★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GSNA Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GSNA-dumps.html
Virtual of GSNA exam price materials and test engine for GIAC certification for IT examinee, Real Success Guaranteed with Updated GSNA pdf dumps vce Materials. 100% PASS GIAC Systems and Network Auditor exam Today!
Free demo questions for GIAC GSNA Exam Dumps Below:
NEW QUESTION 1
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows: Which of the following tools is John using to crack the wireless encryption keys?
- A. Cain
- B. PsPasswd
- C. Kismet
- D. AirSnort
Answer: D
Explanation:
AirSnort is a Linux-based WLAN WEP cracking tool that recovers encryption keys. AirSnort operates by passively monitoring transmissions. It uses Ciphertext Only Attack and captures approximately 5 to 10 million packets to decrypt the WEP keys. Answer C is incorrect. Kismet is an IEEE 802.11 wireless network sniffer and intrusion detection system.
NEW QUESTION 2
You work as a professional Ethical Hacker. You are assigned a project to test the security of www.we-are-secure.com. You are working on the Windows Server 2003 operating system. You suspect that your friend has installed the keyghost keylogger onto your computer. Which of the following countermeasures would you employ in such a situation?
- A. Use commercially available anti-keyloggers such as PrivacyKeyboard.
- B. Use on-screen keyboards and speech-to-text conversion software which can also be useful against keyloggers, as there are no typing or mouse movements involved.
- C. Remove the SNMP agent or disable the SNMP service.
- D. Monitor the programs running on the server to see whether any new process is runningon the server or not.
Answer: ABD
Explanation:
It is very hard to detect a keylogger's activity. Hence, a Network Administrator should take the following steps as countermeasures against software keyloggers: Actively monitor the programs running on the server. Monitor the network whenever an application attempts to make a network connection. Use commercially available anti-keyloggers, such as PrivacyKeyboard. Update one's antivirus regularly. Use on-screen keyboards and speech-to-text conversion software which can also be useful against keyloggers, as there are no typing or mouse movements involved.
Answer C is incorrect. An SNMP service is not used for keystroke logging. Hence, removing an SNMP agent may be a valid option if, and only if, the server is vulnerable to SNMP enumeration.
NEW QUESTION 3
John works as a contract Ethical Hacker. He has recently got a project to do security checking for www.we-are-secure.com. He wants to find out the operating system of the we- are-secure server in the information gathering step. Which of the following commands will he use to accomplish the task? (Choose two)
- A. nc 208.100.2.25 23
- B. nmap -v -O www.we-are-secure.com
- C. nc -v -n 208.100.2.25 80
- D. nmap -v -O 208.100.2.25
Answer: BD
Explanation:
According to the scenario, John will use "nmap -v -O 208.100.2.25" to detect the operating system of the we-are-secure server. Here, -v is used for verbose and -O is used for TCP/IP fingerprinting to guess the remote operating system. John may also use the DNS name of we-are-secure instead of using the IP address of the we-are-secure server. So, he can also use the nmap command "nmap -v -O www.we-are-secure.com ". Answer C is incorrect. "nc -v -n 208.100.2.25 80" is a Netcat command, which is used to banner grab for getting information about the
NEW QUESTION 4
Which of the following NFS mount options specifies whether a program using a file via an NFS connection should stop and wait for the server to come back online, if the host serving the exported file system is unavailable, or if it should report an error?
- A. intr
- B. hard or soft
- C. nfsvers=2 or nfsvers=3
- D. fsid=num
Answer: B
Explanation:
The hard or soft NFS mount options are used to specify whether a program using a file via an NFS connection should stop and wait (hard) for the server to come back online, if the host serving the exported file system is unavailable, or if it should report an error. Answer A is incorrect. The intr NFS mount option allows NFS requests to be interrupted if the server goes down or cannot be reached. Answer C is incorrect. The nfsvers=2 or nfsvers=3 NFS mount options are used to specify which version of the NFS protocol to use. Answer D is incorrect. The fsid=num NFS mount option forces the file handle and file attributes settings on the wire to be num.
