★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW 101 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/101-dumps.html
Want to know Passleader 101 Exam practice test features? Want to lear more about F5-Networks Application Delivery Fundamentals certification experience? Study High value F5-Networks 101 answers to Latest 101 questions at Passleader. Gat a success with an absolute guarantee to pass F5-Networks 101 (Application Delivery Fundamentals) test on your first attempt.
Online 101 free questions and answers of New Version:
NEW QUESTION 1
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named LACP01) connected to the BIG IP device, Multiple other VLANs exist on LACP01.Which TMSH command should the BIG IP Administrator issue to add the new VLAN lo the existing LAC?
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named IACP01) connected to the BIG IP device Multiple other VLANs exist on LACP01. Which TMSH command should the BIG IP Administrator issue to add the new VLAN to the existing LAC?
- A. create net vlan VIAN40 (interfaces replace all with {LACP01 (untagged } } lag 40 )
- B. create net vian VLAN40 (interfaces add { LACP01 {tagged} tag JO J
- C. create net vian VLAN40 {interfaces add ( LACP01 {untagged)) tag 40}
- D. create net wan VLAN40 {interfaces replace all with {LACP01 {tagged ]} lag 40 }
Answer: B
Explanation:
Tagged" VLAN is how F5 refers to a VIAN within an 802.1q trunk. The fact that it is an FS trunk' or an LACP/etherchannel link only changeshowthe interface is referred to in the command.
NEW QUESTION 2
Which of the following would happen?
- A. The PC sends a DNS query for 172. 17. 10. 1
- B. The PC sends an ARP looking for the MAC address of 172. 17. 10. 4
- C. The PC sends an ARP looking for the MAC address of 172. 17. 10. 1
- D. The PC sends a DNS query for 172.17.10 4
Answer: B
NEW QUESTION 3
Which high availability feature allows two different BIG-IP devices to use the MAC address for the same server IP?
- A. HSRP virtual MAC address
- B. Device group
- C. Sync- failover
- D. MAC masquerade
Answer: D
NEW QUESTION 4
An organization needs to cryptographically sign its domains. Which F5 product provides this functionality?
- A. GTM
- B. LTM
- C. ASM
- D. APM
Answer: A
Explanation:
https //devcentral f5 com/articles/the-tNg-ip gtm-configuring-dnssec
NEW QUESTION 5
A client is transmitting a large amount of data to a server During this process, the server sets the window size to zero What is the likely cause of this issue?
- A. The server is unable to accept more data
- B. The server resets the connection
- C. The client runs out of network buffers
- D. The server reaches its maximum segment size
Answer: A
Explanation:
htlps://wiki wireshark orgn/TCP%20ZeroWindow
NEW QUESTION 6
A BIG-IP Administrator needs to create a route to send traffic destined to 10.1.1 1 to another router with an address of 192 168 1 1 Which TMSH command should the administrator use?
- A. create/net route 10. 11. 1/32 gw 192 168. 1. 1
- B. create met route 192 168. 1. 1/32 gw 10. 11. 1
- C. add met route 192. 168. 1. 1/32 gw 10. 1. 1. 1
- D. add inet route 10.11.1/32 gw 192. 168.1.1
Answer: A
NEW QUESTION 7
A company deploys F5 load balancers to manage number of secure applications. The company needs to centrally manage certificates.
Which F5 product provides this functionality?
- A. BIG IQ
- B. GTW
- C. iHeath
- D. LTM
Answer: A
NEW QUESTION 8
What is a benefit of configuring BIG-IP devicesin active-active high availabilitymode?
- A. avoid Overload on the BIG-P system in theevent of a failover
- B. allows full utilization of hardware purchased
- C. reduces troubleshooting complexity
- D. provides ability to upgrade a member of the pair without disruption
Answer: B
NEW QUESTION 9
in which scenario is a full proxy TCP connection required?
