★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW CAS-004 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/CAS-004-dumps.html
It is impossible to pass CompTIA CAS-004 exam without any help in the short term. Come to Pass4sure soon and find the most advanced, correct and guaranteed CompTIA CAS-004 practice questions. You will get a surprising result by our Improve CompTIA Advanced Security Practitioner (CASP+) Exam practice guides.
Check CAS-004 free dumps before getting the full version:
NEW QUESTION 1
An e-commerce company is running a web server on premises, and the resource utilization is usually less than 30%. During the last two holiday seasons, the server experienced performance issues because of too many connections, and several customers were not able to finalize purchase orders. The company is looking to change the server configuration to avoid this kind of performance issue.
Which of the following is the MOST cost-effective solution?
- A. Move the server to a cloud provider.
- B. Change the operating system.
- C. Buy a new server and create an active-active cluster.
- D. Upgrade the server with a new one.
Answer: A
NEW QUESTION 2
A network architect is designing a new SD-WAN architecture to connect all local sites to a central hub site. The hub is then responsible for redirecting traffic to public cloud and datacenter applications. The SD-WAN routers are managed through a SaaS, and the same security policy is applied to staff whether working in the office or at a remote location. The main requirements are the following:
* 1. The network supports core applications that have 99.99% uptime.
* 2. Configuration updates to the SD-WAN routers can only be initiated from the management service.
* 3. Documents downloaded from websites must be scanned for malware.
Which of the following solutions should the network architect implement to meet the requirements?
- A. Reverse proxy, stateful firewalls, and VPNs at the local sites
- B. IDSs, WAFs, and forward proxy IDS
- C. DoS protection at the hub site, mutual certificate authentication, and cloud proxy
- D. IPSs at the hub, Layer 4 firewalls, and DLP
Answer: B
NEW QUESTION 3
The Chief information Officer (CIO) asks the system administrator to improve email security at the company based on the following requirements:
* Transaction being requested by unauthorized individuals.
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attackers using email to malware and ransomeware.
* Exfiltration of sensitive company information.
The cloud-based email solution will provide anti-malware reputation-based scanning, signature-based scanning, and sandboxing .
Which of the following is the BEST option to resolve the boar’s concerns for this email migration?
- A. Data loss prevention
- B. Endpoint detection response
- C. SSL VPN
- D. Application whitelisting
Answer: A
NEW QUESTION 4
A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate
UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:
The security engineer looks at the UTM firewall rules and finds the following: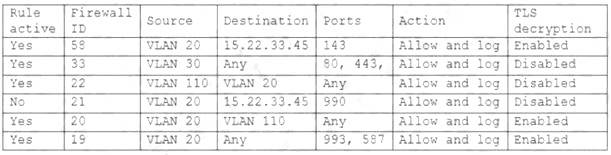
Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?
- A. Contact the email service provider and ask if the company IP is blocked.
- B. Confirm the email server certificate is installed on the corporate computers.
- C. Make sure the UTM certificate is imported on the corporate computers.
- D. Create an IMAPS firewall rule to ensure email is allowed.
Answer: C
NEW QUESTION 5
A security engineer needs to recommend a solution that will meet the following requirements: Identify sensitive data in the provider’s network
Maintain compliance with company and regulatory guidelines
Detect and respond to insider threats, privileged user threats, and compromised accounts Enforce datacentric security, such as encryption, tokenization, and access control Which of the following solutions should the security engineer recommend to address these requirements?
- A. WAF
- B. CASB
- C. SWG
- D. DLP
Answer: A
NEW QUESTION 6
A company has decided to purchase a license for software that is used to operate a mission-critical process. The third-party developer is new to the industry but is delivering what the company needs at this time.
Which of the following BEST describes the reason why utilizing a source code escrow will reduce the operational risk to the company if the third party stops supporting the application?
- A. The company will have access to the latest version to continue development.
- B. The company will be able to force the third-party developer to continue support.
- C. The company will be able to manage the third-party developer’s development process.
- D. The company will be paid by the third-party developer to hire a new development team.
Answer: B
NEW QUESTION 7
A business stores personal client data of individuals residing in the EU in order to process requests for mortgage loan approvals. Which of the following does the business’s IT manager need to consider?
- A. The availability of personal data
- B. The right to personal data erasure
- C. The company’s annual revenue
- D. The language of the web application
Answer: B
Explanation:
Reference: https://gdpr.eu/right-to-beforgotten/#:~:text=Also%20known%20as%20the%20right,to%20delete%20their%20personal%20data.&text=The%20General%20Data%20Protection%20Regulation,collected%2C%20processed%2C%20and%20erased
NEW QUESTION 8
A company is looking to fortify its cybersecurity defenses and is focusing on its network infrastructure. The solution cannot affect the availability of the company’s services to ensure false positives do not drop legitimate traffic.
Which of the following would satisfy the requirement?
- A. NIDS
- B. NIPS
- C. WAF
- D. Reverse proxy
Answer: B
Explanation:
Reference: https://subscription.packtpub.com/book/networking-and-servers/9781782174905/5/ch05lvl1sec38/differentiatingbetween-nids-and-nips
NEW QUESTION 9
A security engineer was auditing an organization’s current software development practice and discovered that multiple opensource libraries were Integrated into the organization’s software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries?
- A. Perform additional SAST/DAST on the open-source libraries.
- B. Implement the SDLC security guidelines.
- C. Track the library versions and monitor the CVE website for related vulnerabilities.
- D. Perform unit testing of the open-source libraries.
