★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW 312-38 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/312-38-dumps.html
we provide Downloadable EC-Council 312-38 answers which are the best for clearing 312-38 test, and to get certified by EC-Council EC-Council Network Security Administrator (ENSA). The 312-38 Questions & Answers covers all the knowledge points of the real 312-38 exam. Crack your EC-Council 312-38 Exam with latest dumps, guaranteed!
EC-Council 312-38 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Identify the correct statements regarding a DMZ zone:
- A. It is a file integrity monitoring mechanism
- B. It is a Neutral zone between a trusted network and an untrusted network
- C. It serves as a proxy
- D. It includes sensitive internal servers such as database servers
Answer: B
NEW QUESTION 2
John has successfully remediated the vulnerability of an internal application that could have caused a threat to the network. He is scanning the application for the existence of a remediated vulnerability, this process is called a _______ and it has to adhere to the ________
- A. Verification, Security Policies
- B. Mitigation, Security policies
- C. Vulnerability scanning, Risk Analysis
- D. Risk analysis, Risk matrix
Answer: A
NEW QUESTION 3
Dan and Alex are business partners working together. Their Business-Partner Policy states that they should encrypt their emails before sending to each other. How will they ensure the authenticity of their emails?
- A. Dan will use his public key to encrypt his mails while Alex will use Dan's digital signature to verify the authenticity of the mails.
- B. Dan will use his private key to encrypt his mails while Alex will use his digital signature to verify the authenticity of the mails.
- C. Dan will use his digital signature to sign his mails while Alex will use his private key to verify the authenticity of the mails.
- D. Dan will use his digital signature to sign his mails while Alex will use Dan's public key to verify the authencity of the mails.
Answer: D
NEW QUESTION 4
An attacker uses different types of password cracking techniques to crack the password and gain unauthorized access to a system. An attacker uses a file containing a list of commonly used passwords. They then upload this file into the cracking application that runs against the user accounts. Which of the following password cracking techniques is the attacker trying?
- A. Bruteforce
- B. Rainbow table
- C. Hybrid
- D. Dictionary
Answer: D
NEW QUESTION 5
Kyle, a front office executive, suspects that a Trojan has infected his computer. What should be his first course of action to deal with the incident?
- A. Contain the damage
- B. Disconnect the five infected devices from the network
- C. Inform the IRT about the incident and wait for their response
- D. Inform everybody in the organization about the attack
Answer: C
NEW QUESTION 6
As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2's _____ integrity check mechanism provides security against a replay attack
- A. CBC-32
- B. CRC-MAC
- C. CRC-32
- D. CBC-MAC
Answer: D
NEW QUESTION 7
An administrator wants to monitor and inspect large amounts of traffic and detect unauthorized attempts from inside the organization, with the help of an IDS. They are not able to
recognize the exact location to deploy the IDS sensor. Can you help him spot the location where the IDS sensor should be placed?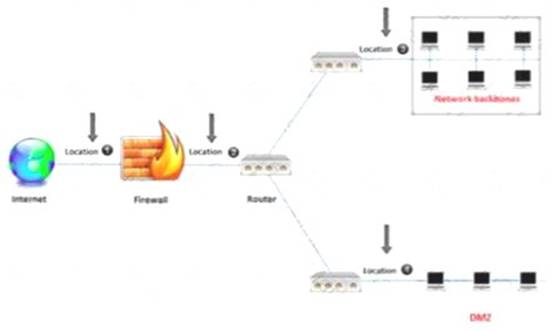
- A. Location 2
- B. Location 3
- C. Location 4
- D. Location 1
Answer: A
NEW QUESTION 8
Kyle is an IT technician managing 25 workstations and 4 servers. The servers run applications and mostly store confidential data. Kyle must backup the server's data daily to ensure nothing is lost. The power in the company's office is not always reliable, Kyle needs to make sure the servers do not go down or are without power for too long. Kyle decides to purchase an Uninterruptible Power Supply (UPS) that has a pair of inverters and converters to charge the battery and provides power when needed. What type of UPS has Kyle purchased?
- A. Kyle purchased a Ferro resonant Standby UPS.
- B. Kyle purchased a Line-Interactive UPS
- C. He has bought a Standby UPS
- D. He purchased a True Online UPS.
Answer: C
NEW QUESTION 9
Which VPN QoS model guarantees the traffic from one customer edge (CE) to another?
