★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GSNA Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GSNA-dumps.html
Proper study guides for Up to the immediate present GIAC GIAC Systems and Network Auditor certified begins with GIAC GSNA preparation products which designed to deliver the Printable GSNA questions by making you pass the GSNA test at your first time. Try the free GSNA demo right now.
GIAC GSNA Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
You are concerned about an attacker being able to get into your network. You want to make sure that you are informed of any network activity that is outside normal parameters. What is the best way to do this?
- A. Utilize protocol analyzers.
- B. User performance monitors.
- C. Implement signature based antivirus.
- D. Implement an anomaly based IDS.
Answer: D
Explanation:
An anomaly based Intrusion Detection System will monitor the network for any activity that is outside normal parameters (i.e. an anomaly) and inform you of it. Answer C is incorrect. Antivirus software, while important, won't help detect the activities of intruders. Answer B is incorrect. Performance monitors are used to measure normal network activity and look for problems such as bottlenecks. Answer A is incorrect. A protocol analyzer does detect if a given protocol is moving over a particular network segment.
NEW QUESTION 2
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to set the user login features on the systems with the shadow passwords. Which of the following Unix configuration files can you use to accomplish the task?
- A. /etc/logrotate.conf
- B. /etc/login.defs
- C. /etc/magic
- D. /etc/filesystems
Answer: B
Explanation:
In Unix, the /etc/login.defs file is used by system administrators to set the user login features on the systems with the shadow passwords. Answer A is incorrect. In Unix, the /etc/logrotate.conf file configures the logrotate program used for managing log files. Answer C is incorrect. In Unix, the /etc/magic file contains the descriptions of various file formats for the file command. Answer D is incorrect. In Unix, the /etc/filesystems file is used to set the filesystem probe order when filesystems are mounted with the auto option.
NEW QUESTION 3
Which of the following mechanisms is closely related to authorization?
- A. Sending secret data such as credit card information.
- B. Allowing access to a particular resource.
- C. Verifying username and password.
- D. Sending data so that no one can alter it on the way.
Answer: B
Explanation:
Authorization is a process that verifies whether a user has permission to access a Web resource. A Web server can restrict access to some of its resources to only those clients that log in using a recognized username and password. To be authorized, a user must first be authenticated. Answer C is incorrect. Verifying username and password describes the mechanism of authentication. Authentication is the process of verifying the identity of a user. This is usually done using a user name and password. This process compares the provided user name and password with those stored in the database of an authentication server. Answer D is incorrect. Sending data so that no one can alter it on the way describes the mechanism of data integrity. Data integrity is a mechanism that ensures that the data is not modified during transmission from source to destination. This means that the data received at the destination should be exactly the same as that sent from the source. Answer A is incorrect. Sending secret data such as credit card information describes the mechanism of confidentiality. Confidentiality is a mechanism that ensures that only the intendeA, Duthorized recipients are able to read data. The data is so encrypted that even if an unauthorized user gets access to it, he will not get any meaning out of it.
NEW QUESTION 4
You are concerned about possible hackers doing penetration testing on your network as a prelude to an attack. What would be most helpful to you in finding out if this is occurring?
- A. Examining your antivirus logs
- B. Examining your domain controller server logs
- C. Examining your firewall logs
- D. Examining your DNS Server logs
Answer: C
Explanation:
Firewall logs will show all incoming and outgoing traffic. By examining those logs, you can do port scans and use other penetration testing tools that have been used on your firewall.
NEW QUESTION 5
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to do RARP mapping from hardware mapping addresses to IP addresses. Which of the following Unix configuration files can you use to accomplish the task?
- A. /etc/dhcpd.conf
- B. /etc/motd
- C. /etc/exports
- D. /etc/ethers
Answer: D
Explanation:
In Unix, the /etc/ethers file is used by system administrators for RARP mapping from hardware mapping addresses to IP addresses.
Answer A is incorrect. In Unix, the /etc/dhcpd.conf file is the configuration file for the DHCP server daemon. Answer C is incorrect. In Unix, the /etc/exports file describes exported file systems for NFS services. Answer B is incorrect. In Unix, the /etc/motd file automatically displays the message of the day after a successful login.
