★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW H12-711_V3.0 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/H12-711_V3.0-dumps.html
Exam Code: H12-711_V3.0 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: HCIA-Security V3.0
Certification Provider: HUAWEI
Free Today! Guaranteed Training- Pass H12-711_V3.0 Exam.
Free H12-711_V3.0 Demo Online For HUAWEI Certifitcation:
NEW QUESTION 1
Which of the following is not an asymmetric encryption algorithm?
- A. DH
- B. MD5
- C. DSA
- D. RSA
Answer: B
NEW QUESTION 2
aboutwindowsDescription of the firewall advanced settings, which of the following options is wrong? (multiple choice)
- A. When setting the stacking rules, only the local port can be restricted, and the remote port cannot be restricted
- B. When setting the stacking rules, you can restrict both the local port and the remote port.
- C. When setting the stacking rule, only the local port can be restricted, and the remote port cannot be restricted
- D. When setting the stacking rules, you can restrict both the local port and the remote port.
Answer: BD
NEW QUESTION 3
Which of the following does not belong toP2DRin the modelDetectionThe method used in the link?
- A. real time monitoring
- B. detect
- C. Call the police
- D. shut down service
Answer: D
NEW QUESTION 4
aboutSSL VPNTechnology, which of the following statements is false?
- A. SSL VPNtechnology can be perfectly adapted toNATthrough the scene
- B. SSL VPNThe encryption of the technology only takes effect at the application layer
- C. SSL VPNRequires a dial-up client
- D. SSL VPNTechnology expands the reach of the enterprise's network
Answer: C
NEW QUESTION 5
aboutIPSec SA, which of the following statements is correct?
- A. IPSec SAis unidirectional
- B. IPSec SAis bidirectional
- C. Used to generate encryption keys
- D. Used to generate secret algorithms
Answer: A
NEW QUESTION 6
Which of the following descriptions of the firewall log is wrong?
- A. The log level Emergency is the most severe level
- B. Alert log level indicates a major abnormality of the device, requiring immediate action
- C. According to the severity level or urgency of the informatio
- D. The log can be divided into 8 level
- E. Themore serious the information, the greater the log level value.
- F. The ebug log level indicates that it is general information about the normal operation of the device, and the user does not need to pay attention
Answer: D
NEW QUESTION 7
In the TCP/P protocol core, which of the following protocols works at the application layer? ( )[Multiple choice]*
- A. IGMP
- B. ICMP
- C. RIP
- D. ARP
Answer: C
NEW QUESTION 8
Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution.[fill in the blank]*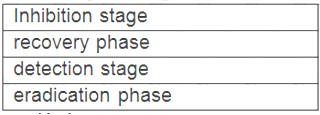
Solution:
3142
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 9
Which of the following options is correct for the description of a buffer overflow attack? (multiple choice)
- A. Buffer overflow attacks exploit the flaws of software systems in memory operations to run attack code with high operating privileges
- B. Buffer overflow attacks have nothing to do with the vulnerabilities and architecture of the operating system
- C. Buffer overflow attacks are one of the most common ways to attack the behavior of software systems
- D. Buffer overflow attacks are application-layer attacks
Answer: ACD
NEW QUESTION 10
aboutHRPWhich of the following options is not included in the content of the master/slave configuration consistency check?
- A. NATStrategy
- B. Whether the heartbeat interface with the same sequence number is configured
- C. The next hop and outgoing interface of the static route
- D. Authentication Policy
Answer: C
NEW QUESTION 11
When the company's network administrator is performing dual-system hot backup, due to the possibility of inconsistent round-trip paths, if he wants to enable the session fast backup function, the command that needs to be entered is _______ [fill in the blank]*
Solution:
hrp mirror session enable
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
Company network administrator allocation. After the dual-system hot backup is set, run the command to check VRRP and other information, and get the following information
HRP_M<FWA>
Gigabi tEtherneto/0/3 Virtual Router 1 State: Master
Virtual IP: 10.3.0.3
Master IP: 10.3.0.1
PriorityRun: 120 PriorityConfig:100 MasterPriority: 120
Preempt: YESDelay Time: 0 s TimerRun: 60s
TimerConfig: 60s Auth type: NONE
Virtual MAC: 0000-5e00-0101
Check TIL: YES
Config type:vgmp Vrrp Backup-torward: disabled
Create time:2020-03-17 17:35:54 UTC08:02
Last change time: 2020-03-22 16:01:56 UTC08:02
Ask him to type the view command in the blank space is _____
[fill in the blank]*
Solution:
display vrrp
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
Which of the following options is notUSG6000What file formats are supported by serial devices for saving certificates?
- A. PKCS#12
- B. DER
- C. PEM
- D. PKCS#
Answer: D
NEW QUESTION 14
Which of the following options arePKIComponents of the architecture? (multiple choice)
- A. end entity
- B. Certificate Authority
- C. Certificate Registration Authority
- D. certificate store
Answer: ABCD
NEW QUESTION 15
The protocol number of the transport layer protocol TCP is ( ) (fill in the blank)
Solution:
6
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
......
P.S. 2passeasy now are offering 100% pass ensure H12-711_V3.0 dumps! All H12-711_V3.0 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/H12-711_V3.0/ (492 New Questions)