★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GPEN Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GPEN-dumps.html
Act now and download your GIAC GPEN test today! Do not waste time for the worthless GIAC GPEN tutorials. Download Up to the immediate present GIAC GIAC Certified Penetration Tester exam with real questions and answers and begin to learn GIAC GPEN with a classic professional.
Check GPEN free dumps before getting the full version:
NEW QUESTION 1
Which of the following best describes a client side exploit?
- A. Attack of a client application that retrieves content from the network
- B. Attack that escalates user privileged to root or administrator
- C. Attack of a service listening on a client system
- D. Attack on the physical machine
Answer: C
NEW QUESTION 2
LM hash is one of the password schemes that Microsoft LAN Manager and Microsoft Windows versions prior to the Windows Vista use to store user passwords that are less than 15 characters long. If you provide a password seven characters or less, the second half of the LM hash is always __________.
- A. 0xAAD3B435B51404EE
- B. 0xBBD3B435B51504FF
- C. 0xBBC3C435C51504EF
- D. 0xAAD3B435B51404FF
Answer: A
NEW QUESTION 3
Which of the following is the correct sequence of packets to perform the 3-way handshake method?
- A. SYN, ACK, ACK
- B. SYN, ACK, SYN/ACK
- C. SYN, SYN/ACK, ACK
- D. SYN, SYN, ACK
Answer: C
NEW QUESTION 4
John works as a Penetration Tester in a security service providing firm named you-are-secure Inc.
Recently, John's company has got a project to test the security of a promotional Website www.missatlanta.com and assigned the pen-testing work to John. When John is performing penetration testing, he inserts the following script in the search box at the company home page:
<script>alert('Hi, John')</script>
After pressing the search button, a pop-up box appears on his screen with the text - "Hi, John."
Which of the following attacks can be performed on the Web site tested by john while considering the above scenario?
- A. Replay attack
- B. Buffer overflow attack
- C. CSRF attack
- D. XSS attack
Answer: D
NEW QUESTION 5
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com network. Now, when you have finished your penetration testing, you find that the weare- secure.com server is highly vulnerable to SNMP enumeration. You advise the we-are-secure Inc. to turn off SNMP; however, this is not possible as the company is using various SNMP services on its remote nodes. What other step can you suggest to remove SNMP vulnerability?
Each correct answer represents a complete solution. Choose two.
- A. Change the default community string name
- B. Install antiviru
- C. Close port TCP 53.
- D. Upgrade SNMP Version 1 with the latest versio
Answer: AD
NEW QUESTION 6
You work as a Penetration Tester for the Infosec Inc. Your company takes the projects of security auditing. Recently, your company has assigned you a project to test the security of the we-aresecure. com Website. The we-are-secure.com Web server is using Linux operating system. When you port scanned the we-are-secure.com Web server, you got that TCP port 23, 25, and 53 are open. When you tried to telnet to port 23, you got a blank screen in response. When you tried to type the dir, copy, date, del, etc. commands you got only blank spaces or underscores symbols on the screen. What may be the reason of such unwanted situation?
- A. The we-are-secure.com server is using honeypo
- B. The we-are-secure.com server is using a TCP wrappe
- C. The telnet service of we-are-secure.com has corrupte
- D. The telnet session is being affected by the stateful inspection firewal
Answer: B
NEW QUESTION 7
You have gained shell on a Windows host and want to find other machines to pivot to, but the rules of engagement state that you can only use tools that are already available. How could you find other machines on the target network?
- A. Use the "ping" utility to automatically discover other hosts
- B. Use the "ping" utility in a for loop to sweep the networ
- C. Use the "edit" utility to read the target's HOSTS fil
- D. Use the "net share" utility to see who is connected to local shared drive
Answer: B
Explanation:
Reference:
http://www.slashroot.in/what-ping-sweep-and-how-do-ping-sweep
NEW QUESTION 8
What is the sequence in which packets are sent when establishing a connection to a secured network?
