★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW NSE4_FGT-7.0 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/NSE4_FGT-7.0-dumps.html
Pass4sure NSE4_FGT-7.0 Questions are updated and all NSE4_FGT-7.0 answers are verified by experts. Once you have completely prepared with our NSE4_FGT-7.0 exam prep kits you will be ready for the real NSE4_FGT-7.0 exam without a problem. We have Abreast of the times Fortinet NSE4_FGT-7.0 dumps study guide. PASSED NSE4_FGT-7.0 First attempt! Here What I Did.
Online NSE4_FGT-7.0 free questions and answers of New Version:
NEW QUESTION 1
Which statement about video filtering on FortiGate is true?
- A. Full SSL Inspection is not required.
- B. It is available only on a proxy-based firewall policy.
- C. It inspects video files hosted on file sharing services.
- D. Video filtering FortiGuard categories are based on web filter FortiGuard categories.
Answer: B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/7.0.0/new-features/190873/video-filtering
NEW QUESTION 2
You have enabled logging on your FortiGate device for Event logs and all Security logs, and you have set up logging to use the FortiGate local disk.
What is the default behavior when the local disk is full?
- A. Logs are overwritten and the only warning is issued when log disk usage reaches the threshold of 95%.
- B. No new log is recorded until you manually clear logs from the local disk.
- C. Logs are overwritten and the first warning is issued when log disk usage reaches the threshold of 75%.
- D. No new log is recorded after the warning is issued when log disk usage reaches the threshold of 95%.
Answer: C
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.4.0/cli-reference/462620/log-disk-setting
NEW QUESTION 3
Which three statements are true regarding session-based authentication? (Choose three.)
- A. HTTP sessions are treated as a single user.
- B. IP sessions from the same source IP address are treated as a single user.
- C. It can differentiate among multiple clients behind the same source IP address.
- D. It requires more resources.
- E. It is not recommended if multiple users are behind the source NAT
Answer: ACD
NEW QUESTION 4
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source filed of a firewall policy?
- A. IP address
- B. Once Internet Service is selected, no other object can be added
- C. User or User Group
- D. FQDN address
Answer: B
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.5/cookbook/179236/using-internet-service-in-policy
NEW QUESTION 5
Which two statements are correct about SLA targets? (Choose two.)
- A. You can configure only two SLA targets per one Performance SLA.
- B. SLA targets are optional.
- C. SLA targets are required for SD-WAN rules with a Best Quality strategy.
- D. SLA targets are used only when referenced by an SD-WAN rule.
Answer: BD
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/382233/performance-sla-sla-targets
NEW QUESTION 6
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on which device?
- A. FortiManager
- B. Root FortiGate
- C. FortiAnalyzer
- D. Downstream FortiGate
Answer: B
NEW QUESTION 7
An administrator is running the following sniffer command: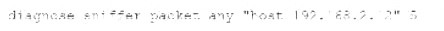
Which three pieces of Information will be Included in me sniffer output? {Choose three.)
- A. Interface name
- B. Packet payload
- C. Ethernet header
- D. IP header
- E. Application header
Answer: ABD
NEW QUESTION 8
Which of the following statements is true regarding SSL VPN settings for an SSL VPN portal?
- A. By default, FortiGate uses WINS servers to resolve names.
- B. By default, the SSL VPN portal requires the installation of a client’s certificate.
- C. By default, split tunneling is enabled.
- D. By default, the admin GUI and SSL VPN portal use the same HTTPS port.
Answer: D
NEW QUESTION 9
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
- A. The subject field in the server certificate
- B. The serial number in the server certificate
- C. The server name indication (SNI) extension in the client hello message
- D. The subject alternative name (SAN) field in the server certificate
- E. The host field in the HTTP header
Answer: ACD
Explanation:
Reference: https://checkthefirewall.com/blogs/fortinet/ssl-inspection
NEW QUESTION 10
Which two statements about antivirus scanning mode are true? (Choose two.)
- A. In proxy-based inspection mode, files bigger than the buffer size are scanned.
- B. In flow-based inspection mode, FortiGate buffers the file, but also simultaneously transmits it to the client.
- C. In proxy-based inspection mode, antivirus scanning buffers the whole file for scanning, before sending it to the client.
- D. In flow-based inspection mode, files bigger than the buffer size are scanned.
