★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GPEN Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GPEN-dumps.html
Cause all that matters here is passing the GIAC GPEN exam. Cause all that you need is a high score of GPEN GIAC Certified Penetration Tester exam. The only one thing you need to do is downloading Certleader GPEN exam study guides now. We will not let you down with our money-back guarantee.
Check GPEN free dumps before getting the full version:
NEW QUESTION 1
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
- A. ICMP error message quoting
- B. Analyzing email headers
- C. Sniffing and analyzing packets
- D. Sending FIN packets to open ports on the remote system
Answer: BC
NEW QUESTION 2
Which of the following is a web ripping tool?
- A. Netcat
- B. NetBus
- C. SuperScan
- D. Black Widow
Answer: D
NEW QUESTION 3
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 Active Directory domain-based network. The domain consists of a domain controller, two Windows 2003 member servers, and one hundred client computers. The company employees use laptops with Windows XP Professional. These laptops are equipped with wireless network cards that are used to connect to access points located in the Marketing department of the company. The company employees log on to the domain by using a user name and password combination. The wireless network has been configured with WEP in addition to 802.1x. Mark wants to provide the best level of security for the kind of
authentication used by the company. What will Mark do to accomplish the task?
- A. Use EAP-TLS
- B. Use MD5
- C. Use PEAP
- D. Use IPSec
Answer: C
NEW QUESTION 4
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using the Linux operating system. He wants to use a wireless sniffer to sniff the We-are-secure network. Which of the following tools will he use to accomplish his task?
- A. NetStumbler
- B. Snadboy's Revelation
- C. WEPCrack
- D. Kismet
Answer: D
NEW QUESTION 5
Which of the following is the frequency range to tune IEEE 802.11a network?
- A. 1.15-3.825 GHz
- B. 5.15-5.825 GHz
- C. 5.25-9.825 GHz
- D. 6.25-9.825 GHz
Answer: B
NEW QUESTION 6
Which of the following tools is not a BlueSnarf attacking tool?
- A. Blooover
- B. Redsnarf
- C. BlueSnarfer
- D. Freejack
Answer: D
NEW QUESTION 7
Which of the following tools automates password guessing in the NetBIOS session?
- A. L0phtCrack
- B. John the Ripper
- C. Legion
- D. NTInfoScan
Answer: C
NEW QUESTION 8
You have obtained the hash below from the /etc/shadow file. What are you able to discern simply by looking at this hash? 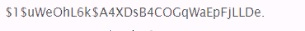
- A. A4XD$B4COCqWaEpFjLLD
- B. is a SHAI hash that was created using the salt $1 SuWeOhL6k$ 1
- C. A4XD$B4COCqWaEpFjLLD
- D. is an MD5 hash that was created using the salt $1 SuWeOhL6k$
- E. A4XDsB4COGqWaEpFjLLD
- F. is an MD5 hash that was created using the salt uWeOhL6k
- G. A4XDsB4COCqWaEpFjLLD
- H. is a SHAI hash that was created using the salt uweohL6k
Answer: C
NEW QUESTION 9
Which of the following Penetration Testing steps includes network mapping and OS fingerprinting?
- A. Gather information
- B. Exploit
- C. Verify vulnerabilities
- D. Planning stage
Answer: A
NEW QUESTION 10
John, a novice web user, makes a new E-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
- A. Brute Force attack
- B. Dictionary attack
- C. Hybrid attack
- D. Rule based attack
Answer: ABC
NEW QUESTION 11
When DNS is being used for load balancing, why would a penetration tester choose to identify a scan target by its IP address rather than its host name?
- A. Asingle IP may have multiple domain
- B. A single domain name can only have one IP addres
- C. Scanning tools only recognize IP addresses
- D. A single domain name may have multiple IP addresse
Answer: C
Explanation:
Reference: http://www.flashcardmachine.com/sec-midterm.html
NEW QUESTION 12
Your company has decided that the risk of performing a penetration test Is too great. You would like to figure out other ways to find vulnerabilities on their systems, which of the following is MOST likely to be a valid alternative?
- A. Network scope Analysis
- B. Baseline Data Reviews
- C. Patch Policy Review
- D. Configuration Reviews
Answer: A
NEW QUESTION 13
Which of the following tools can be used to enumerate networks that have blocked ICMP Echo packets, however, failed to block timestamp or information packet or not performing sniffing of trusted addresses, and it also supports spoofing and promiscuous listening for reply packets?
- A. Nmap
- B. Zenmap
- C. Icmpenum
- D. Nessus
Answer: C
NEW QUESTION 14
In which of the following attacks does an attacker use packet sniffing to read network traffic between two parties to steal the session cookie?
- A. Cross-site scripting
- B. Session sidejacking
- C. ARP spoofing
- D. Session fixation
Answer: B
NEW QUESTION 15
What does TCSEC stand for?
- A. Trusted Computer System Evaluation Criteria
- B. Target Computer System Evaluation Criteria
- C. Trusted Computer System Experiment Criteria
- D. Trusted Computer System Evaluation Center
Answer: A
NEW QUESTION 16
You want to retrieve the default security report of nessus. Which of the following google search queries will you use?
- A. link:pdf nessus "Assessment report"
- B. filetype:pdf nessus
- C. filetype:pdf "Assessment Report" nessus
- D. site:pdf nessus "Assessment report"
Answer: C
NEW QUESTION 17
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He enters the following command on the Linux terminal:chmod 741 secure.c
Considering the above scenario, which of the following statements are true?
Each correct answer represents a complete solution. Choose all that apply.
- A. John is restricting a guest to only write or execute the secure.c fil
- B. John is providing all rights to the owner of the fil
- C. By the octal representation of the file access permission, John is restricting the group members to only read the secure.c fil
- D. The textual representation of the file access permission of 741 will be -rwxr--rw-.
Answer: BC
NEW QUESTION 18
Analyze the screenshot below. What type of vulnerability is being attacked? 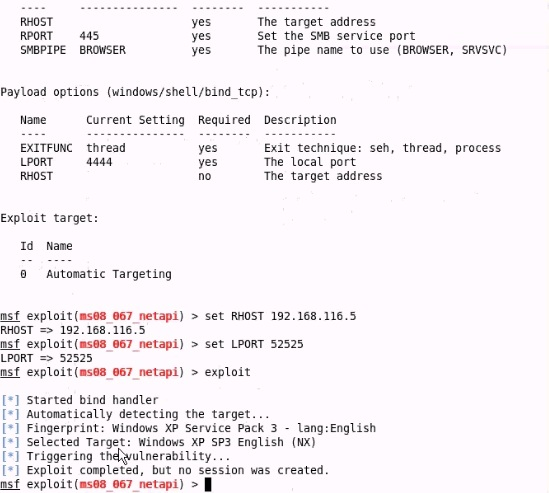
- A. Windows Server service
- B. Internet Explorer
- C. Windows Powershell
- D. Local Security Authority
Answer: B
NEW QUESTION 19
......
100% Valid and Newest Version GPEN Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/GPEN-dumps.html (New 385 Q&As)