★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW PT0-002 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/PT0-002-dumps.html
It is impossible to pass CompTIA PT0-002 exam without any help in the short term. Come to Pass4sure soon and find the most advanced, correct and guaranteed CompTIA PT0-002 practice questions. You will get a surprising result by our Avant-garde CompTIA PenTest+ Certification Exam practice guides.
Online PT0-002 free questions and answers of New Version:
NEW QUESTION 1
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
- A. Add a dependency checker into the tool chain.
- B. Perform routine static and dynamic analysis of committed code.
- C. Validate API security settings before deployment.
- D. Perform fuzz testing of compiled binaries.
Answer: D
NEW QUESTION 2
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company’s servers. Which of the following actions would BEST enable the tester to perform phishing in a later stage of the assessment?
- A. Test for RFC-defined protocol conformance.
- B. Attempt to brute force authentication to the service.
- C. Perform a reverse DNS query and match to the service banner.
- D. Check for an open relay configuration.
Answer: C
NEW QUESTION 3
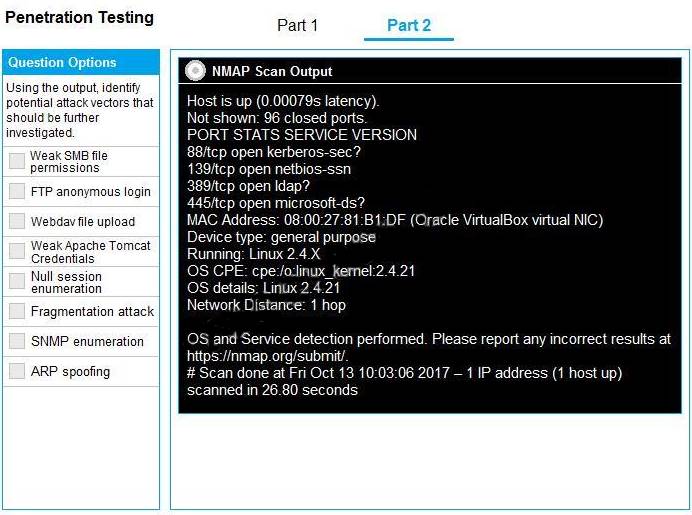
You are a penetration tester running port scans on a server. INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.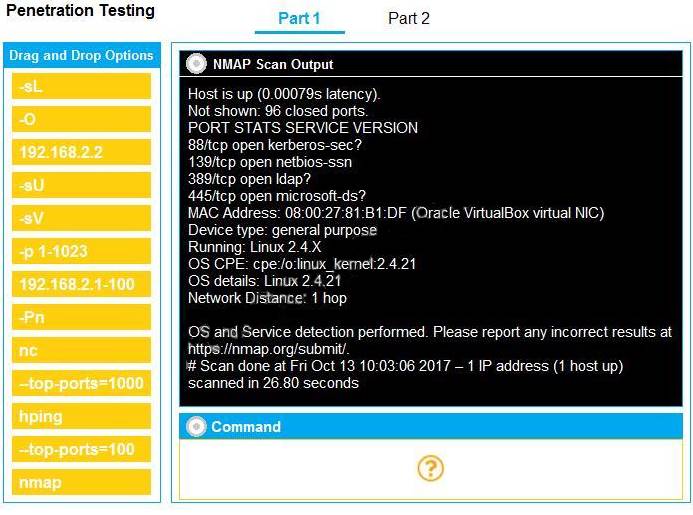
Solution:
Part 1 - nmap 192.168.2.2 -sV -O
Part 2 - Weak SMB file permissions
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
A large client wants a penetration tester to scan for devices within its network that are Internet facing. The client is specifically looking for Cisco devices with no authentication requirements. Which of the following settings in Shodan would meet the client’s requirements?
- A. “cisco-ios” “admin+1234”
- B. “cisco-ios” “no-password”
- C. “cisco-ios” “default-passwords”
- D. “cisco-ios” “last-modified”
Answer: A
NEW QUESTION 5
A company recruited a penetration tester to configure wireless IDS over the network. Which of the following tools would BEST test the effectiveness of the wireless IDS solutions?