NEW QUESTION 6
You work as a professional Ethical Hacker. You are assigned a project to perform blackbox testing of the security of www.we-are-secure.com. Now you want to perform banner grabbing to retrieve information about the Webserver being used by we-are-secure. Which of the following tools can you use to accomplish the task?
- A. Wget
- B. WinSSLMiM
- C. Whisker
- D. httprint
Answer: D
Explanation:
According to the scenario, you want to perform banner grabbing to retrieve information about the Webserver being used by we-are-secure. For this, you will use the httprint tool to accomplish the task. httprint is a fingerprinting tool that is based on Web server characteristics to accurately identify Web servers. It works even when Web server may have been obfuscated by changing the server banner strings, or by plug-ins such as mod_security or servermask. It can also be used to detect Web enabled devices that do not contain a server banner string, such as wireless access points, routers, switches, cable modems, etc. httprint uses text signature strings for identification, and an attacker can also add signatures to the signature database. Answer A is incorrect. Wget is a Website copier that is used to analyze the vulnerabilities of a Website offline. Answer C is incorrect. Whisker is an HTTP/Web vulnerability scanner that is written in the PERL language. Whisker runs on both the Windows and UNIX environments. It provides functions for testing HTTP servers for many known security holes, particularly the presence of dangerous CGIs. Answer B is incorrect. WinSSLMiM is an HTTPS Man in the Middle attacking tool. It includes FakeCert, a tool used to make fake certificates. It can be used to exploit the Certificate Chain vulnerability in Internet Explorer. The tool works under Windows 9x/2000. Which of the following tools can be used to automate the MITM attack? A. Airjack B. Kismet C. Hotspotter D. IKECrack Answer A
Airjack is a collection of wireless card drivers and related programs. It uses a program called monkey_jack that is used to automate the MITM attack. Wlan_jack is a DoS tool in the set of airjack tools, which accepts a target source and BSSID to send continuous deauthenticate frames to a single client or an entire network. Another tool, essid_jack is used to send a disassociate frame to a target client in order to force the client to reassociate with the network and giving up the network SSID. Answer C is incorrect. Hotspotter is a wireless hacking tool that is used to detect rogue access point. It fools users to connect, and authenticate with the hacker's tool. It sends the deauthenticate frame to the victim's computer that causes the victim's wireless connection to be switched to a non- preferred connection. Answer D is incorrect. IKECrack is an IKE/IPSec authentication crack tool, which uses brute force for searching password and key combinations of Pre- Shared-Key authentication networks. The IKECrack tool undermines the latest Wi-Fi security protocol with repetitive attempts at authentication with random passphrases or keys. Answer B is incorrect. Kismet is a Linux-based 802.11 wireless network sniffer and intrusion detection system. It can work with any wireless card that supports raw monitoring (rfmon) mode. Kismet can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet can be used for the following tasks: To identify networks by passively collecting packets To detect standard named networks To detect masked networks To collect the presence of non-beaconing networks via data traffic
NEW QUESTION 7
Which of the following statements about invalidating a session is true?
- A. The getCreationTime() method can be called on an invalidated session.
- B. The invalidate() method belongs to the HttpServletRequest interface.
- C. A session can be invalidated programmatically as well as using the deployment descriptor.
- D. The getAttribute(String name) method throws an IllegalArgumentException if called on an invalidated session.
Answer: C
Explanation:
An existing session can be invalidated in the following two ways: Setting timeout in the deployment descriptor: This can be done by specifying timeout between the <session-timeout> tags as follows: <session-config> <session-timeout> 10 </session- timeout> </session-config> This will set the time for session timeout to be ten minutes. Setting timeout programmatically: This will set the timeout for a specific session. The syntax for setting the timeout programmatically is as follows: session.setMaxInactiveInterval(10*60) In this method, the timeout is specified in seconds. Hence, this will set the time for the session timeout to be ten minutes. Answer A is incorrect. The getCreationTime() method returns the time when the session was created. The time is measured in milliseconds since midnight January 1, 1970. This method throws an IllegalStateException if it is called on an invalidated session. Answer D is incorrect. The getAttribute(String name) method of the HttpSession interface returns the value of the named attribute as an object. It returns a null value if no attribute with the given name is bound to the session. This method throws an IllegalStateException if it is called on an invalidated session. Answer B is incorrect. The invalidate() method belongs to the HttpSession interface.