Answer: BC
Explanation:
An antivirus profile in full scan mode buffers up to your specified file size limit. The default is 10 MB. That is large enough for most files, except video files. If your FortiGate model has more RAM, you may be able to increase this threshold. Without a limit, very large files could exhaust the scan memory. So, this threshold balances risk and performance. Is this tradeoff unique to FortiGate, or to a specific model? No. Regardless of vendor or model, you must make a choice. This is because of the difference between scans in theory, that have no limits, and scans on real-world devices, that have finite RAM. In order to detect 100% of malware regardless of file size, a firewall would need infinitely large RAM—something that no device has in the real world. Most viruses are very small. This table shows a typical tradeoff. You can see that with the default 10 MB threshold, only 0.01% of viruses pass through.
NEW QUESTION 11
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
- A. FortiGate automatically negotiates different local and remote addresses with the remote peer.
- B. FortiGate automatically negotiates a new security association after the existing security association expires.
- C. FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
- D. FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
Answer: D
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=12069
NEW QUESTION 12
How do you format the FortiGate flash disk?
- A. Load a debug FortiOS image.
- B. Load the hardware test (HQIP) image.
- C. Execute the CLI command execute formatlogdisk.
- D. Select the format boot device option from the BIOS menu.
Answer: D
NEW QUESTION 13
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
* All traffic must be routed through the primary tunnel when both tunnels are up
* The secondary tunnel must be used only if the primary tunnel goes down
* In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover
Which two key configuration changes are needed on FortiGate to meet the design requirements? (Choose two,)
- A. Configure a high distance on the static route for the primary tunnel, and a lower distance on the static route for the secondary tunnel.
- B. Enable Dead Peer Detection.
- C. Configure a lower distance on the static route for the primary tunnel, and a higher distance on the static route for the secondary tunnel.
- D. Enable Auto-negotiate and Autokey Keep Alive on the phase 2 configuration of both tunnels.
Answer: BC
Explanation:
B - because the customer requires the tunnels to notify when a tunnel goes down. DPD is designed for that purpose. To send a packet over a firewall to determine a failover for the next tunnel after a specific amount of time of not receiving a response from its peer.
C - remember when it comes to choosing a route with regards to Administrative Distance. The route with the lowest distance for that particular route will be chosen. So, by configuring a lower routing distance on the primary tunnel, means that the primary tunnel will be chosen to route packets towards their destination.
NEW QUESTION 14
Which two statements about IPsec authentication on FortiGate are correct? (Choose two.)
- A. For a stronger authentication, you can also enable extended authentication (XAuth) to request the remote peer to provide a username and password
- B. FortiGate supports pre-shared key and signature as authentication methods.
- C. Enabling XAuth results in a faster authentication because fewer packets are exchanged.
- D. A certificate is not required on the remote peer when you set the signature as the authentication method.
Answer: AB
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/913287/ipsec-vpn-authenticating-aremote-fortigate
NEW QUESTION 15
Refer to the exhibit.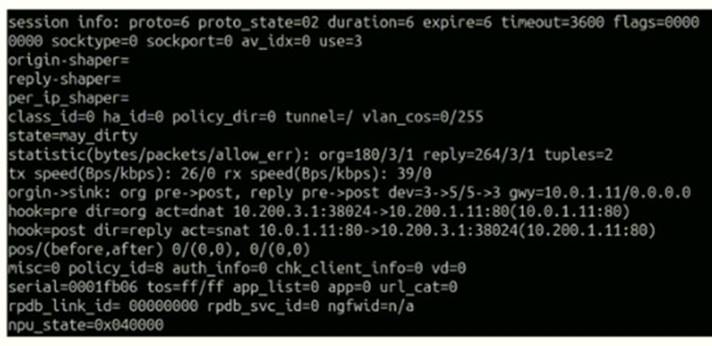
Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
- A. The session is in SYN_SENT state.
- B. The session is in FIN_ACK state.
- C. The session is in FTN_WAIT state.
- D. The session is in ESTABLISHED state.
Answer: A
Explanation:
Indicates TCP (proto=6) session in SYN_SENT state (proto=state=2) https://kb.fortinet.com/kb/viewContent.do?externalId=FD30042
NEW QUESTION 16
An administrator has configured two-factor authentication to strengthen SSL VPN access. Which additional best practice can an administrator implement?
- A. Configure Source IP Pools.
- B. Configure split tunneling in tunnel mode.
- C. Configure different SSL VPN realms.
- D. Configure host check.
Answer: D
NEW QUESTION 17
......
Thanks for reading the newest NSE4_FGT-7.0 exam dumps! We recommend you to try the PREMIUM Certshared NSE4_FGT-7.0 dumps in VCE and PDF here: https://www.certshared.com/exam/NSE4_FGT-7.0/ (172 Q&As Dumps)