★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GPEN Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GPEN-dumps.html
Your success in GIAC GPEN is our sole target and we develop all our GPEN braindumps in a way that facilitates the attainment of this target. Not only is our GPEN study material the best you can find, it is also the most detailed and the most updated. GPEN Practice Exams for GIAC GPEN are written to the highest standards of technical accuracy.
Online GPEN free questions and answers of New Version:
NEW QUESTION 1
In which layer of the OSI model does a sniffer operate?
- A. Network layer
- B. Session layer
- C. Presentation layer
- D. Data link layer
Answer: D
NEW QUESTION 2
What command will correctly reformat the Unix passwordcopy and shadowcopy Tiles for input to John The Ripper?
- A. /Un shadow passwd copy shadowcopy > johnfile
- B. /Unshadow passwdcopy shadowcopy > johnfile
- C. /Unshadow shadowcopy passwdcopy >john file
- D. /Unshadow passwdcopy shadowcopy > johnfile
Answer: C
Explanation:
Reference:
https://books.google.co.in/books?id=SC-tAwAAQBAJ&pg=PA286&lpg=PA286&dq=/Unshadow+shadow+copy+passwd+copy+%3Ej ohn+file&source=bl&ots=OnZK9atlc1&sig=co7EM5EHye96vO74W3wZxky3sXU&hl=en&sa =X&ei=FBuoVPLHDc-cugSDxYGYBA&ved=0CCwQ6AEwAg#v=onepage&q=%2FUnshadow%20shadow%20cop y%20passwd%20copy%20%3Ejohn%20file&f=false
NEW QUESTION 3
Which of the following standards is used in wireless local area networks (WLANs)?
- A. IEEE 802.4
- B. IEEE 802.3
- C. IEEE 802.11b
- D. IEEE 802.5
Answer: C
NEW QUESTION 4
Which of the following are considered Bluetooth security violations?
Each correct answer represents a complete solution. Choose two.
- A. Cross site scripting attack
- B. SQL injection attack
- C. Bluesnarfing
- D. Bluebug attack
- E. Social engineering
Answer: CD
NEW QUESTION 5
Ryan wants to create an ad hoc wireless network so that he can share some important files with another employee of his company. Which of the following wireless security protocols should he choose for setting up an ad hoc wireless network?
Each correct answer represents a part of the solution. Choose two.
- A. WPA2 -EAP
- B. WPA-PSK
- C. WPA-EAP
- D. WEP
Answer: BD
NEW QUESTION 6
Which of the following ports must you filter to check null sessions on your network?
- A. 139 and 445
- B. 111 and 222
- C. 1234 and 300
- D. 130 and 200
Answer: A
NEW QUESTION 7
Which of the following tools are used for footprinting?
Each correct answer represents a complete solution. Choose all that apply.
- A. Brutus
- B. Sam spade
- C. Whois
- D. Traceroute
Answer: BCD
NEW QUESTION 8
Which of the following tools is a wireless sniffer and analyzer that works on the Windows operating system?
- A. Void11
- B. Airsnort
- C. Kismet
- D. Aeropeek
Answer: D
NEW QUESTION 9
Peter, a malicious hacker, obtains e-mail addresses by harvesting them from postings, blogs, DNS listings, and Web pages. He then sends large number of unsolicited commercial e-mail (UCE) messages on these addresses. Which of the following e-mail crimes is Peter committing?
- A. E-mail Spam
- B. E-mail Storm
- C. E-mail spoofing
- D. E-mail bombing
Answer: A
NEW QUESTION 10
Which of the following is the second half of the LAN manager Hash?
- A. 0xAAD3B435B51404BB
- B. 0xAAD3B435B51404CC
- C. 0xAAD3B435B51404EE
- D. 0xAAD3B435B51404AA
Answer: C
NEW QUESTION 11
Which of the following is possible in some SQL injection vulnerabilities on certain types of databases that affects the underlying server OS?
- A. Database structure retrieval
- B. Shell command execution
- C. Data manipulation
- D. Data query capabilities
Answer: A
Explanation:
Reference:
http://www.darkmoreops.com/2014/08/28/use-sqlmap-sql-injection-hack-website-database/
NEW QUESTION 12
John works as a Professional Penetration Tester. He has been assigned a project to test the Website security of www.we-are-secure Inc. On the We-are-secure Website login page, he enters ='or''=' as a username and successfully logs on to the user page of the Web site. Now, John asks the we-are-secure Inc. to improve the login page PHP script. Which of the following suggestions can John give to improve the security of the we-are-secure Website login page from the SQL injection attack?
- A. Use the escapeshellarg() function
- B. Use the session_regenerate_id() function
- C. Use the mysql_real_escape_string() function for escaping input
- D. Use the escapeshellcmd() function
Answer: C
NEW QUESTION 13
You are concerned about attackers simply passing by your office, discovering your wireless network, and getting into your network via the wireless connection. Which of the following are
NOT steps in securing your wireless connection?
Each correct answer represents a complete solution. Choose two.
- A. Not broadcasting SSID
- B. MAC filtering on the router
- C. Strong password policies on workstation
- D. Using either WEP or WPA encryption
- E. Hardening the server OS
Answer: CE
NEW QUESTION 14
This is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards. The main features of these tools are as follows:
It displays the signal strength of a wireless network, MAC address, SSID, channel details, etc.
It is commonly used for the following purposes:
:a. War driving
:b. Detecting unauthorized access points
:c. Detecting causes of interference on a WLAN
:d. WEP ICV error tracking
:e. Making Graphs and Alarms on 802.11 Data, including Signal Strength
This tool is known as __________.
- A. Absinthe
- B. THC-Scan
- C. NetStumbler
- D. Kismet
Answer: C
NEW QUESTION 15
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He successfully performs a brute force attack on the We-are-secure server. Now, he suggests some countermeasures to avoid such brute force attacks on the We-aresecure server. Which of the following are countermeasures against a brute force attack?
Each correct answer represents a complete solution. Choose all that apply.
- A. The site should use CAPTCHA after a specific number of failed login attempt
- B. The site should restrict the number of login attempts to only three time
- C. The site should force its users to change their passwords from time to tim
- D. The site should increase the encryption key length of the passwor
Answer: AB
NEW QUESTION 16
__________ firewall architecture uses two NICs with a screening router inserted between the host and the untrusted network.
- A. packet filtering
- B. Screened host
- C. Dual homed host
- D. Screened subnet
Answer: B
NEW QUESTION 17
168.116.9 Is an IP address forvvww.scanned-server.com. Why are the results from the two scans, shown below, different?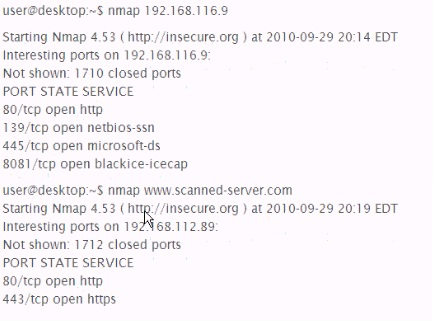
- A. John.pot
- B. John conf
- C. John.rec
- D. John.ini
Answer: C
NEW QUESTION 18
Which of the following best describes a server side exploit?
- A. Attack on the physical machine
- B. Attack of a service listening on a network port
- C. Attack that escalates user privilege to root or administrator
- D. Attack of a client application that retrieves content from the network
Answer: C
NEW QUESTION 19
......
Recommend!! Get the Full GPEN dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/GPEN/ (New 385 Q&As Version)