★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW JN0-1332 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/JN0-1332-dumps.html
Act now and download your Juniper JN0-1332 test today! Do not waste time for the worthless Juniper JN0-1332 tutorials. Download Abreast of the times Juniper Security Design. Specialist (JNCDS-SEC) exam with real questions and answers and begin to learn Juniper JN0-1332 with a classic professional.
Also have JN0-1332 free dumps questions for you:
NEW QUESTION 1
Physical security devices are ''blind'' to which type of traffic?
- A. bare metal server to VM
- B. private VLAN
- C. intra-server traffic
- D. management
Answer: B
NEW QUESTION 2
Multiple customers use the shared infrastructure of your data center. These customers require isolation for compliance and security reasons.
What would you do to satisfy this requirement?
- A. Isolate each customer by using different physical hard//are
- B. Deploy multiple physical security control points
- C. Deploy a single logical security control point.
- D. Place each customers VLANs separate virtual router
Answer: C
NEW QUESTION 3
You are designing a security solution that includes SRX Series firewalls in a chassis cluster. In this scenario. which two dements must be part of the design? (Choose two.)
- A. The physical interface on each SRX Series device making up the reth interface must be in the same L2 domain
- B. The physical interface on each SRX Series device making up the reth interface must be in separate L2 domains
- C. The duster ID must be the same on both SRX Series devices
- D. The node 10 must be the same on both SRX Series devices
Answer: B
NEW QUESTION 4
A new virus is sheading across the Internet, with the potential to affect your customer's network
Which two statements describe how Policy Enforcer interacts with other devices to ensure that the network is protected in this scenario? (Choose two.)
- A. Policy Enforcer pulls security intelligence feeds from Juniper ATP Cloud to apply to SRX Series devices
- B. Policy Enforcer pulls security policies from Juniper ATP cloud and apples them to SRX Series devices
- C. Policy Enforcer automates the enrollment of SRX Series devices with Jumper ATP Cloud
- D. Security Director pulls security intelligence feeds from Juniper ATP Cloud and applies them to Policy Enforcer
Answer: B
NEW QUESTION 5
You are a security architect for a small managed service provider. The marketing team has proposed providing firewall services to the customers.
The requirements for the solution are shown below
-- The customer must be able 10 manage their own security device.
-- You must provide segmentation using Layer 2 and Layer 3.
-- You need to implement dynamic routing
-- You need to provide UTM services
in this scenario. which product would you select to provide the firewall services?
- A. cSRX
- B. vSRX
- C. vMX
- D. vQFX
Answer: D
NEW QUESTION 6
You want to reduce the possibility of your data center's server becoming an unwilling participant in a DDoS attack When tvA3 features should you use on your SRX Series devices to satisfy this requirement? (Choose two.)
- A. dynamic IPsec tunnels
- B. Juniper ATP Cloud GeolP
- C. UTMWebtaering
- D. Juniper ATP Cloud CC feeds
Answer: AD
NEW QUESTION 7
Which firewall service is used as a first line of defense and often used by a security device to protect itself?
- A. intrusion prevention system
- B. unified Threat management
- C. network address translation
- D. stateless firewall filter
Answer: A
NEW QUESTION 8
You are asked to perform a risk assessment for a core layer switch in your data center. After analyze the Annual loss Expectancy (ALE) for this switch, you conclude that the risk remediation strategy involves purchasing insurance to protect against losses due to compromise or failure.
This scenario describes which risk remediation strategy?
- A. risk transfer
- B. risk mitigation
- C. risk avoidance
- D. risk acceptance
Answer: D
NEW QUESTION 9
You are designing an IP camera solution for your warehouse You must block command and control servers from communicating with the cameras. In this scenario. which two products would you need to include in your design? (Choose two)
- A. SRX Series device
- B. Security Director
- C. Juniper ATP Cloud
- D. IPS
Answer: CD
NEW QUESTION 10
You are asked to recommend a client remote access solution that provides direct network access and is the most secure When connection type accomplishes this task?
