★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW 156-915.77 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/156-915.77-dumps.html
Certleader offers free demo for 156-915.77 exam. "Check Point Certified Security Expert Update Blade", also known as 156-915.77 exam, is a CheckPoint Certification. This set of posts, Passing the CheckPoint 156-915.77 exam, will help you answer those questions. The 156-915.77 Questions & Answers covers all the knowledge points of the real exam. 100% real CheckPoint 156-915.77 exams and revised by experts!
Online CheckPoint 156-915.77 free dumps demo Below:
NEW QUESTION 1
Your customer, Mr. Smith needs access to other networks and should be able to use all services. Session authentication is not suitable. You select Client Authentication with HTTP. The standard authentication port for client HTTP authentication (Port 900) is already in use. You want to use Port 9001 but are having connectivity problems. Why are you having problems?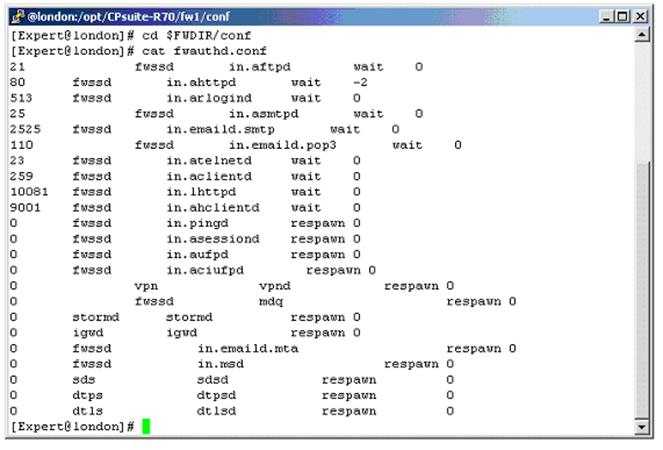
- A. The configuration file $FWDIR/conf/fwauthd.conf is incorrect.
- B. The Security Policy is not correct.
- C. You can't use any port other than the standard port 900 for Client Authentication via HTTP.
- D. The service FW_clntauth_http configuration is incorrect.
Answer: A
NEW QUESTION 2
You are running a R77 Security Gateway on GAiA. In case of a hardware failure, you have a server with the exact same hardware and firewall version installed. What back up method could be used to quickly put the secondary firewall into production?
- A. manual backup
- B. upgrade_export
- C. backup
- D. snapshot
Answer: D
NEW QUESTION 3
You are responsible for the configuration of MegaCorp’s Check Point Firewall. You need to allow two NAT rules to match a connection. Is it possible? Give the BEST answer.
- A. No, it is not possible to have more than one NAT rule matching a connectio
- B. When the firewall receives a packet belonging to a connection, it compares it against the first rule in the Rule Base, then the second rule, and so o
- C. When it finds a rule that matches, it stops checking and applies that rule.
- D. Yes, it is possible to have two NAT rules which match a connection, but only in using Manual NAT (bidirectional NAT).
- E. Yes, there are always as many active NAT rules as there are connections.
- F. Yes, it is possible to have two NAT rules which match a connection, but only when using Automatic NAT (bidirectional NAT).
Answer: D
NEW QUESTION 4
When restoring R77 using the command upgrade_import, which of the following items are NOT restored?
- A. SIC Certificates
- B. Licenses
- C. Route tables
- D. Global properties
Answer: C
NEW QUESTION 5
CORRECT TEXT
Type the command and syntax you would use to verify that your Check Point cluster is functioning correctly.
Solution:
cphaprob state
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network
destinations. Select accept as the Action.
Ms. McHanry tries to access the resource but is unable. What should she do?
- A. Have the security administrator select the Action field of the Firewall Rule “Redirect HTTP connections to an authentication (captive) portal”
- B. Have the security administrator reboot the firewall
- C. Have the security administrator select Any for the Machines tab in the appropriate Access Role
- D. Install the Identity Awareness agent on her iPad
Answer: A
NEW QUESTION 7
What is the primary benefit of using the command upgrade_export over either backup or snapshot?
- A. upgrade_export is operating system independent and can be used when backup or snapshot is not available.
- B. upgrade_export will back up routing tables, hosts files, and manual ARP configurations, where backup and snapshot will not.
- C. The commands backup and snapshot can take a long time to run whereas upgrade_export will take a much shorter amount of time.
- D. upgrade_export has an option to back up the system and SmartView Tracker logs while backup and snapshot will not.
Answer: A
NEW QUESTION 8
Before upgrading SecurePlatform to GAiA, you should create a backup. To save time, many administrators use the command backup. This creates a backup of the Check Point configuration as well as the system configuration.
An administrator has installed the latest HFA on the system for fixing traffic problem after creating a backup file. There is a mistake in the very complex static routing configuration. The Check Point configuration has not been changed. Can the administrator use a restore to fix the errors in static routing?
- A. The restore is not possible because the backup file does not have the same build number (version).
- B. The restore is done by selecting Snapshot Management from the boot menu of GAiA.
- C. The restore can be done easily by the command restore and copying netconf.C from the production environment.
- D. A backup cannot be restored, because the binary files are missing.
Answer: C
NEW QUESTION 9
Reboot both gateways.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
CORRECT TEXT
Fill in the blank. The user wants to replace a failed Windows-based firewall with a new server running GAiA. For the most complete restore of an GAiA configuration, he or she will use the command
Solution:
migrate_import
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities should you do first?
- A. Exchange exported CA keys and use them to create a new server object to represent your partner’s Certificate Authority (CA).
- B. Create a new logical-server object to represent your partner’s CA.
- C. Manually import your partner’s Access Control List.
- D. Manually import your partner’s Certificate Revocation List.
Answer: A
NEW QUESTION 12
Which command will erase all CRL’s?
- A. vpn crladmin
- B. cpstop/cpstart
- C. vpn crl_zap
- D. vpn flush
Answer: C
NEW QUESTION 13
What command with appropriate switches would you use to test Identity Awareness connectivity?
- A. test_ldap
- B. test_ad_connectivity
- C. test_ldap_connectivity
- D. test_ad
Answer: B
NEW QUESTION 14
CORRECT TEXT
Type the command and syntax to view critical devices on a cluster member in a ClusterXL environment.
Solution:
cphaprob -ia list
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
A host on the Internet initiates traffic to the Static NAT IP of your Web server behind the Security Gateway. With the default settings in place for NAT, the initiating packet will translate the .
- A. destination on server side
- B. source on server side
- C. source on client side
- D. destination on client side
Answer: D
NEW QUESTION 16
......
P.S. Dumps-hub.com now are offering 100% pass ensure 156-915.77 dumps! All 156-915.77 exam questions have been updated with correct answers: https://www.dumps-hub.com/156-915.77-dumps.html (203 New Questions)