- A. Auth, Associate and Probe
- B. Probe, Auth and Associate
- C. Associate, Probe and Auth
- D. Prob
- E. Associate and Auth
Answer: C
NEW QUESTION 9
Which of the following statements are true about session hijacking?
Each correct answer represents a complete solution. Choose all that apply.
- A. TCP session hijacking is when a hacker takes over a TCP session between two machine
- B. It is the exploitation of a valid computer session to gain unauthorized access to information or services in a computer syste
- C. Use of a long random number or string as the session key reduces session hijackin
- D. It is used to slow the working of victim's network resource
Answer: ABC
NEW QUESTION 10
What is the impact on pre-calculated Rainbow Tables of adding multiple salts to a set of passwords?
- A. Salts increases the time to crack the original password by increasing the number oftables that must be calculate
- B. Salts double the total size of a rainbow table databas
- C. Salts can be reversed or removed from encoding quickly to produce unsaltedhashe
- D. Salts have little effect because they can be calculated on the fly with applicationssuch as Ophcrac
Answer: B
NEW QUESTION 11
You want to run the nmap command that includes the host specification of 202.176.56-57.*. How many hosts will you scan?
- A. 1024
- B. 256
- C. 512
- D. 64
Answer: C
NEW QUESTION 12
Which of the following statements about Fport is true?
- A. It works as a process viewe
- B. It works as a datapipe on Window
- C. It works as a datapipe on Linu
- D. It is a source port forwarder/redirecto
Answer: A
NEW QUESTION 13
Which of the following tools is an example of HIDS?
- A. Anti-Spector
- B. Auditpol.exe
- C. Elsave
- D. Log File Monitor
Answer: D
NEW QUESTION 14
Analyze the screenshot below, which of the following sets of results will be retrieved using this search? 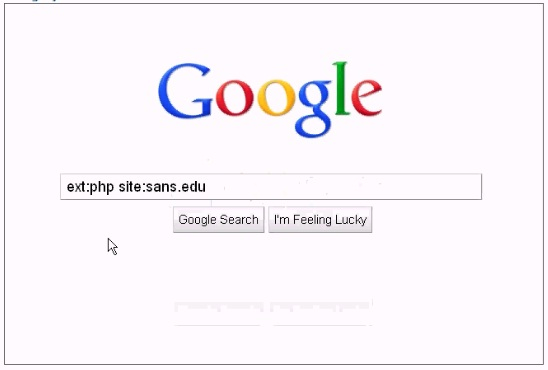
- A. Pages from the domain sans.edu that have external link
- B. Files of type .php from the domain sans.ed
- C. Pages that contain the term ext:php and slte.sans.ed
- D. Files of type .php that redirect to the sans.edu domai
Answer: A
NEW QUESTION 15
What section of the penetration test or ethical hacking engagement final report is used to detail and prioritize the results of your testing?
- A. Methodology
- B. Conclusions
- C. Executive Summary
- D. Findings
Answer: C
NEW QUESTION 16
Which of the following is a web ripping tool?
- A. Netcat
- B. NetBus
- C. SuperScan
- D. Black Widow
Answer: D
NEW QUESTION 17
Which of the following is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards and also detects wireless networks marking their relative position with a GPS?
- A. Ettercap
- B. Tcpdump
- C. Kismet
- D. NetStumbler
Answer: D
NEW QUESTION 18
You've been contracted by the owner of a secure facility to try and break into their office in the middle of the night. Your client requested photographs of any sensitive information found as proof of your accomplishments. The job you've been hired to perform is an example of what practice?
- A. Penetration Testing
- B. Ethical Hacking
- C. Vulnerability Assessing
- D. Security Auditing
Answer: B
NEW QUESTION 19
......
P.S. Dumpscollection.com now are offering 100% pass ensure GPEN dumps! All GPEN exam questions have been updated with correct answers: https://www.dumpscollection.net/dumps/GPEN/ (385 New Questions)