NEW QUESTION 5
You want to repeat the last command you entered in the bash shell. Which of the following commands will you use?
- A. history ##
- B. history !#
- C. history !!
- D. history !1
Answer: C
Explanation:
The history !! command shows the previously entered command in the bash shell. In the bash shell, the history command is used to view the recently executed commands. History is on by default. A user can turn off history using the command set +o history and turn it on using set -o history. An environment variable HISTSIZE is used to inform bash about how many history lines should be kept. The following commands are frequently used to view
and manipulate history: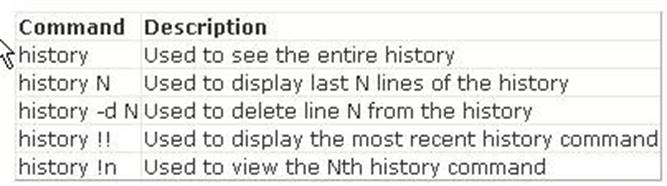
Answer B is incorrect. The history !# command shows the entire command line typed. Answer D is incorrect. The history !n command shows the nth command typed. Since n is equal to 1 in this command, the first command will be shown. Answer A is incorrect. It is not a valid command.
NEW QUESTION 6
A Cisco router can have multiple connections to networks. These connections are known as interfaces for Cisco Routers. For naming each interface, Cisco generally uses the type of interface as part of the name. Which of the following are true about the naming conventions of Cisco Router interfaces?
- A. An interface connected to a serial connection always starts with an S.
- B. An interface connected to a Token Ring segment always starts with To.
- C. An Ethernet interface that is fast always starts with an F.
- D. An interface connected to an Ethernet segment of the network always starts with an En.
Answer: ABC
Explanation:
A Cisco router can have multiple connections to networks. These connections are known as interfaces for Cisco Routers. For naming each interface, Cisco generally uses the type of interface as part of the name. Following are some of the naming conventions of Cisco Router interfaces: An Ethernet interface that is fast always starts with an F. An interface connected to a serial connection always starts with an S. An interface connected to an Ethernet segment of the network always starts with an E. An interface connected to a Token Ring segment always starts with To.
NEW QUESTION 7
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
- A. Implement WPA
- B. Implement WEP
- C. Don't broadcast SSID
- D. Implement MAC filtering
Answer: C
Explanation:
By not broadcasting your SSID some simple war driving tools won't detect your network. However you should be aware that there are tools that will still detect networks that are not broadcasting their SSID across your network. Answer D is incorrect. While MAC filtering may help prevent a hacker from accessing your network, it won't keep him or her from finding your network.
NEW QUESTION 8
Which of the following is the most secure place to host a server that will be accessed publicly through the Internet?
- A. A DNS Zone
- B. An Intranet
- C. A stub zone
- D. A demilitarized zone (DMZ)
Answer: D
Explanation:
A demilitarized zone (DMZ) is the most secure place to host a server that will be accessed publicly through the Internet. Demilitarized zone (DMZ) or perimeter network is a small network that lies in between the Internet and a private network. It is the boundary between the Internet and an internal network, usually a combination of firewalls and bastion hosts that are gateways between inside networks and outside networks. DMZ provides a large enterprise network or corporate network the ability to use the Internet while still maintaining its security. Answer B is incorrect. Hosting a server on the intranet for public access will not be good from a security point of view.
NEW QUESTION 9
You work as a Network Administrator for NetTech Inc. Your computer has the Windows 2000 Server operating system. You want to harden the security of the server. Which of the following changes are required to accomplish this? (Choose two)
- A. Remove the Administrator account.
- B. Disable the Guest account.
- C. Rename the Administrator account.
- D. Enable the Guest account.
Answer: BC
Explanation:
For security, you will have to rename the Administrator account and disable the Guest account. Renaming the Administrator account will ensure that hackers do not break into the network or computer by guessing the password of the Administrator account. You can also create a fake Administrator account that has no privileges and audit its use to detect attacks. Disabling the Guest account will prevent users who do not have a domain or local user account from illegally accessing the network or computer. By default, the Guest account is disabled on systems running Windows 2000 Server. If the Guest account is enabled, you will have to disable it.