- A. Aircrack-ng
- B. Wireshark
- C. Wifite
- D. Kismet
Answer: A
NEW QUESTION 6
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
- A. RFID cloning
- B. RFID tagging
- C. Meta tagging
- D. Tag nesting
Answer: C
NEW QUESTION 7
A software development team is concerned that a new product's 64-bit Windows binaries can be deconstructed to the underlying code. Which of the following tools can a penetration tester utilize to help the team gauge what an attacker might see in the binaries?
- A. Immunity Debugger
- B. OllyDbg
- C. GDB
- D. Drozer
Answer: B
NEW QUESTION 8
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
- A. devices produce more heat and consume more power.
- B. devices are obsolete and are no longer available for replacement.
- C. protocols are more difficult to understand.
- D. devices may cause physical world effects.
Answer: D
Explanation:
"A significant issue identified by Wiberg is that using active network scanners, such as Nmap, presents a weakness when attempting port recognition or service detection on SCADA devices. Wiberg states that active tools such as Nmap can use unusual TCP segment data to try and find available ports. Furthermore, they can open a massive amount of connections with a specific SCADA device but then fail to close them gracefully." And since SCADA and ICS devices are designed and implemented with little attention having been paid to the operational security of these devices and their ability to handle errors or unexpected events, the presence idle open connections may result into errors that cannot be handled by the devices.
NEW QUESTION 9
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider’s metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
- A. Cross-site request forgery
- B. Server-side request forgery
- C. Remote file inclusion
- D. Local file inclusion
Answer: B
NEW QUESTION 10
A penetration tester found the following valid URL while doing a manual assessment of a web application: http://www.example.com/product.php?id=123987.
Which of the following automated tools would be best to use NEXT to try to identify a vulnerability in this URL?
- A. SQLmap
- B. Nessus
- C. Nikto
- D. DirBuster
Answer: B
NEW QUESTION 11
A penetration tester received a .pcap file to look for credentials to use in an engagement. Which of the following tools should the tester utilize to open and read the .pcap file?
- A. Nmap
- B. Wireshark
- C. Metasploit
- D. Netcat
Answer: B
NEW QUESTION 12
Which of the following are the MOST important items to include in the final report for a penetration test?
(Choose two.)
- A. The CVSS score of the finding
- B. The network location of the vulnerable device
- C. The vulnerability identifier
- D. The client acceptance form
- E. The name of the person who found the flaw
- F. The tool used to find the issue
Answer: CF
NEW QUESTION 13
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
- A. Direct-to-origin
- B. Cross-site scripting
- C. Malware injection
- D. Credential harvesting
Answer: A
NEW QUESTION 14
A penetration tester wants to perform reconnaissance without being detected. Which of the following activities have a MINIMAL chance of detection? (Choose two.)
- A. Open-source research
- B. A ping sweep
- C. Traffic sniffing
- D. Port knocking
- E. A vulnerability scan
- F. An Nmap scan
Answer: AC
NEW QUESTION 15
A penetration tester ran an Nmap scan on an Internet-facing network device with the –F option and found a few open ports. To further enumerate, the tester ran another scan using the following command:
nmap –O –A –sS –p- 100.100.100.50
Nmap returned that all 65,535 ports were filtered. Which of the following MOST likely occurred on the second scan?
- A. A firewall or IPS blocked the scan.
- B. The penetration tester used unsupported flags.
- C. The edge network device was disconnected.
- D. The scan returned ICMP echo replies.
Answer: A
NEW QUESTION 16
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
- A. OpenVAS
- B. Drozer
- C. Burp Suite
- D. OWASP ZAP
Answer: A
NEW QUESTION 17
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
- A. Perform XSS.
- B. Conduct a watering-hole attack.
- C. Use BeEF.
- D. Use browser autopwn.
Answer: A
NEW QUESTION 18
......
P.S. Easily pass PT0-002 Exam with 110 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam PT0-002 Dumps: https://www.surepassexam.com/PT0-002-exam-dumps.html (110 New Questions)