★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW 156-215.81 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/156-215.81-dumps.html
Exam Code: 156-215.81 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Check Point Certified Security Administrator R81
Certification Provider: CheckPoint
Free Today! Guaranteed Training- Pass 156-215.81 Exam.
Online 156-215.81 free questions and answers of New Version:
NEW QUESTION 1
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ________ .
- A. Captive Portal and Transparent Kerberos Authentication
- B. UserCheck
- C. User Directory
- D. Captive Portal
Answer: A
Explanation:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_IdentityAwareness_AdminGuide/T
NEW QUESTION 2
Which option, when applied to a rule, allows traffic to VPN gateways in specific VPN communities?
- A. All Connections (Clear or Encrypted)
- B. Accept all encrypted traffic
- C. Specific VPN Communities
- D. All Site-to-Site VPN Communities
Answer: B
Explanation:
The first rule is the automatic rule for the Accept All Encrypted Traffic feature. The Firewalls for the Security Gateways in the BranchOffices and LondonOffices VPN communities allow all VPN traffic from hosts in clients in these communities. Traffic to the Security Gateways is dropped. This rule is installed on all Security Gateways in these communities.
* 2. Site to site VPN - Connections between hosts in the VPN domains of all Site to Site VPN communities are allowed. These are the only protocols that are allowed: FTP, HTTP, HTTPS and SMTP.
* 3. Remote access - Connections between hosts in the VPN domains of RemoteAccess VPN community are allowed. These are the only protocols that are allowed: HTTP, HTTPS, and IMAP.
NEW QUESTION 3
Fill in the blanks: Default port numbers for an LDAP server is ________ for standard connections and _______ SSL connections.
- A. 675, 389
- B. 389, 636
- C. 636, 290
- D. 290, 675
Answer: B
Explanation:
A client starts an LDAP session by connecting to an LDAP server, called a Directory System Agent (DSA), by default on TCP and UDP port 389, or on port 636 for LDAPS. Global Catalog is available by default on ports 3268, and 3269 for LDAPS.
NEW QUESTION 4
Fill in the blanks: The Application Layer Firewalls inspect traffic through ______ the layer(s) of the TCP/IP model and up to and including the ______ layer.
- A. Upper; Application
- B. First two; Internet
- C. Lower; Application
- D. First two; Transport
Answer: C
Explanation:
application firewalls, or application layer firewalls, use a series of configured policies to determine whether to block or allow communications to or from an app.
NEW QUESTION 5
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.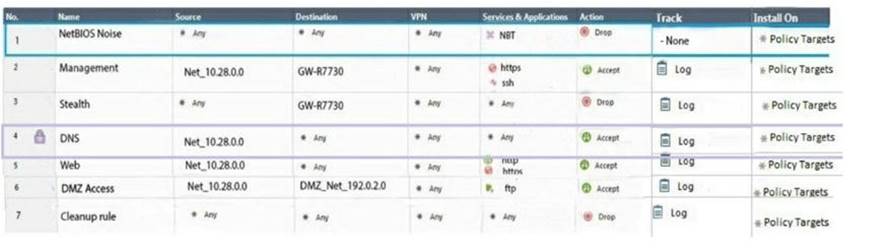
What is the possible explanation for this?
- A. DNS Rule is using one of the new feature of R80 where an administrator can mark a rule with the padlock icon to let other administrators know it is important.
- B. Another administrator is logged into the Management and currently editing the DNS Rule.
- C. DNS Rule is a placeholder rule for a rule that existed in the past but was deleted.
- D. This is normal behavior in R80 when there are duplicate rules in the Rule Base.
Answer: B
NEW QUESTION 6
Security Gateway software blades must be attached to what?
- A. Security Gateway
- B. Security Gateway container
- C. Management server
- D. Management container
Answer: B
Explanation:
Security Management and Security Gateway Software Blades must be attached to a Software Container to be licensed. https://downloads.checkpoint.com/dc/download.htm?ID=11608
NEW QUESTION 7
What is UserCheck?