NEW QUESTION 10
You run the wc -c file1.txt command. If this command displays any error message, you want to store the error message in the error.txt file. Which of the following commands will you use to accomplish the task?
- A. wc -c file1.txt >>error.txt
- B. wc -c file1.txt 1>error.txt
- C. wc -c file1.txt 2>error.txt
- D. wc -c file1.txt >error.txt
Answer: C
Explanation:
According to the scenario, you will use the wc -c file1.txt 2>error.txt command to accomplish the task. The 2> operator is an error redirector, which, while running a command, redirects the error (if it exists) on the specified file. Answer B, D are incorrect. The > or 1> redirector can be used to redirect the output of the wc -c file1.txt file to the error.txt file; however, you want to write the errors in the error.txt file, not the whole output. Answer A is incorrect. The >> operator will redirect the output of the command in the same manner as the > or 1> operator. Although the >> operator will not overwrite the error.txt file, it will append the error.txt file.
NEW QUESTION 11
You work as a Network Administrator for XYZ CORP. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory- based single forest single domain network. You have installed a Windows Server 2008 computer. You have configured auditing on this server. The client computers of the company use the Windows XP Professional operating system. You want to audit each event that is related to a user managing an account in the user database on the computer
where the auditing is configured. To accomplish the task, you have enabled the Audit account management option on the server. Which of the following events can be audited by enabling this audit option?
- A. Access to an Active Directory object
- B. Change of password for a user account
- C. Addition of a user account to a group
- D. Creation of a user account
Answer: BCD
Explanation:
Audit account management is one of the nine audit settings that can be configured on a Windows computer. This option is enabled to audit each event that is related to a user managing an account in the user database on the computer where the auditing is configured. These events include the following: Creating a user account Adding a user account to a group Renaming a user account Changing password for a user account This option is also used to audit the changes to the domain account of the domain controllers.
NEW QUESTION 12
Sam works as a Network Administrator for XYZ CORP. The computers in the company run Windows Vista operating system, and they are continuously connected to the Internet. This makes the network of the company susceptible to attacks from unauthorized users. Which of the following will Sam choose to protect the network of the company from such attacks?
- A. Firewall
- B. Windows Defender
- C. Software Explorer
- D. Quarantined items
Answer: A
Explanation:
A firewall is a set of related programs configured to protect private networks connected to the Internet from intrusion. It is used to regulate the network traffic between different computer networks. It permits or denies the transmission of a network packet to its destination based on a set of rules. A firewall is often installed on a separate computer so that an incoming packet does not get into the network directly. Answer B is incorrect. Windows Defender is a software product designed by Microsoft to provide continuous security against malware. If it detects anything suspicious, an alert will appear on the screen. Windows Defender can also be used to scan a computer for suspicious software. It can remove or quarantine any malware or spyware it finds. Answer C is incorrect. Software Explorer is a tool of Windows Defender. It is used to remove, enable, or disable the programs running on a computer. Answer D is incorrect. Quarantined items is a tool of Windows Defender. It is used to remove or restore a program blocked by Windows Defender.
NEW QUESTION 13
Which of the following commands is most useful for viewing large files?
- A. cat
- B. less
- C. touch
- D. cp
Answer: B
Explanation:
The less command is most useful for viewing large files. The less command displays the output of a file one page at a time. Viewing large files through cat may take more time to scroll pages, so it is better to use the less command to see the content of large files. Answer A is incorrect. The cat command is also used to view the content of a file, but it is most useful for viewing short files. Answer D is incorrect. The cp command is used to copy files and directories from one location to another. Answer C is incorrect. The touch command is not used to view the content of a file. It is used to create empty files or to update file timestamps.
NEW QUESTION 14
Samantha works as a Web Developer for XYZ CORP. She is designing a Web site for the company. In a Web page, she uses the HTTP-EQUIV attribute to control the page cache. Which of the following HTTP-EQUIV values controls the page cache in the browser folder?