NEW QUESTION 8
The employees of CCN Inc. require remote access to the company's proxy servers. In order to provide solid wireless security, the company uses LEAP as the authentication protocol. Which of the following is supported by the LEAP protocol?
- A. Dynamic key encryption
- B. Public key certificate for server authentication
- C. Strongest security level
- D. Password hash for client authentication
Answer: AD
Explanation:
LEAP can use only password hash as the authentication technique. Not only LEAP, but EAP-TLS, EAP-TTLS, and PEAP also support dynamic key encryption and mutual authentication. Answer C is incorrect. LEAP provides only a moderate level of security. Answer B is incorrect. LEAP uses password hash for server authentication.
NEW QUESTION 9
You have been assigned a project to develop a Web site for a construction company. You plan to develop a Web site and want to get more control over the appearance and presentation of the Web pages. You also want to increase your ability to precisely specify the position and appearance of the elements on a page and create special effects. You plan to use cascading style sheets (CSS). You want to define styles only for the active page. Which type of style sheet will you use?
- A. Embedded Style Sheet
- B. Inline Style Sheet
- C. Internal Style Sheet
- D. External Style Sheet
Answer: A
Explanation:
To define styles only for the active page you should use embedded style sheet. Cascading style sheets (CSS) are used so that the Web site authors can exercise greater control on the appearance and presentation of their Web pages. And also because they increase the ability to precisely point to the location and look of elements on a Web page and help in creating special effects. Cascading Style Sheets have codes, which are interpreteA, Dpplied by the browser on to the Web pages and their elements. There are three types of cascading style sheets. External Style Sheets Embedded Style Sheets Inline
Style Sheets External Style Sheets are used whenever consistency in style is required throughout a Web site. A typical external style sheet uses a .css file extension, which can be edited using a text editor such as a Notepad. Embedded Style Sheets are used for defining styles for an active page. Inline Style Sheets are used for defining individual elements of a page. Reference: TechNet, Contents: Microsoft Knowledgebase, February 2000 issue PSS ID Number: Q179628 You want to enable Host A to access the Internet. For this, you need to configure the default gateway settings. Choose the appropriate address to accomplish the task.
NEW QUESTION 10
In which of the following techniques does an attacker take network traffic coming towards a host at one port and forward it from that host to another host?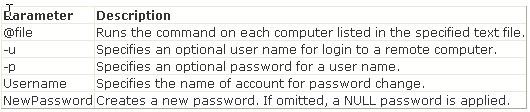
- A. Snooping
- B. UDP port scanning
- C. Firewalking
- D. Port redirection
Answer: D
Explanation:
Port redirection is a technique by which an attacker takes network traffic coming towards a host at one port and redirects it from that host to another host. For example, tools such as Fpipe and Datapipe are port redirection tools that accept connections at any specified port and resend them to other specified ports on specified hosts. For example, the following command establishes a listener on port 25 on the test system and then redirects the connection to port 80 on the target system using the source port of 25. C.\>fpipe -l 25 -s 25 -r 80 IP_address Answer C is incorrect. Firewalking is a technique for gathering information about a remote network protected by a firewall. This technique can be used effectively to perform information gathering attacks. In this technique, an attacker sends a crafted packet with a TTL value that is set to expire one hop past the firewall. If the firewall allows this crafted packet through, it forwards the packet to the next hop. On the next hop, the packet expires and elicits an ICMP "TTL expired in transit" message to the attacker. If the firewall does not allow the traffic, there should be no response, or an ICMP "administratively prohibited" message should be returned to the attacker. A malicious attacker can use firewalking to determine the types of ports/protocols that can bypass the firewall. To use firewalking, the attacker needs the IP address of the last known gateway before the firewall and the IP address of a host located behind the firewall. The main drawback of this technique is that if an administrator blocks ICMP packets from leaving the network, it is ineffective. Answer A is incorrect. Snooping is an activity of observing the content that appears on a computer monitor or watching what a user is typing. Snooping also occurs by using software programs to remotely monitor activity on a computer or network device. Hackers or attackers use snooping techniques and equipment such as keyloggers to monitor keystrokes, capture passwords and login information, and to intercept e-mail and other private communications. Sometimes, organizations also snoop their employees legitimately to monitor their use of organizations' computers and track Internet usage. Answer B is incorrect. In UDP port scanning, a UDP packet is sent to each port of the target system. If the remote port is closed, the server replies that the remote port is unreachable. If the remote Port is open, no such error is generated. Many firewalls block the TCP port scanning, at that time the UDP port scanning may be useful. Certain IDS and firewalls can detect UDP port scanning easily.
