★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW NSE4_FGT-7.0 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/NSE4_FGT-7.0-dumps.html
It is more faster and easier to pass the Fortinet NSE4_FGT-7.0 exam by using Virtual Fortinet Fortinet NSE 4 - FortiOS 7.0 questuins and answers. Immediate access to the Leading NSE4_FGT-7.0 Exam and find the same core area NSE4_FGT-7.0 questions with professionally verified answers, then PASS your exam with a high score now.
Fortinet NSE4_FGT-7.0 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which statement about the IP authentication header (AH) used by IPsec is true?
- A. AH does not provide any data integrity or encryption.
- B. AH does not support perfect forward secrecy.
- C. AH provides data integrity bur no encryption.
- D. AH provides strong data integrity but weak encryption.
Answer: C
NEW QUESTION 2
Examine the exhibit, which contains a virtual IP and firewall policy configuration.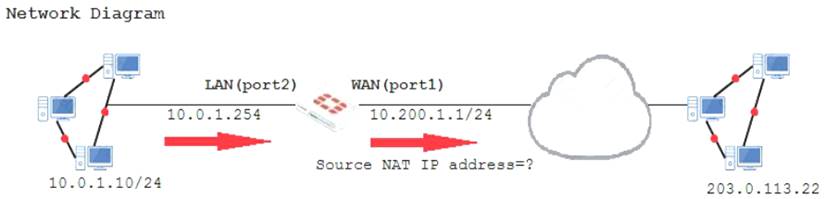
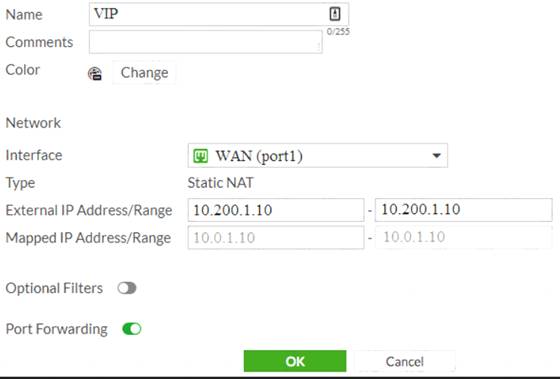
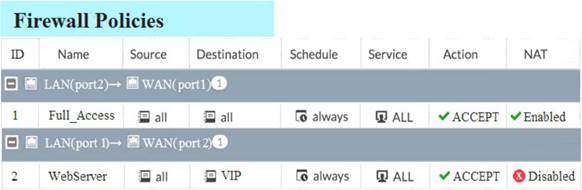
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
- A. 10.200.1.10
- B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24
- C. 10.200.1.1
- D. 10.0.1.254
Answer: A
Explanation:
https://help.fortinet.com/fos50hlp/54/Content/FortiOS/fortigate-firewall-52/Firewall%20Objects/Virtual%20IPs.
NEW QUESTION 3
A team manager has decided that, while some members of the team need access to a particular website, the majority of the team does not Which configuration option is the most effective way to support this request?
- A. Implement a web filter category override for the specified website
- B. Implement a DNS filter for the specified website.
- C. Implement web filter quotas for the specified website
- D. Implement web filter authentication for the specified website.
Answer: D
NEW QUESTION 4
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy.
Which two other security profiles can you apply to the security policy? (Choose two.)
- A. Antivirus scanning
- B. File filter
- C. DNS filter
- D. Intrusion prevention
Answer: AD
NEW QUESTION 5
Exhibit: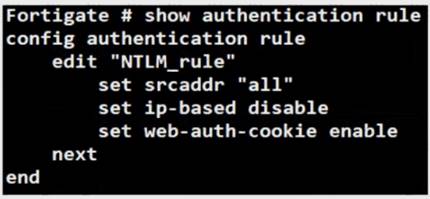
Refer to the exhibit to view the authentication rule configuration In this scenario, which statement is true?
- A. IP-based authentication is enabled
- B. Route-based authentication is enabled
- C. Session-based authentication is enabled.
- D. Policy-based authentication is enabled
Answer: C
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD45387
NEW QUESTION 6
Which two policies must be configured to allow traffic on a policy-based next-generation firewall (NGFW) FortiGate? (Choose two.)