Answer: B
Explanation:
Reference: https://www.whitesourcesoftware.com/resources/blog/application-security-best-practices/
NEW QUESTION 10
A company’s claims processed department has a mobile workforce that receives a large number of email submissions from personal email addresses. An employees recently received an email that approved to be claim form, but it installed malicious software on the employee’s laptop when was opened.
- A. Impalement application whitelisting and add only the email client to the whitelist for laptop in the claims processing department.
- B. Required all laptops to connect to the VPN before accessing email.
- C. Implement cloud-based content filtering with sandboxing capabilities.
- D. Install a mail gateway to scan incoming messages and strip attachments before they reach the mailbox.
Answer: C
NEW QUESTION 11
Over the last 90 days, many storage services has been exposed in the cloud services environments, and the security team does not have the ability to see is creating these instance. Shadow IT is creating data services and instances faster than the small security team can keep up with them. The Chief information security Officer (CIASO) has asked the security officer (CISO) has asked the security lead architect to architect to recommend solutions to this problem.
Which of the following BEST addresses the problem best address the problem with the least amount of administrative effort?
- A. Compile a list of firewall requests and compare than against interesting cloud services.
- B. Implement a CASB solution and track cloud service use cases for greater visibility.
- C. Implement a user-behavior system to associate user events and cloud service creation events.
- D. Capture all log and feed then to a SIEM and then for cloud service events
Answer: C
NEW QUESTION 12
During a remodel, a company’s computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room. The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
- A. Monitor camera footage corresponding to a valid access request.
- B. Require both security and management to open the door.
- C. Require department managers to review denied-access requests.
- D. Issue new entry badges on a weekly basis.
Answer: A
Explanation:
Reference: https://www.getkisi.com/access-control
NEW QUESTION 13
Ransomware encrypted the entire human resources fileshare for a large financial institution. Security operations personnel were unaware of the activity until it was too late to stop it. The restoration will take approximately four hours, and the last backup occurred 48 hours ago. The management team has indicated that the RPO for a disaster recovery event for this data classification is 24 hours.
Based on RPO requirements, which of the following recommendations should the management team make?
- A. Leave the current backup schedule intact and pay the ransom to decrypt the data.
- B. Leave the current backup schedule intact and make the human resources fileshare read-only.
- C. Increase the frequency of backups and create SIEM alerts for IOCs.
- D. Decrease the frequency of backups and pay the ransom to decrypt the data.
Answer: C
NEW QUESTION 14
A health company has reached the physical and computing capabilities in its datacenter, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare application that process sensitive health and payment information .
Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standard for virtualization and cloud computing?
- A. Hybrid IaaS solution in a single-tenancy cloud
- B. Pass solution in a multinency cloud
- C. SaaS solution in a community cloud
- D. Private SaaS solution in a single tenancy cloud.
Answer: D
NEW QUESTION 15
A small company recently developed prototype technology for a military program. The company’s security engineer is concerned about potential theft of the newly developed, proprietary information.
Which of the following should the security engineer do to BEST manage the threats proactively?
- A. Join an information-sharing community that is relevant to the company.
- B. Leverage the MITRE ATT&CK framework to map the TTR.
- C. Use OSINT techniques to evaluate and analyze the threats.
- D. Update security awareness training to address new threats, such as best practices for data security.
Answer: D
NEW QUESTION 16
Which of the following are risks associated with vendor lock-in? (Choose two.)
- A. The client can seamlessly move data.
- B. The vendor can change product offerings.
- C. The client receives a sufficient level of service.
- D. The client experiences decreased quality of service.
- E. The client can leverage a multicloud approach.
- F. The client experiences increased interoperability.
Answer: BD
Explanation:
Reference: https://www.cloudflare.com/learning/cloud/what-is-vendor-lockin/#:~:text=Vendor%20lock%2Din%20can%20become,may%20involve%20reformatting%20the%20data
NEW QUESTION 17
A systems administrator is in the process of hardening the host systems before connecting to the network. The administrator wants to add protection to the boot loader to ensure the hosts are secure before the OS fully boots.
Which of the following would provide the BEST boot loader protection?
- A. TPM
- B. HSM
- C. PKI
- D. UEFI/BIOS
Answer: D
Explanation:
Reference: https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.security.doc/GUID-898217D4-689D-4EB5-866C-888353FE241C.html
NEW QUESTION 18
A company’s SOC has received threat intelligence about an active campaign utilizing a specific vulnerability. The company would like to determine whether it is vulnerable to this active campaign.
Which of the following should the company use to make this determination?
- A. Threat hunting
- B. A system penetration test
- C. Log analysis within the SIEM tool
- D. The Cyber Kill Chain
Answer: B
NEW QUESTION 19
A company has hired a security architect to address several service outages on the endpoints due to new malware. The Chief Executive Officer’s laptop was impacted while working from home. The goal is to prevent further endpoint disruption.
The edge network is protected by a web proxy.
Which of the following solutions should the security architect recommend?
- A. Replace the current antivirus with an EDR solution.
- B. Remove the web proxy and install a UTM appliance.
- C. Implement a deny list feature on the endpoints.
- D. Add a firewall module on the current antivirus solution.
Answer: C
NEW QUESTION 20
A security analyst is reviewing the following output:
Which of the following would BEST mitigate this type of attack?
- A. Installing a network firewall
- B. Placing a WAF inline
- C. Implementing an IDS
- D. Deploying a honeypot
Answer: A
NEW QUESTION 21
......
100% Valid and Newest Version CAS-004 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/CAS-004-exam-dumps.html (New 128 Q&As)