NEW QUESTION 11
Which of the following statements are true about data aggregation?
- A. A common aggregation purpose is to get more information about particular groups based on specific variables.
- B. Data aggregation cannot be user-based.
- C. Data aggregation is any process in which information is gathered and expressed in a summary form.
- D. Online analytic processing (OLAP) is a simple type of data aggregation.
Answer: ACD
Explanation:
Data aggregation is any process in which information is gathered and expressed in a summary form, for purposes such as statistical analysis. A common aggregation purpose is to get more information about particular groups based on specific variables such as age, profession, or income. The information about such groups can then be used for Web site personalization to choose content and advertising likely to appeal to an individual belonging to one or more groups for which data has been collected. For example, a site that sells music CDs might advertise certain CDs based on the age of the user and the data aggregate for their age group. Online analytic processing (OLAP) is a simple type of data aggregation in which the marketer uses an online reporting mechanism to process the information. Answer B is incorrect. Data aggregation can be user-based. Personal data aggregation services offer the user a single point for collection of their personal information from other Web sites. The customer uses a single master personal identification number (PIN) to give them access to their various accounts (such as those for financial institutions, airlines, book and music clubs, and so on). Performing this type of data aggregation is sometimes referred to as "screen scraping."
NEW QUESTION 12
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the
forest is Windows Server 2003. The company has recently provided laptops to its sales team members. You have configured access points in the network to enable a wireless network. The company's security policy states that all users using laptops must use smart cards for authentication. Which of the following authentication techniques will you use to implement the security policy of the company?
- A. IEEE 802.1X using EAP-TLS
- B. IEEE 802.1X using PEAP-MS-CHAP
- C. Pre-shared key
- D. Open system
Answer: A
Explanation:
In order to ensure that the laptop users use smart cards for authentication, you will have to configure IEEE 802.1X authentication using the EAP-TLS protocol on the network.
NEW QUESTION 13
You have detected what appears to be an unauthorized wireless access point on your network. However this access point has the same MAC address as one of your real access points and is broadcasting with a stronger signal. What is this called?
- A. Buesnarfing
- B. The evil twin attack
- C. WAP cloning
- D. DOS
Answer: B
Explanation:
In the evil twin attack, a rogue wireless access point is set up that has the same MAC address as one of your legitimate access points. That rogue WAP will often then initiate a denial of service attack on your legitimate access point making it unable to respond to users, so they are redirected to the 'evil twin'. Answer A is incorrect. Blue snarfing is the process of taking over a PD Answer D is incorrect. A DOS may be used as part of establishing an evil twin, but this attack is not specifically for denial of service. Answer C is incorrect. While you must clone a WAP MAC address, the attack is not called WAP cloning.
NEW QUESTION 14
You are the Network Admin for a company. You are concerned about users having access to items they should not. Your concern is that they may inadvertently have been granted access to those resources. When conducting a user access and rights review, which of the following is most likely to show you such unintentional granting of user rights?
