★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW NSE7_OTS-6.4 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/NSE7_OTS-6.4-dumps.html
Breathing of NSE7_OTS-6.4 practice question materials and exam answers for Fortinet certification for IT examinee, Real Success Guaranteed with Updated NSE7_OTS-6.4 pdf dumps vce Materials. 100% PASS Fortinet NSE 7 - OT Security 6.4 exam Today!
Online Fortinet NSE7_OTS-6.4 free dumps demo Below:
NEW QUESTION 1
Refer to the exhibit.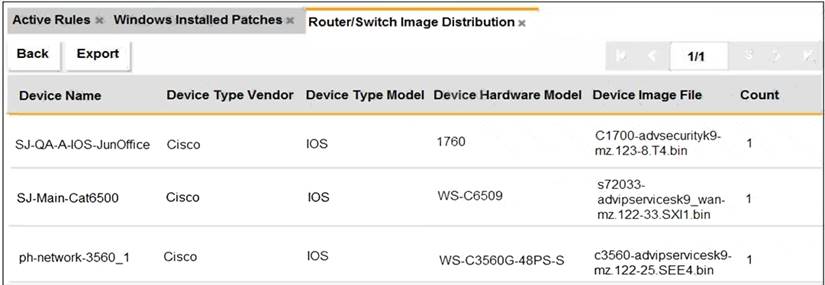
An OT administrator ran a report to identify device inventory in an OT network. Based on the report results, which report was run?
- A. A FortiSIEM CMDB report
- B. A FortiAnalyzer device report
- C. A FortiSIEM incident report
- D. A FortiSIEM analytics report
Answer: A
NEW QUESTION 2
An OT architect has deployed a Layer 2 switch in the OT network at Level 1 the Purdue model-process control. The purpose of the Layer 2 switch is to segment traffic between PLC1 and PLC2 with two VLANs. All the traffic between PLC1 and PLC2 must first flow through the Layer 2 switch and then through the FortiGate device in the Level 2 supervisory control network.
What statement about the traffic between PLC1 and PLC2 is true?
- A. The Layer 2 switch rewrites VLAN tags before sending traffic to the FortiGate device.
- B. The Layer 2 switches routes any traffic to the FortiGate device through an Ethernet link.
- C. PLC1 and PLC2 traffic must flow through the Layer-2 switch trunk link to the FortiGate device.
- D. In order to communicate, PLC1 must be in the same VLAN as PLC2.
Answer: C
NEW QUESTION 3
As an OT administrator, it is important to understand how industrial protocols work in an OT network. Which communication method is used by the Modbus protocol?
- A. It uses OSI Layer 2 and the primary device sends data based on request from secondary device.
- B. It uses OSI Layer 2 and both the primary/secondary devices always send data during the communication.
- C. It uses OSI Layer 2 and both the primary/secondary devices send data based on a matching token ring.
- D. It uses OSI Layer 2 and the secondary device sends data based on request from primary device.
Answer: D
NEW QUESTION 4
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
- A. Services defined in the firewall policy.
- B. Source defined as internet services in the firewall policy
- C. Lowest to highest policy ID number
- D. Destination defined as internet services in the firewall policy
- E. Highest to lowest priority defined in the firewall policy
Answer: ABD
NEW QUESTION 5
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
- A. Configure a fabric connector with a notification policy on FortiSIEM to connect with FortiGate.
- B. Create a notification policy and define a script/remediation on FortiSIEM.
- C. Define a script/remediation on FortiManager and enable a notification rule on FortiSIEM.
- D. Deploy a mitigation script on Active Directory and create a notification policy on FortiSIEM.
Answer: C
NEW QUESTION 6
Refer to the exhibit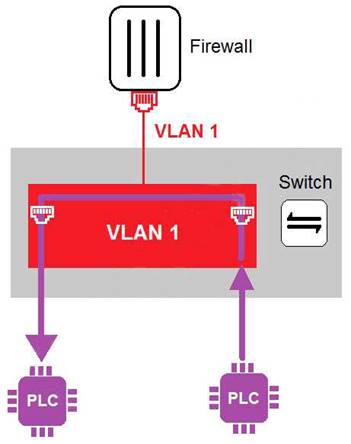
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going
through the firewall.
Which statement about the topology is true?
- A. PLCs use IEEE802.1Q protocol to communicate each other.
- B. An administrator can create firewall policies in the switch to secure between PLCs.
- C. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
- D. There is no micro-segmentation in this topology.
Answer: D
NEW QUESTION 7
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- A. You must set correct operator in event handler to trigger an event.
- B. You can automate SOC tasks through playbooks.
- C. Each playbook can include multiple triggers.
- D. You cannot use Windows and Linux hosts security events with FortiSoC.
Answer: BC
Explanation:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
NEW QUESTION 8
Refer to the exhibit.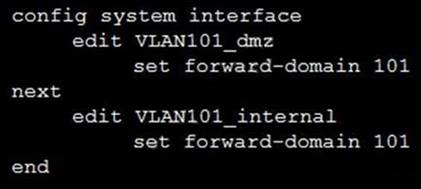
Given the configurations on the FortiGate, which statement is true?
- A. FortiGate is configured with forward-domains to reduce unnecessary traffic.
- B. FortiGate is configured with forward-domains to forward only domain controller traffic.
- C. FortiGate is configured with forward-domains to forward only company domain website traffic.
- D. FortiGate is configured with forward-domains to filter and drop non-domain controller traffic.
Answer: A
NEW QUESTION 9
Refer to the exhibit.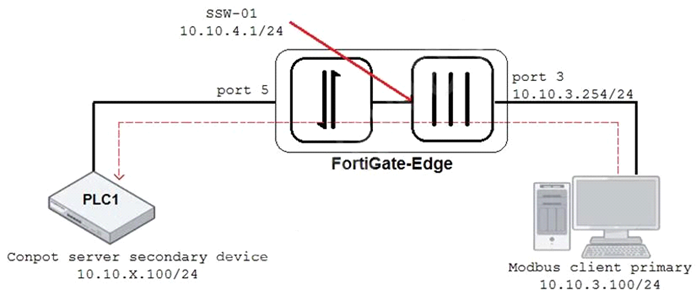
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
- A. The FortiGate-Edge device must be in NAT mode.
- B. NAT is disabled in the FortiGate firewall policy from port3 to ssw-01.
- C. The FortiGate devices is in offline IDS mode.
- D. Port5 is not a member of the software switch.
Answer: AC
NEW QUESTION 10
Which three common breach points can be found in a typical OT environment? (Choose three.)
- A. Global hat
- B. Hard hat
- C. VLAN exploits
- D. Black hat
- E. RTU exploits
Answer: CDE
NEW QUESTION 11
In a wireless network integration, how does FortiNAC obtain connecting MAC address information?
- A. RADIUS
- B. Link traps
- C. End station traffic monitoring
- D. MAC notification traps
Answer: A
NEW QUESTION 12
......
Thanks for reading the newest NSE7_OTS-6.4 exam dumps! We recommend you to try the PREMIUM Allfreedumps.com NSE7_OTS-6.4 dumps in VCE and PDF here: https://www.allfreedumps.com/NSE7_OTS-6.4-dumps.html (35 Q&As Dumps)