- A. Firewall policy
- B. Policy rule
- C. Security policy
- D. SSL inspection and authentication policy
Answer: CD
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/38324/ngfw-policy-based-mode
NEW QUESTION 7
Refer to the exhibit to view the application control profile.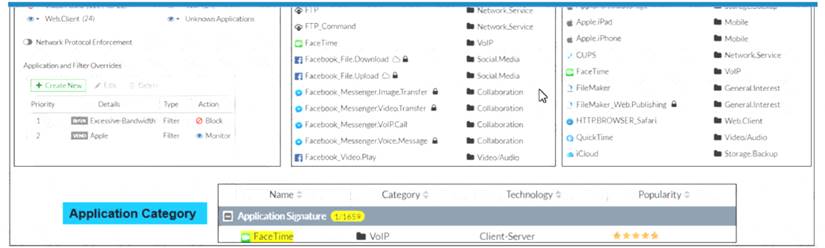
Based on the configuration, what will happen to Apple FaceTime?
- A. Apple FaceTime will be blocked, based on the Excessive-Bandwidth filter configuration
- B. Apple FaceTime will be allowed, based on the Apple filter configuration.
- C. Apple FaceTime will be allowed only if the filter in Application and Filter Overrides is set to Learn
- D. Apple FaceTime will be allowed, based on the Categories configuration.
Answer: A
NEW QUESTION 8
View the exhibit: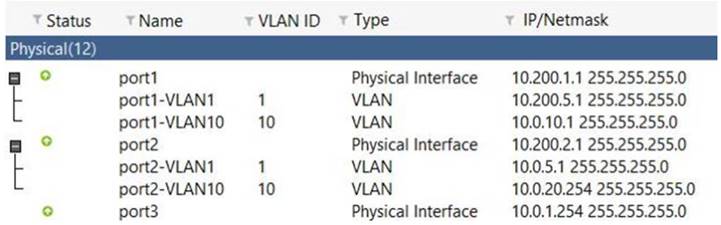
Which the FortiGate handle web proxy traffic rue? (Choose two.)
- A. Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
- B. port-VLAN1 is the native VLAN for the port1 physical interface.
- C. port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- D. Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
Answer: AC
NEW QUESTION 9
In an explicit proxy setup, where is the authentication method and database configured?
- A. Proxy Policy
- B. Authentication Rule
- C. Firewall Policy
- D. Authentication scheme
Answer: D
NEW QUESTION 10
Refer to the exhibit.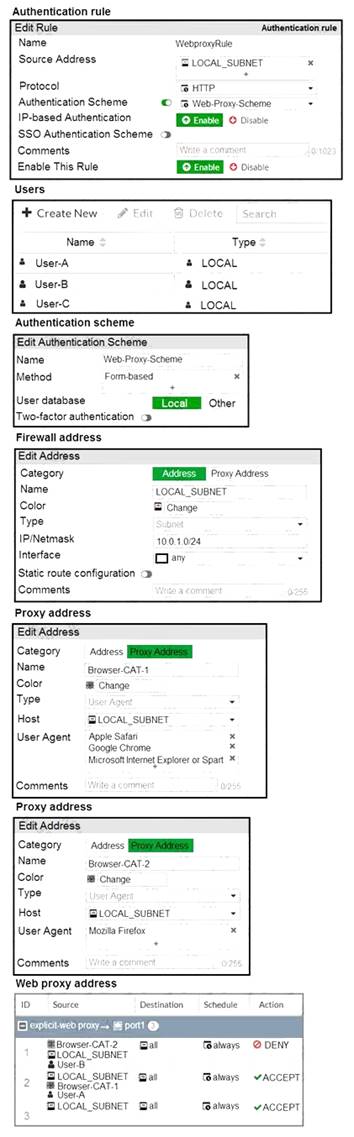
The exhibit shows proxy policies and proxy addresses, the authentication rule and authentication scheme, users, and firewall address.
An explicit web proxy is configured for subnet range 10.0.1.0/24 with three explicit web proxy policies. The authentication rule is configured to authenticate HTTP requests for subnet range 10.0.1.0/24 with a
form-based authentication scheme for the FortiGate local user database. Users will be prompted for
authentication.
How will FortiGate process the traffic when the HTTP request comes from a machine with the source IP 10.1.1.10 to the destination http://www.fortinet.com? (Choose two.)
- A. If a Mozilla Firefox browser is used with User-B credentials, the HTTP request will be allowed.
- B. If a Google Chrome browser is used with User-B credentials, the HTTP request will be allowed.