- A. GRE
- B. SSH
- C. PPTP
- D. IPsec
Answer: B
NEW QUESTION 11
You must implement a solution to deploy end-to-end security services on network elements. Which solution will accomplish this task?
- A. Security Director
- B. Network Director
- C. JSA
- D. SRX Series devices
Answer: C
NEW QUESTION 12
You are asked to segment the networks connected to an SRX Series device into distinct logical groups with different security requirements.
How would you accomplish this task?
- A. Define different NAT policies for each network segment.
- B. Define different security policies for each network segment.
- C. Define different intrusion prevention policies for each network segment.
- D. Define different security zones for each network segment
Answer: B
NEW QUESTION 13
Refer to the exhibit.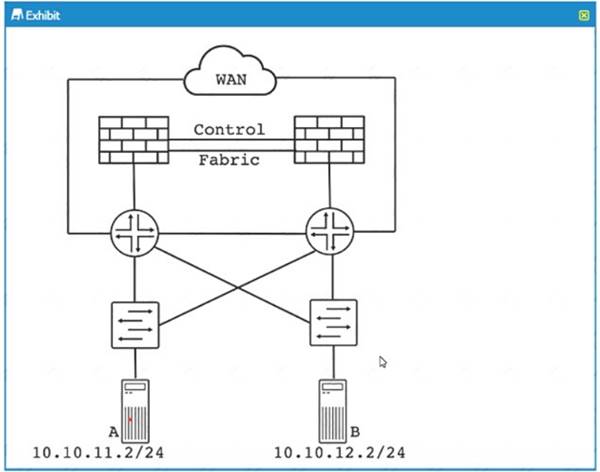
The SRX Series devices are decoyed in an off-path active/passive Cluster configuration
What are two advantages of this deployment model over an active-'active duster configuration' (Choose two)
- A. load-balancing of east/west traffic
- B. load-balancing of north/south traffic
- C. reduced latency
- D. reduced fabric link traffic
Answer: CD
NEW QUESTION 14
As part of your service provider WAN network design, you are asked to create a design that secures BGP communication .
In this scenario, what are two reasons you would choose BGP Generated TTL Security Mechanism (GTSM)? (Choose two.)
- A. You have an automated method of rotating MD5 hashes on each router.
- B. All of your router BGP connections are point-to-multipoint.
- C. AlI of your router BGP connections are point-to-point
- D. You do not have an easy method of rotating MD5 hashes on each router
Answer: BD
NEW QUESTION 15
What are two reasons for using a cSRX instance over a vSRX instance? (Choose two )
- A. cSRX instances launch faster than vSRX instances
- B. cSRX instances share the host OS unlike vSRX instances.
- C. A cSRX instance uses more memory but uses less disk space than a vSRX instance
- D. A cSRX instance supports more features than a vSRX instance
Answer: C
NEW QUESTION 16
Which feature is evaluated first when a packet is received on an interface of an SRX Series device?
- A. UTM
- B. ALG
- C. stateless firewall filter
- D. screens
Answer: A
NEW QUESTION 17
Which statement about Junos firewall filters is correct?
- A. Firewall filters can be applied as a security policy action
- B. Firewall filters do not operate on stateful flows and they serve no purpose in a next-generation firewall
- C. Firewall filters can be applied as the packet enters the security device, and they are stateless.
- D. Firewall filters are applied to TCP packets onl
- E. and they do not block UDP pockets
Answer: B
NEW QUESTION 18
Which two steps should be included in your security design process? (Choose two )
- A. Define an overall routing strategy
- B. identity external attackers
- C. Identify permitted communications
- D. Identify security requirements for the customer's organization
Answer: BC
NEW QUESTION 19
You are designing a service provider network. As part of your design you must ensure that the OSPF, BGP, and RSVP protocol communications are secured using the same authentication method. Which authentication protocol will accomplish this task?
- A. HMAC-MD5
- B. simple authentication
- C. SHA-RSA
- D. SHA-256
Answer: B
NEW QUESTION 20
......
Recommend!! Get the Full JN0-1332 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/JN0-1332-pdf-download.html (New 65 Q&As Version)