★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW H12-711_V3.0 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/H12-711_V3.0-dumps.html
Cause all that matters here is passing the HUAWEI H12-711_V3.0 exam. Cause all that you need is a high score of H12-711_V3.0 HCIA-Security V3.0 exam. The only one thing you need to do is downloading Passleader H12-711_V3.0 exam study guides now. We will not let you down with our money-back guarantee.
Free H12-711_V3.0 Demo Online For HUAWEI Certifitcation:
NEW QUESTION 1
About the packet iniptablesDescription of the transfer process, which of the following options is incorrect?
- A. When a packet enters the network card, it first goes to matchPREROUTINGchain
- B. If the destination address of the data packet is the local machine, the system will send the data packet toINPUTchain.
- C. If the destination address of the data packet is not the local machine, the system sends the data packet toOUTPUTchain
- D. If the destination address of the data packet is not the local machine, the system sends the data packet toFORWARDchain.
Answer: C
NEW QUESTION 2
In the process of digital signature, which of the following is mainly carried outHASHAlgorithms thereby verifying the integrity of data transmissions?
- A. User data
- B. Symmetric key
- C. Receiver's public key
- D. Receiver's private key
Answer: A
NEW QUESTION 3
Which of the following options are application risks (multiple choice)
- A. Internet virus
- B. Email Security
- C. Database system configuration security
- D. WEBservice security
Answer: ABCD
NEW QUESTION 4
Based on the HiSec solution, please drag the device on the left into the logical architecture layer on the right.[fill in the blank]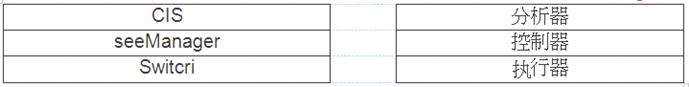
Solution:
CIS Analyzer, SecoManager Controller, Switch Actuator
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
aboutwindowslog, which of the following descriptions is false?
- A. System logs are used to record events generated by operating system components, mainly including crashes of drivers, system components and application software, and data
- B. windows server 2008The system logs are stored inApplication.evtxmiddle
- C. The application log contains events recorded by applications or system programs, mainly recording program operation events
- D. windows server 2008The security log is stored insecurity.evtxmiddle
Answer: B
NEW QUESTION 6
Security policy conditions can be divided into multiple fields, such as source address, destination address, source port, destination port, etc.
"and"That is to say, this policy is hit only if the information in the packet matches all fields.
- A. True
- B. False
Answer: B
NEW QUESTION 7
The attacker searches the ports currently open by the attacked object by scanning the ports to determine the attack mode. In port scanning attacks, attackers usually use Port Scan attack software to initiate a series of TCP/UDP connections, and determine whether the host uses these ports to provide services according to the response packets. Such network probing is called ______ scanning.[fill in the blank]*
Solution:
port
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
If there is no hard disk installed on the firewall, when a network intrusion event is found, the event will be recorded in the () log. (fill in the blank)
Solution:
Logbuffer
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 9
Which of the following is true about the difference between pre-incident prevention strategies and post-incident recovery strategies? (multiple choice)
- A. Prevention strategies focus on minimizing the likelihood of an accident before a story occur
- B. Recovery strategies focus on minimizing the impact and damage to the business after an incident
- C. The role of pre-disaster prevention strategies does not include minimizing economic and reputational losses caused by accidents
- D. Recovery strategies are used to improve business high availability
- E. A recovery strategy is part of a business continuity plan
Answer: ACD
NEW QUESTION 10
Which of the following DDoS attack types is an attack?
- A. snooping scan attack
- B. Malformed Packet Attack
- C. special packet attack
- D. traffic attack
Answer: D
NEW QUESTION 11
aboutNATAddress translation, which of the following statements is false?
- A. sourceNATconfiguration in technologyNATaddress pool, you can configure only one address poolIPaddress
- B. Address translation can be provided in the local area network according to the needs of usersFTP,WWW,Telnetand other services
- C. Some application layer protocols carry in the dataIPaddress information, make themNATWhen modifying the data in the upper layerIPAddress information
- D. for someTCP,UDPagreement (such asICMP,PPTP), cannot doNATconvert
Answer: D
NEW QUESTION 12
RFC (Request For Comment) 1918 reserves 3 IP addresses for private use, namely 10.0.0.0-10.255.255.255, _________, 192.168.0.0-192.168.255.255[fill in the blank]*
Solution:
* 172.16.0.0-172.31.255.255
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
The company administrator uses the ping command to test the connectivity of the network. If he needs to specify the source address of the ehco-request message, what are the additional parameters he needs?
- A. -i
- B. -a
- C. -C
- D. -f
Answer: C
NEW QUESTION 14
pass throughdisplay ike sa The results you see are as follows. Which of the following statements is false?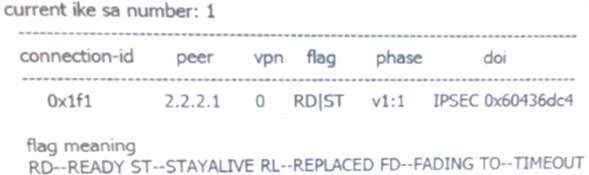
- A. IKE SAhas been established
- B. IPSec SAhas been established
- C. neighbor address is2.2.2.1
- D. IKEused isV1Version
Answer: B
NEW QUESTION 15
Which of the following is true about firewall security policies?
- A. By default, the security policy can control unicast packets and broadcast packets
- B. By default, the security policy can control multicast
- C. By default, the security policy only controls unicast packets.
- D. By default, the security policy can control unicast packets, broadcast packets, and multicast packets.
Answer: C
NEW QUESTION 16
......
Thanks for reading the newest H12-711_V3.0 exam dumps! We recommend you to try the PREMIUM 2passeasy H12-711_V3.0 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/H12-711_V3.0/ (492 Q&As Dumps)