- A. when compression is actuated
- B. When Source NAT configured
- C. when a virtual server is configured
- D. When Source IP persistence is required
Answer: A
Explanation:
https//devcentral f5 com/articles/the-full-proxy-data-center-architecture
NEW QUESTION 10
A BIG-IP Administrator is cleaning up unused Virtual Servers and pools via the Configuration Utility while trying to delete certain administrator receives an error message that indicates that the pool is in use.
What is the likely cause of this error?
- A. The pool members are all disabled
- B. The pool is in use by a Virtual Server
- C. The pool members are marked up with a green circle
- D. The pool is in use by a monitor
Answer: B
NEW QUESTION 11
The BIG IP device is connected to the same network as a server
Which communication protocol will the BIG IP device use to discover the link layer address of the server?
- A. Ping
- B. ICMP
- C. RARP
- D. ARP
Answer: D
NEW QUESTION 12
HTTPs traffic is not working properly. What is the likely reason for the issue?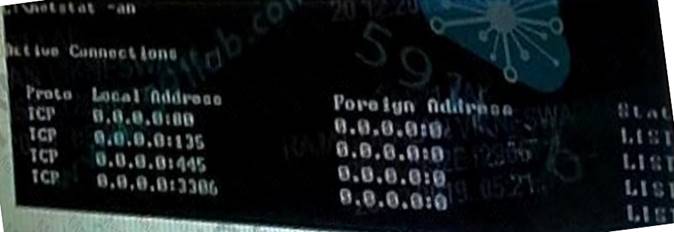
- A. 0. 0 0.0 0 is an invalid address in netstat.
- B. 0. 0. 0. 0.0 80 should be in an active stale
- C. The server is not listening on TCP 443
- D. The server is not listening on UDP 80
Answer: C
NEW QUESTION 13
BIG-IP Administrator performs the capture as shown in the image! On which protocol is the application responding?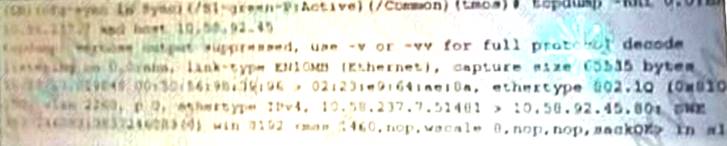
- A. RDP
- B. HTTPS
- C. DNS
- D. HTTP
Answer: D
NEW QUESTION 14
What we two advantages of using SSL offloading? (Choose two)
- A. Offloads the client to SSL processing
- B. provides single point of management for private keys
- C. reduces server load significantly
- D. encrypts all communications and to end
- E. allows secure remote access to internal server resources
Answer: BC
NEW QUESTION 15
The use of attack signature within an intrusion Detection System (IDS) is an application of which security model?
- A. Positive
- B. Context-based
- C. Negative
- D. Role-based
Answer: C
Explanation:
https //www.dosarrpst.com'ddos-blog/the-difference-between-positive-s-negatto-wafi
NEW QUESTION 16
The users in a company are unable to send and receive SMTP e-mails using the BIG-IP Virtual Server. The administrator logs into the BIG IP device to verify if the mail pool member with an IP address of 192. 168. 10. 100. 18 is serving SMTP traffic.
Which command on the BIG-IP device should the administrator use to verify the traffic?
- A. tcpdump - 0 0 host 192 168 10 100 and port 143
- B. curf - 1 smtp1/192 168 10 100
- C. Icpdurnp - 0:0 host 192. 168. 10. 100 and port 25
- D. telnet 192. 168. 10. 100. 143
Answer: C
NEW QUESTION 17
A server is operating on the network 10.100/24. The BIG-IP device is operating on the 192.168.0.0/24 net. What is required to enable the several and BIG-IP device to communicate properly?
- A. Firewall
- B. Switch
- C. Router
- D. Hub
Answer: C
NEW QUESTION 18
A BIG-P Administrator needs to upload a qkview view to evaluate software upgrade options. Which service should be used?
- A. AskF5
- B. iHeath
- C. DevCentral
- D. F5WedSubOon
Answer: B
NEW QUESTION 19
......
Recommend!! Get the Full 101 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/101-pdf-download.html (New 240 Q&As Version)