- C. If a Mozilla Firefox browser is used with User-A credentials, the HTTP request will be allowed.
- D. If a Microsoft Internet Explorer browser is used with User-B credentials, the HTTP request will be allowed.
Answer: BD
NEW QUESTION 11
Which two statements about SSL VPN between two FortiGate devices are true? (Choose two.)
- A. The client FortiGate requires a client certificate signed by the CA on the server FortiGate.
- B. The client FortiGate requires a manually added route to remote subnets.
- C. The client FortiGate uses the SSL VPN tunnel interface type to connect SSL VPN.
- D. Server FortiGate requires a CA certificate to verify the client FortiGate certificate.
Answer: CD
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.9/cookbook/266506/ssl-vpn-with-certificate-authentication
NEW QUESTION 12
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
- A. SSH
- B. HTTPS
- C. FTM
- D. FortiTelemetry
Answer: AB
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.4.0/hardening-your-fortigate/995103/buildingsecurity-into-fortios
NEW QUESTION 13
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
- A. The interface has been configured for one-arm sniffer.
- B. The interface is a member of a virtual wire pair.
- C. The operation mode is transparent.
- D. The interface is a member of a zone.
- E. Captive portal is enabled in the interface.
Answer: ABC
Explanation:
https://help.fortinet.com/fos50hlp/54/Content/FortiOS/fortigate-whats-new-54/Top_VirtualWirePair.htm
NEW QUESTION 14
Refer to the exhibit.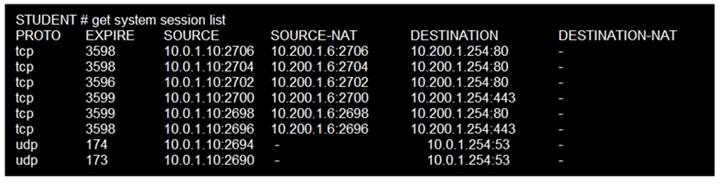
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
- A. Destination NAT is disabled in the firewall policy.
- B. One-to-one NAT IP pool is used in the firewall policy.
- C. Overload NAT IP pool is used in the firewall policy.
- D. Port block allocation IP pool is used in the firewall policy.
Answer: B
Explanation:
FortiGate_Security_6.4 page 155 . In one-to-one, PAT is not required.
NEW QUESTION 15
Which three statements about security associations (SA) in IPsec are correct? (Choose three.)
- A. Phase 2 SAs are used for encrypting and decrypting the data exchanged through the tunnel.
- B. An SA never expires.
- C. A phase 1 SA is bidirectional, while a phase 2 SA is directional.
- D. Phase 2 SA expiration can be time-based, volume-based, or both.
- E. Both the phase 1 SA and phase 2 SA are bidirectional.
Answer: ACD
NEW QUESTION 16
Refer to the exhibit.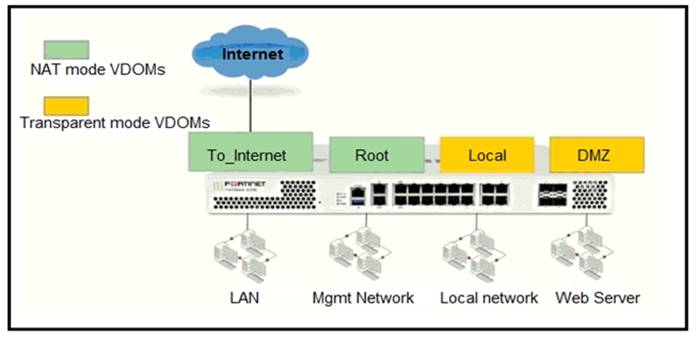
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem.
With this configuration, which statement is true?
- A. Inter-VDOM links are required to allow traffic between the Local and Root VDOMs.
- B. A static route is required on the To_Internet VDOM to allow LAN users to access the internet.
- C. Inter-VDOM links are required to allow traffic between the Local and DMZ VDOMs.
- D. Inter-VDOM links are not required between the Root and To_Internet VDOMs because the Root VDOM is used only as a management VDOM.
Answer: A
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD46542
NEW QUESTION 17
......
Thanks for reading the newest NSE4_FGT-7.0 exam dumps! We recommend you to try the PREMIUM Dumpscollection.com NSE4_FGT-7.0 dumps in VCE and PDF here: https://www.dumpscollection.net/dumps/NSE4_FGT-7.0/ (172 Q&As Dumps)