- A. Pipe Model
- B. AAA model
- C. Hub-and-Spoke VPN model
- D. Hose mode
Answer: A
NEW QUESTION 10
Fred is a network technician working for Johnson Services, a temporary employment agency in Boston. Johnson Services has three remote offices in New England and the headquarters in Boston where Fred works.
The company relies on a number of customized applications to perform daily tasks and unfortunately these applications require users to be local administrators. Because of this, Fred's supervisor wants to implement
tighter security measures in other areas to compensate for the inherent risks in making those users local admins. Fred's boss wants a solution that will be placed on all computers throughout the company and
monitored by Fred. This solution will gather information on all network traffic to and from the local computers without actually affecting the traffic. What type of solution does Fred's boss want to implement?
- A. Fred's boss wants a NIDS implementation.
- B. Fred's boss wants Fred to monitor a NIPS system.
- C. Fred's boss wants to implement a HIPS solution.
- D. Fred's boss wants to implement a HIDS solution.
Answer: D
NEW QUESTION 11
Which of the following network monitoring techniques requires extra monitoring software or hardware?
- A. Non-router based
- B. Switch based
- C. Hub based
- D. Router based
Answer: A
NEW QUESTION 12
Harry has successfully completed the vulnerability scanning process and found serious vulnerabilities exist in the organization's network. Identify the vulnerability management phases through which he will proceed to ensure all the detected vulnerabilities are addressed and eradicated. (Select all that apply)
- A. Mitigation
- B. Assessment
- C. Verification
- D. Remediation
Answer: ACD
NEW QUESTION 13
Heather has been tasked with setting up and implementing VPN tunnels to remote offices. She will most likely be implementing IPsec VPN tunnels to connect the offices. At what layer of the OSI model does an IPsec tunnel function on?
- A. They work on the session layer.
- B. They function on either the application or the physical layer.
- C. They function on the data link layer
- D. They work on the network layer
Answer: D
NEW QUESTION 14
Justine has been tasked by her supervisor to ensure that the company's physical security is on the same level as their logical security measures. She installs video cameras at all entrances and exits and installs badge access points for all doors. The last item she wants to install is a method to prevent unauthorized people piggybacking employees. What should she install to prevent piggybacking?
- A. She should install a mantrap
- B. Justine needs to install a biometrics station at each entrance
- C. Justine will need to install a revolving security door
- D. She should install a Thompson Trapdoor.
Answer: A
NEW QUESTION 15
Identify the password cracking attempt involving precomputed hash values stored as plaintext and using these to crack the password.
- A. Bruteforce
- B. Rainbow table
- C. Dictionary
- D. Hybrid
Answer: B
NEW QUESTION 16
Nancy is working as a network administrator for a small company. Management wants to implement a RAID storage for their organization. They want to use the appropriate RAID level for their backup plan that will satisfy the following requirements: 1. It has a parity check to store all the information about the data in multiple drives 2. Help reconstruct the data during downtime. 3. Process the data at a good speed. 4. Should not be expensive. The management team asks Nancy to research and suggest the appropriate RAID level that best suits their requirements. What RAID level will she suggest?
- A. RAID 0
- B. RAID 10
- C. RAID 3
- D. RAID 1
Answer: C
NEW QUESTION 17
A network is setup using an IP address range of 0.0.0.0 to 127.255.255.255. The network has a default subnet mask of 255.0.0.0. What IP address class is the network range a part of?
- A. Class C
- B. Class A
- C. Class B
- D. Class D
Answer: B
NEW QUESTION 18
The agency Jacob works for stores and transmits vast amounts of sensitive government data that cannot be compromised. Jacob has implemented Encapsulating Security Payload (ESP) to encrypt IP traffic. Jacob wants to encrypt the IP traffic by inserting the ESP header in the IP datagram before the transport layer protocol header. What mode of ESP does Jacob need to use to encrypt the IP traffic?
- A. He should use ESP in transport mode.
- B. Jacob should utilize ESP in tunnel mode.
- C. Jacob should use ESP in pass-through mode.
- D. He should use ESP in gateway mode
Answer: B
NEW QUESTION 19
James wants to implement certain control measures to prevent denial-of-service attacks against the organization. Which of the following control measures can help James?
- A. Strong passwords
- B. Reduce the sessions time-out duration for the connection attempts
- C. A honeypot in DMZ
- D. Provide network-based anti-virus
Answer: B
NEW QUESTION 20
......
100% Valid and Newest Version 312-38 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/312-38-dumps.html (New 177 Q&As)