★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GSEC Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GSEC-dumps.html
Cause all that matters here is passing the GIAC GSEC exam. Cause all that you need is a high score of GSEC GIAC Security Essentials Certification exam. The only one thing you need to do is downloading Examcollection GSEC exam study guides now. We will not let you down with our money-back guarantee.
Free GSEC Demo Online For GIAC Certifitcation:
NEW QUESTION 1
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to change the startup shell of Maria from bash to tcsh. Which of the following commands will John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
- A. usermod -s
- B. chage
- C. usermod -u
- D. useradd -s
Answer: AD
NEW QUESTION 2
What is the name of the command-line tool for Windows that can be used to manage audit policies on remote systems?
- A. SECEDTT.EXE
- B. POLCLI.EXE
- C. REMOTEAUDIT.EXE
- D. AUDITPOL.EXE
Answer: D
NEW QUESTION 3
Your customer wants to make sure that only computers he has authorized can get on his Wi-Fi. What is the most appropriate security measure you can recommend?
- A. A firewall
- B. WPA encryption
- C. WEP encryption
- D. Mac filtering
Answer: D
NEW QUESTION 4
What type of attack can be performed against a wireless network using the tool Kismet?
- A. IP spoofing
- B. Eavesdropping
- C. Masquerading
- D. Denial of Service
Answer: B
NEW QUESTION 5
What is the main reason that DES is faster than RSA?
- A. DES is less secur
- B. DES is implemented in hardware and RSA is implemented in softwar
- C. Asymmetric cryptography is generally much faster than symmetri
- D. Symmetric cryptography is generally much faster than asymmetri
Answer: D
NEW QUESTION 6
Which of the following is referred to as Electromagnetic Interference (EMI)?
- A. Electrical line noise
- B. Spike
- C. Transient
- D. Brownout
Answer: A
NEW QUESTION 7
Which of the following works at the network layer and hides the local area network IP address and topology?
- A. Network address translation (NAT)
- B. Hub
- C. MAC address
- D. Network interface card (NIC)
Answer: A
NEW QUESTION 8
Your software developer comes to you with an application that controls a user device. The application monitors its own behavior and that of the device and creates log files. The log files are expected to grow steadily and rapidly. Your developer currently has the log files stored in the /bin folder with the application binary. Where would you suggest that the developer store the log files?
- A. /var/log
- B. /etc/log
- C. /usr/log
- D. /tmp/log
- E. /dev/log
Answer: A
NEW QUESTION 9
What type of malware is a self-contained program that has the ability to copy itself without parasitically infecting other host code?
- A. Trojans
- B. Boot infectors
- C. Viruses
- D. Worms
Answer: D
NEW QUESTION 10
In addition to securing the operating system of production honey pot hosts, what is recommended to prevent the honey pots from assuming the identities of production systems that could result in the denial of service for legitimate users?
- A. Deploy the honey pot hosts as physically close as possible to production system
- B. Deploy the honey pot hosts in an unused part of your address spac
- C. Deploy the honey pot hosts to only respond to attack
- D. Deploy the honey pot hosts on used address spac
Answer: B
NEW QUESTION 11
Analyze the screenshot below. What is the purpose of this message?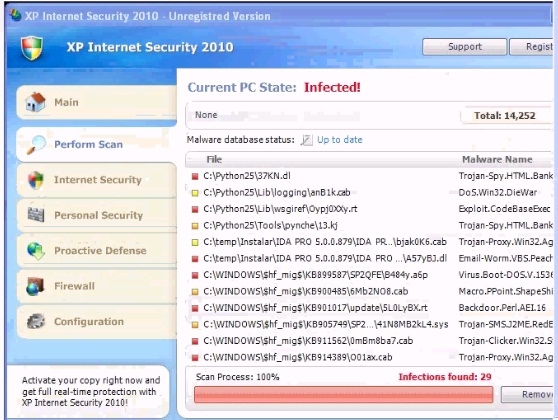
- A. To gather non-specific vulnerability information
- B. To get the user to download malicious software
- C. To test the browser plugins for compatibility
- D. To alert the user to infected software on the compute
Answer: D
NEW QUESTION 12
Which type of risk assessment results are typically categorized as low, medium, or high-risk events?
- A. Technical
- B. Qualitative
- C. Management
- D. Quantitative
Answer: B
NEW QUESTION 13
Which of the following are the types of intrusion detection systems?
Each correct answer represents a complete solution. Choose all that apply.
- A. Host-based intrusion detection system (HIDS)
- B. Client-based intrusion detection system (CIDS)
- C. Server-based intrusion detection system (SIDS)
- D. Network intrusion detection system (NIDS)
Answer: AD
NEW QUESTION 14
Why would someone use port 80 for deployment of unauthorized services?
- A. Google will detect the service listing on port 80 and post a link, so that people all over the world will surf to the rogue servic
- B. If someone were to randomly browse to the rogue port 80 service they could be compromise
- C. This is a technique commonly used to perform a denial of service on the local web serve
- D. HTTP traffic is usually allowed outbound to port 80 through the firewall in most environment
Answer: D
NEW QUESTION 15
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 domain- based network. The network contains ten Windows 2003 member servers, 150 Windows XP Professional client computers. According to the company's security policy, Mark needs to check whether all the computers in the network have all available security updates and shared folders. He also needs to check the file system type on each computer's hard disk. Mark installs and runs MBSACLI.EXE with the appropriate switches on a server. Which of the following tasks will he accomplish?
- A. None of the tasks will be accomplishe
- B. He will be able to check the file system type on each computer's hard dis
- C. He will be able to accomplish all the task
- D. He will be able to check all available security updates and shared folder
Answer: C
NEW QUESTION 16
CORRECT TEXT
Fill in the blank with the correct answer to complete the statement below.
The permission is the minimum required permission that is necessary for a user to enter a directory and list its contents.
- A.
Answer: Read
NEW QUESTION 17
Which of the following ports is the default port for Layer 2 Tunneling Protocol (L2TP)?
- A. TCP port 443
- B. UDP port 161
- C. TCP port 110
- D. UDP port 1701
Answer: D
NEW QUESTION 18
Which of the following classes of fire comes under Class C fire?
- A. Paper or wood fire
- B. Oil fire
- C. Combustible metals fire
- D. Electronic or computer fire
Answer: D
NEW QUESTION 19
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. You have configured a firewall on the network. A filter has been applied to block all the ports. You want to enable sending and receiving of emails on the network. Which of the following ports will you open?
Each correct answer represents a complete solution. Choose two.
- A. 80
- B. 25
- C. 20
- D. 110
Answer: BD
NEW QUESTION 20
......
P.S. Easily pass GSEC Exam with 279 Q&As Allfreedumps.com Dumps & pdf Version, Welcome to Download the Newest Allfreedumps.com GSEC Dumps: https://www.allfreedumps.com/GSEC-dumps.html (279 New Questions)