★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW 156-215.81 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/156-215.81-dumps.html
It is more faster and easier to pass the CheckPoint 156-215.81 exam by using 100% Correct CheckPoint Check Point Certified Security Administrator R81 questuins and answers. Immediate access to the Far out 156-215.81 Exam and find the same core area 156-215.81 questions with professionally verified answers, then PASS your exam with a high score now.
Online CheckPoint 156-215.81 free dumps demo Below:
NEW QUESTION 1
What are the three types of UserCheck messages?
- A. inform, ask, and block
- B. block, action, and warn
- C. action, inform, and ask
- D. ask, block, and notify
Answer: A
Explanation:
Inform User Inform
Shows when the action for the ruleClosed is inform. It informs users what the company policy is for that site. Blocked Message
Block
Shows when a request is blocked. Ask User
Ask
Shows when the action for the rule is ask. It informs users what the company policy is for that site and they must click OK to continue to the site.
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_DataLossPrevention_AdminGuide/
NEW QUESTION 2
The SmartEvent R80 Web application for real-time event monitoring is called:
- A. SmartView Monitor
- B. SmartEventWeb
- C. There is no Web application for SmartEvent
- D. SmartView
Answer: B
NEW QUESTION 3
Which tool is used to enable cluster membership on a Gateway?
- A. SmartUpdate
- B. cpconfig
- C. SmartConsole
- D. sysconfig
Answer: B
Explanation:
References:
NEW QUESTION 4
Which type of Check Point license ties the package license to the IP address of the Security Management Server?
- A. Central
- B. Corporate
- C. Local
- D. Formal
Answer: A
Explanation:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=
NEW QUESTION 5
Which one of the following is TRUE?
- A. Ordered policy is a sub-policy within another policy
- B. One policy can be either inline or ordered, but not both
- C. Inline layer can be defined as a rule action
- D. Pre-R80 Gateways do not support ordered layers
Answer: C
NEW QUESTION 6
Which of the following is NOT an option to calculate the traffic direction?
- A. Incoming
- B. Internal
- C. External
- D. Outgoing
Answer: D
NEW QUESTION 7
To quickly review when Threat Prevention signatures were last updated, which Threat Tool would an administrator use?
- A. Protections
- B. IPS Protections
- C. Profiles
- D. ThreatWiki
Answer: B
NEW QUESTION 8
Which of the following is NOT an identity source used for Identity Awareness?
- A. Remote Access
- B. UserCheck
- C. AD Query
- D. RADIUS
Answer: B
NEW QUESTION 9
Rugged appliances are small appliances with ruggedized hardware and like Quantum Spark appliance they use which operating system?
- A. Centos Linux
- B. Gaia embedded
- C. Gaia
- D. Red Hat Enterprise Linux version 5
Answer: B
Explanation:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=
NEW QUESTION 10
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?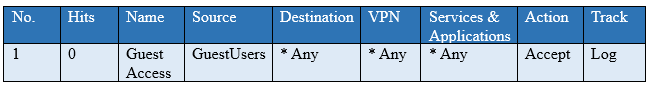
- A. Right click Accept in the rule, select “More”, and then check “Enable Identity Captive Portal”
- B. On the firewall object, Legacy Authentication screen, check “Enable Identity Captive Portal”
- C. In the Captive Portal screen of Global Properties, check “Enable Identity Captive Portal”
- D. On the Security Management Server object, check the box “Identity Logging”
Answer: A
NEW QUESTION 11
R80.10 management server can manage gateways with which versions installed?
- A. Versions R77 and higher
- B. Versions R76 and higher
- C. Versions R75.20 and higher
- D. Version R75 and higher
Answer: B
NEW QUESTION 12
Which of the following describes how Threat Extraction functions?
- A. Detect threats and provides a detailed report of discovered threats
- B. Proactively detects threats
- C. Delivers file with original content
- D. Delivers PDF versions of original files with active content removed
Answer: B
NEW QUESTION 13
When configuring LDAP User Directory integration, Changes applied to a User Directory template are:
- A. Reflected immediately for all users who are using template.
- B. Not reflected for any users unless the local user template is changed.
- C. Reflected for all users who are using that template and if the local user template is changed as well.
- D. Not reflected for any users who are using that template.
Answer: A
Explanation:
The users and user groups are arranged on the Account Unit in the tree structure of the LDAP server. User management in User Directory is external, not local. You can change the User Directory templates. Users associated with this template get the changes immediately. You can change user definitions manually in SmartDashboard, and the changes are immediate on the server.
NEW QUESTION 14
After the initial installation on Check Point appliance, you notice that the Management interface and default gateway are incorrect. Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
- A. set interface Mgmt ipv4-address 192.168.80.200 mask-length 24set static-route default nexthop gateway address 192.168.80.1 onsave config
- B. add interface Mgmt ipv4-address 192.168.80.200 255.255.255.0add static-route 0.0.0.0.0.0.0.0 gw 192.168.80.1 onsave config
- C. set interface Mgmt ipv4-address 192.168.80.200 255.255.255.0add static-route 0.0.0.0.0.0.0.0 gw 192.168.80.1 onsave config
- D. add interface Mgmt ipv4-address 192.168.80.200 mask-length 24add static-route default nexthop gateway address 192.168.80.1 onsave config
Answer: A
NEW QUESTION 15
Fill in the blank: By default, the SIC certificates issued by R80 Management Server are based on the _______ algorithm.
- A. SHA-256
- B. SHA-200
- C. MD5
- D. SHA-128
Answer: A
NEW QUESTION 16
Your internal networks 10.1.1.0/24, 10.2.2.0/24 and 192.168.0.0/16 are behind the Internet Security Gateway. Considering that Layer 2 and Layer 3 setup is correct, what are the steps you will need to do in SmartConsole in order to get the connection working?
- A. 1. Define an accept rule in Security Policy.2. Define Security Gateway to hide all internal networks behind the gateway’s external IP.3. Publish and install the policy.
- B. 1. Define an accept rule in Security Policy.2. Define automatic NAT for each network to NAT the networks behind a public IP.3. Publish the policy.
- C. 1. Define an accept rule in Security Policy.2. Define automatic NAT for each network to NAT the networks behind a public IP.3. Publish and install the policy.
- D. 1. Define an accept rule in Security Policy.2. Define Security Gateway to hide all internal networks behind the gateway’s external IP.3. Publish the policy.
Answer: C
NEW QUESTION 17
URL Filtering cannot be used to:
- A. Control Bandwidth issues
- B. Control Data Security
- C. Improve organizational security
- D. Decrease legal liability
Answer: D
Explanation:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_SecurityManagement_AdminGuide
NEW QUESTION 18
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enable which path is handling the traffic?
- A. Slow Path
- B. Medium Path
- C. Fast Path
- D. Accelerated Path
Answer: A
NEW QUESTION 19
What is the purpose of the CPCA process?
- A. Monitoring the status of processes
- B. Sending and receiving logs
- C. Communication between GUI clients and the SmartCenter server
- D. Generating and modifying certificates
Answer: D
NEW QUESTION 20
......
Recommend!! Get the Full 156-215.81 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/156-215.81-pdf-download.html (New 340 Q&As Version)