- A. IDS Logs
- B. Access Control Lists
- C. Server logs
- D. Group Membership
Answer: D
Explanation:
Most often user rights are determined by the groups the user belongs to. In some cases a user may mistakenly be added to a group they should not be. It is also common that a user moves within the organization, but is still retained in their previous group giving them those rights. Answer B is incorrect. Access Control Lists are usually setup up manually. This means that a person would not likely be inadvertently added. You might want to check the ACL's, and you might find some issues, but this is not the most likely way to find users with inappropriate rights. Answer C is incorrect. At best server logs can show you if a user accessed a resource. But a user could have access to a resource, and simply not have used that access yet. Answer A is incorrect. IDS logs will only help you identify potential attacks. Unless you suspect the user of intentionally trying to break into resources, an IDS log will not help in this scenario.
NEW QUESTION 15
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He performs Web vulnerability scanning on the We- are-secure server. The output of the scanning test is as follows: C.\whisker.pl -h target_IP_address -- whisker / v1.4.0 / rain forest puppy / www.wiretrip.net -- = - = - = - = -
= = Host: target_IP_address = Server: Apache/1.3.12 (Win32) ApacheJServ/1.1 mod_ssl/2.6.4 OpenSSL/0.9.5a mod_perl/1.22 + 200 OK: HEAD /cgi-bin/printenv John recognizes /cgi-bin/printenv vulnerability ('Printenv' vulnerability) in the We_are_secure server. Which of the following statements about 'Printenv' vulnerability are true?
- A. With the help of 'printenv' vulnerability, an attacker can input specially crafted links and/or other malicious scripts.
- B. 'Printenv' vulnerability maintains a log file of user activities on the Website, which may be useful for the attacker.
- C. The countermeasure to 'printenv' vulnerability is to remove the CGI script.
- D. This vulnerability helps in a cross site scripting attack.
Answer: ACD
Explanation:
'Printenv' vulnerability allows an attacker to input specially crafted links and/or other malicious scripts. For example, http://www/cgi-bin/printenv/<script>alert (An attacker can misuse it!)</script> Since 'printenv' is just an example CGI script (It comes with various versions of the Apache Web server.) that has no real use and has its own problems, there is no problem in removing it. Answer B is incorrect. 'Printenv' does not maintain any log file of user activities.
NEW QUESTION 16
Mike works as a Network Engineer for XYZ CORP. The company has a multi-platform network. Recently, the company faced lots of blended threat issues that lead to several drastic attacks. Mike has been assigned a project to manage the resources and services of the company through both Intranet and Internet to protect the company from these attacks. Mike needs a system that provides auto-discovering and network topology building features to allow him to keep an intuitive view of the IT infrastructure. What will Mike use to meet the requirement of the project?
- A. eBox
- B. dopplerVUe
- C. David system
- D. EM7
Answer: C
Explanation:
David system is a network management system that allows a user to manage the resources and services through both Intranet and Internet. It provides auto- discovering and network topology building features to facilitate in keeping an intuitive view of the IT infrastructure. The resources, real-time monitoring, and accessibility of historical data facilitate reaction to failures. Configured interfaces for monitored devices permit a user to focus on the most important aspects of their work. Answer B is incorrect. dopplerVUe is a network management tool that facilitates network discovery, mapping, alerts and alarm management, and bandwidth management system. It enables monitoring of Ping, SNMP, syslog, and WMI performance metrics. It can also be used to monitor IPv6 devices, as well as services such as DNS, http, and email. Answer A is incorrect. eBox is an open source distribution and web development framework. This framework is used to manage server application configuration. It is based on Ubuntu Linux. It is projected to manage services in a computer network. The modular design of eBox allows a user to pick and choose the services. Answer D is incorrect. EM7 is a network monitoring system that is used to measure IT infrastructure health and performance. It is an NMS integrated system. It is designed to help in optimizing the performance and availability of the networks, systems, and applications. It facilitates trouble-ticketing, event management, reporting, IP management, DNS, and monitoring.
NEW QUESTION 17
......
P.S. Dumps-files.com now are offering 100% pass ensure GSNA dumps! All GSNA exam questions have been updated with correct answers: https://www.dumps-files.com/files/GSNA/ (368 New Questions)