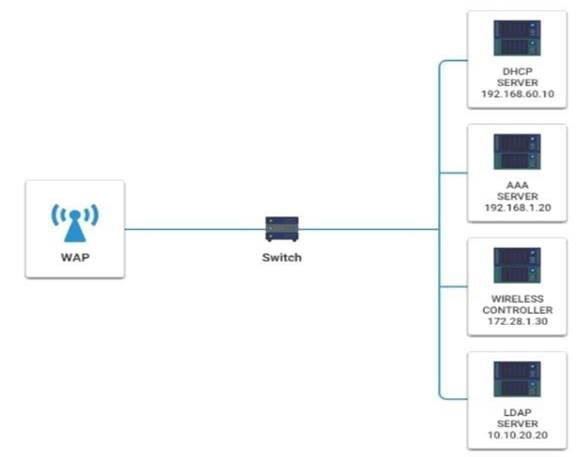
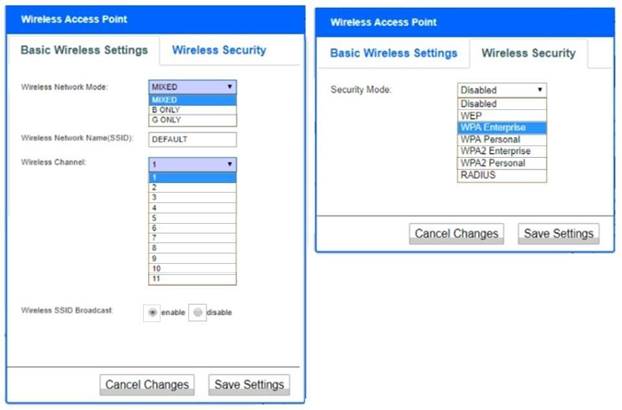
Solution:
Wireless Access Point Network Mode – G only Wireless Channel – 11
Wireless SSID Broadcast – disable Security settings – WPA2 Professional
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
A security analyst needs an overview of vulnerabilities for a host on the network. Which of the following is the BEST type of scan for the analyst to run to discover which vulnerable services are running?
- A. Non-credentialed
- B. Web application
- C. Privileged
- D. Internal
Answer: C
Explanation:
Privileged scanning, also known as credentialed scanning, is a type of vulnerability scanning that uses a valid user account to log in to the target host and examine vulnerabilities from a trusted user’s perspective. It can provide more accurate and comprehensive results than unprivileged scanning, which does not use any credentials and only scans for externally visible vulnerabilities.
NEW QUESTION 17
......
100% Valid and Newest Version SY0-701 Questions & Answers shared by Allfreedumps.com, Get Full Dumps HERE: https://www.allfreedumps.com/SY0-701-dumps.html (New 0 Q&As)