- A. Messaging tool user to verify a user’s credentials
- B. Communication tool used to inform a user about a website or application they are trying to access
- C. Administrator tool used to monitor users on their network
- D. Communication tool used to notify an administrator when a new user is created
Answer: B
Explanation:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_NextGenSecurityGateway_Guide/T
NEW QUESTION 8
What is the main difference between Static NAT and Hide NAT?
- A. Static NAT only allows incoming connections to protect your network.
- B. Static NAT allow incoming and outgoing connection
- C. Hide NAT only allows outgoing connections.
- D. Static NAT only allows outgoing connection
- E. Hide NAT allows incoming and outgoing connections.
- F. Hide NAT only allows incoming connections to protect your network.
Answer: B
Explanation:
Hide NAT only translates the source address to hide it behind a gateway.
NEW QUESTION 9
Choose what BEST describes the reason why querying logs now is very fast.
- A. New Smart-1 appliances double the physical memory install
- B. Indexing Engine indexes logs for faster search results
- C. SmartConsole now queries results directly from the Security Gateway
- D. The amount of logs been store is less than the usual in older versions
Answer: B
Explanation:
Ref: https://sc1.checkpoint.com/documents/R80.40/WebAdminGuides/EN/CP_R80.40_LoggingAndMonitoring_Ad
NEW QUESTION 10
In SmartConsole, on which tab are Permissions and Administrators defined?
- A. Manage and Settings
- B. Logs and Monitor
- C. Security Policies
- D. Gateways and Servers
Answer: A
NEW QUESTION 11
What protocol is specifically used for clustered environments?
- A. Clustered Protocol
- B. Synchronized Cluster Protocol
- C. Control Cluster Protocol
- D. Cluster Control Protocol
Answer: D
NEW QUESTION 12
When installing a dedicated R80 SmartEvent server, what is the recommended size of the root partition?
- A. Any size
- B. Less than 20GB
- C. More than 10GB and less than 20 GB
- D. At least 20GB
Answer: D
NEW QUESTION 13
When dealing with rule base layers, what two layer types can be utilized?
- A. Ordered Layers and Inline Layers
- B. Inbound Layers and Outbound Layers
- C. R81.10 does not support Layers
- D. Structured Layers and Overlap Layers
Answer: A
Explanation:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_SecurityManagement_AdminGuide
NEW QUESTION 14
What key is used to save the current CPView page in a filename format cpview_“cpview process ID”. cap”number of captures”?
- A. S
- B. W
- C. C
- D. Space bar
Answer: C
NEW QUESTION 15
To provide updated malicious data signatures to all Threat Prevention blades, the Threat Prevention gateway does what with the data?
- A. Cache the data to speed up its own function.
- B. Share the data to the ThreatCloud for use by other Threat Prevention blades.
- C. Log the traffic for Administrator viewing.
- D. Delete the data to ensure an analysis of the data is done each time.
Answer: B
Explanation:
Data from malicious attacks are shared between the Threat Prevention Software Blades and help to keep your network safe. For example, the signatures from threats that Threat Emulation identifies are added to the ThreatCloud for use by the other Threat Prevention blades. src
https://infosec.co.il/wp-content/uploads/2020/06/12-GAiA-R80.40-Threat-Prevention.pdf page 28.
NEW QUESTION 16
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
- A. SmartManager
- B. SmartConsole
- C. Security Gateway
- D. Security Management Server
Answer: D
NEW QUESTION 17
What is the SOLR database for?
- A. Used for full text search and enables powerful matching capabilities
- B. Writes data to the database and full text search
- C. Serves GUI responsible to transfer request to the DLE server
- D. Enables powerful matching capabilities and writes data to the database
Answer: A
NEW QUESTION 18
Which back up method uses the command line to create an image of the OS?
- A. System backup
- B. Save Configuration
- C. Migrate
- D. snapshot
Answer: D
NEW QUESTION 19
A SAM rule Is implemented to provide what function or benefit?
- A. Allow security audits.
- B. Handle traffic as defined in the policy.
- C. Monitor sequence activity.
- D. Block suspicious activity.
Answer: D
Explanation:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_LoggingAndMonitoring_AdminGu
NEW QUESTION 20
......
P.S. Easily pass 156-215.81 Exam with 340 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared 156-215.81 Dumps: https://www.certshared.com/exam/156-215.81/ (340 New Questions)