- A. Window-target
- B. Status-code
- C. Content-type
- D. Pragma
Answer: D
Explanation:
HTTP-EQUIV is an attribute of the META tag. It sets or retrieves information used to bind the META tag's content to an HTTP response header. The pragma value of HTTP-EQUIV controls the page cache.
NEW QUESTION 15
Which of the following wireless security features provides the best wireless security mechanism?
- A. WEP
- B. WPA with 802.1X authentication
- C. WPA
- D. WPA with Pre Shared Key
Answer: B
Explanation:
WPA with 802.1X authentication provides best wireless security mechanism. 802.1X authentication, also known as WPA-Enterprise, is a security mechanism for wireless networks. 802.1X provides port-based authentication, which involves communications between a supplicant, authenticator, and authentication server. The supplicant is often software on a client device, the authenticator is a wired Ethernet switch or wireless access point, and an authentication server is generally a RADIUS database. The authenticator acts like a security guard to a protected network. The supplicant (client device) is not allowed access through the authenticator to the protected side of the network until the supplicant's identity is authorized. With 802.1X port-based authentication, the supplicant provides credentials, such as user name/password or digital certificate, to the authenticator, and the authenticator forwards the credentials to the authentication server for verification. If the credentials are valid, the supplicant (client device) is allowed to access resources located on the protected side of the network.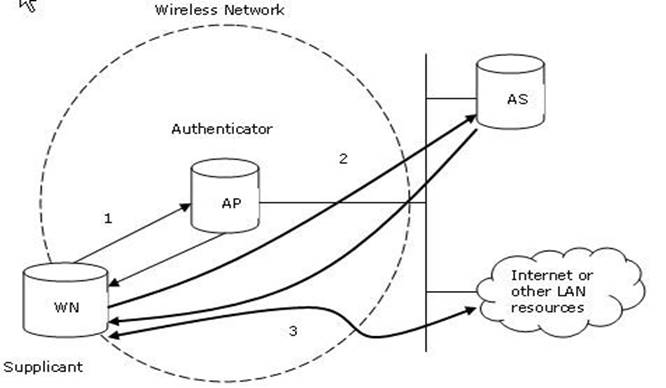
Answer A is incorrect. Wired equivalent privacy (WEP) uses the stream cipher RC4 (Rivest Cipher). WEP uses the Shared Key Authentication, since both the access point and the wireless device possess the same key. Attacker with enough Initialization Vectors can crack the key used and gain full access to the network. Answer D is incorrect. WPA-PSK is a strong encryption where encryption keys are automatically changed (called rekeying) and authenticated between devices after a fixed period of time, or after a fixed number of packets has been transmitted. Answer C is incorrect. WAP uses TKIP (Temporal Key Integrity Protocol) to enhance data encryption, but still vulnerable to different password
cracking attacks.
NEW QUESTION 16
You are the Security Consultant and you frequently do vulnerability assessments on client computers. You want to have a standardized approach that would be applicable to all of your clients when doing a vulnerability assessment. What is the best way to do this?
- A. Utilize OVAL.
- B. Create your own standard and use it with all clients.
- C. Utilize each client's security policies when doing a vulnerability assessment for that client.
- D. Utilize the Microsoft security recommendations.
Answer: A
Explanation:
Open Vulnerability Assessment Language (OVAL) is a common language for security professionals to use when checking for the presence of vulnerabilities on computer systems. OVAL provides a baseline method for performing vulnerability assessments on local computer systems. Answer D is incorrect. While Microsoft security standards will be appropriate for many of your clients, they won't help clients using Linux, Macintosh, or Unix. They also won't give you insight into checking your firewalls or routers. Answer C is incorrect. This would not fulfill the requirement of having a standardized approach applicable to all clients. B is incorrect. This would not be the best way. You should use common industry standards, like OVAL.
NEW QUESTION 17
......
100% Valid and Newest Version GSNA Questions & Answers shared by DumpSolutions.com, Get Full Dumps HERE: https://www.dumpsolutions.com/GSNA-dumps/ (New 368 Q&As)